I’ve been struggling all morning (in truth, for the last several days) to describe the kaleidoscope of ways Trump is destroying rule of law.
It perhaps is best conveyed by a contrast between all the shit going on in Minnesota and what happened in Chicago yesterday.
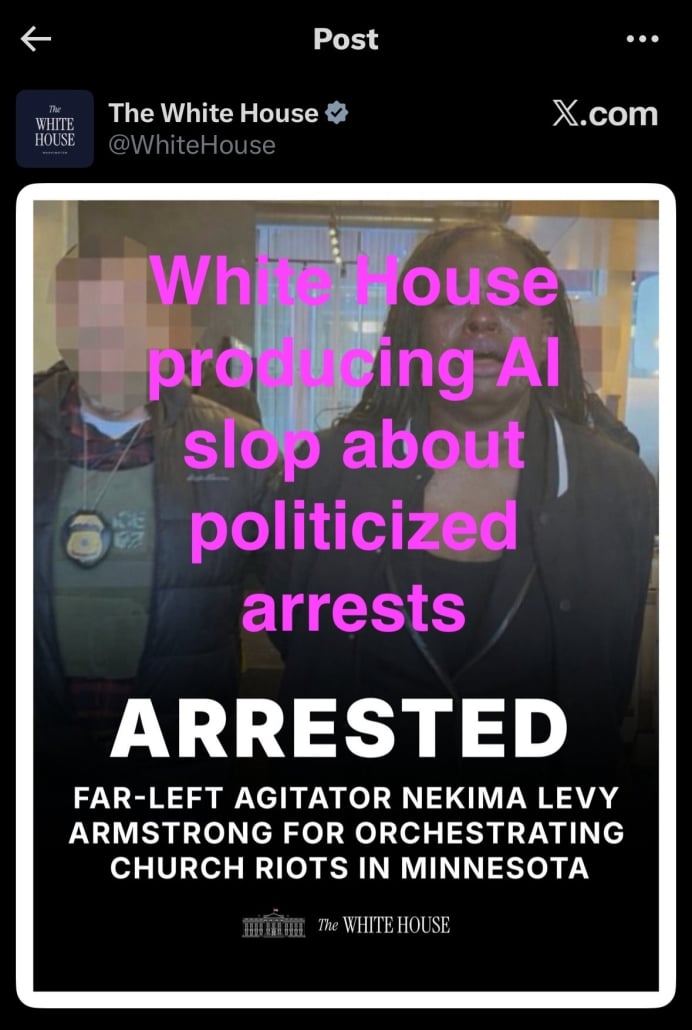
Pam Bondi personally went to Minnesota to secure arrests of people who protested the Southern Baptist Church whose minister, David Easterwood, also runs the local ICE department. When the FBI went to arrest one of them, Nekima Levy Armstrong, they arrested the wrong Black woman at first. Then the White House posted a meme of her, slopped up to make it look like she was crying, and falsely accusing her of rioting.
The AI slop will make it far easier for Levy to argue this is vindictive.
DOJ had tried to charge Don Lemon, but a Magistrate Judge refused to charge someone who was legitimately covering a protest. And now Lemon, who is represented by the omnipresent Abbe Lowell, is taunting Bondi.
The Magistrate also refused to approve FACE charges against those already arrested.
The arrest of the wrong Black woman was not the only case of mistaken identity in Trump’s invasion of Minnesota this week. It turns out that the out-of-state ICE goon who shot Venezuelan Julio Cesar Sosa-Celis thought he was chasing one guy, Joffre Barrera, who is 5’2″ and 128 pounds, but was instead chasing Alfredo Alejandro Aljorna, who is 5’7″ and 172 pounds.
Both have short brown hair.
Sosa-Celis and Aljorna might have a decent argument that they had no way of being sure the ICE goon they’re accused of assaulting was actually ICE. According to the arrest affidavit, the ICE goon who shot Sosa-Celis was not wearing anything that identified him as Police — his badge and gun were on a tactical belt. His buddy, who was wearing a tactical vest identifying him as police, was not yet present when the assault and shooting happened. And they were driving an unmarked vehicle. Except both defendants talked to the cops without an attorney and confessed to knowing the goons were ICE.
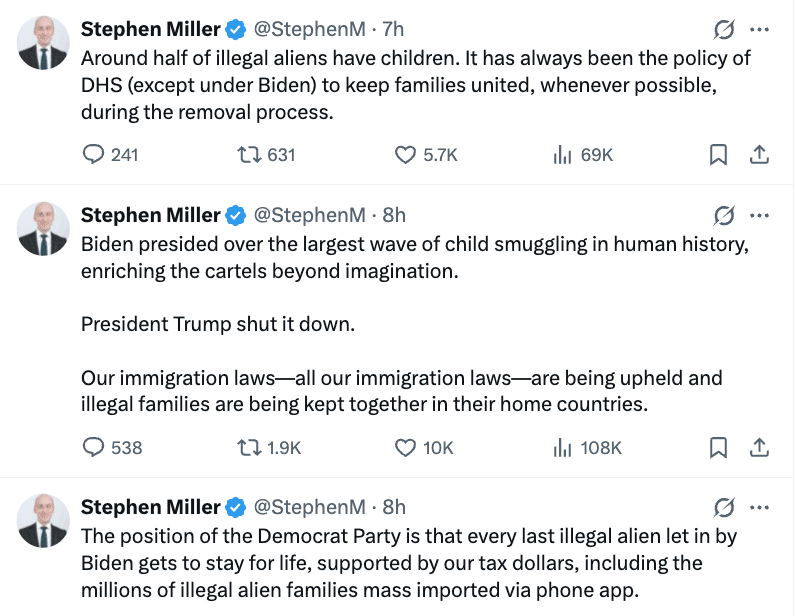
Meanwhile, the backlash surrounding the snatching and use as bait of five year old Liam Conejo Ramos has gotten so bad that Stephen Miller is openly defensive.
The problem for Miller is that, at least according to the attorney for Ramos’ family, they are in the US legally, seeking asylum.
Marc Prokosch, the family’s attorney, said they came to the U.S. in 2024 from Ecuador, had an active asylum case and the preschooler should never have been detained. He said the family was properly following immigration rules and [his father, Adrian] Conejo Arias had no criminal history.
The Ramoses are not the only ones. The local Fox affiliate describes that there have been more habeas petitions filed this year than the entirety of last year.
Immigration attorneys say they are filing habeas corpus petitions to secure the release of detainees at a “dizzying pace.”
The petitions are constitutionally protected challenges to the government’s arrest of an individual. However, the Trump Administration previously suggested suspending those rights.
In the context of immigration enforcement operations, the petitions ask federal judges to either release individuals from custody or grant them a bond hearing in immigration court.
By the numbers: According to case data reviewed by the FOX 9 Investigators, 312 immigrant detainees had sought habeas relief through Jan. 21.
The number of petitions filed in the district court of Minnesota in the first three weeks of the year has already surpassed the 260 filed in the entirety of 2025.
Meanwhile, Minnesota Public Radio tracked down the people on one of DHS’ “worst of the worst” lists — the people DHS falsely claimed to have snatched during this invasion. Most had been released into ICE custody before the recent invasion.
[M]ost of the people on the list had been immediately transferred to ICE custody at the end of time served in Minnesota prisons.
All of those transfers happened before ICE began its surge of operations in Minnesota on Dec. 1, 2025, with some even happening years before.
[snip]
[F]ive of those individuals were transferred from prison custody to ICE custody between August and late November. Three others were handed over to ICE custody by DOC during previous presidential administrations.
And one person was offered to be released to ICE custody more than a decade ago and ICE declined, according to the DOC.
[snip]
[O]ne was put on probation for 30 years and was never in DOC custody, and two were only ever in the custody of county jails and never in DOC custody.
One person on the list was convicted of crimes in Ohio, where it is unclear if they had an ICE detainer, which is a request to hold a prisoner for another agency. The Ohio Department of Rehabilitation and Correction did not respond for a request for information on the matter.
Click through for the list, including the guy released to ICE in 2012 — and share this widely.
Relatedly, Bulwark and a local ABC affiliate reports that the guy DHS claimed they were looking for when they snatched a senior Hmong-American in his underwear was already in prison.
Sometimes, the “worst of the worst” — the U.S. Department of Homeland Security’s catchphrase for undocumented immigrants with violent criminal records — are exactly where one would expect: prison.
That was the case for Lue Moua, a 52-year-old Laotian man who DHS officials say they were looking for when they instead arrested an elderly U.S. citizen last weekend.
The images of ChongLy Thao’s arrest by U.S. Immigration and Customs Enforcement in St. Paul sparked outrage in Minnesota and across the internet.
Several videos show Thao, a U.S. citizen, led out of his home in freezing weather, wearing nothing but his boxers, sandals and a blanket draped around him. Thao’s family alleges the agents did not present a warrant, nor did they ask Thao for identification. He was released shortly afterward.
In a statement explaining Thao’s detention, ICE officials say they were looking for two undocumented Laotian men with criminal records, Moua and Kongmeng Vang, who they say lived with Thao. They also said Thao matched the description of those men.
Family members said they had no knowledge of either and that Thao lived with his son, daughter-in-law and his young grandson.
So where are these men?
Moua, who has felony convictions dating back to 1992 of fifth-degree criminal sexual conduct, kidnapping, and violating a parental custody order, has been incarcerated at Minnesota Corrections Facility-Faribault since Sept. 4, 2024. His expected release date is Jan. 7, 2027.
It’s all bullshit, all the way down.
Contrast that effort to criminalize dissent in Minnesota and claim five year old boys are scary criminals with the most spectacular faceplant yet in Trump’s attempt to gin up criminal cases to justify Stephen Miller’s dragnet, the acquittal of Juan Espinoza Martinez, who was accused of attempting to pay for a hit on Greg Bovino. Jon Seidel describes how the case collapsed after DOJ conceded they could not prove that Martinez had ties to the Latin Kings.
The original criminal complaint cited a “source of information,” now known to be 44-year-old Adrian Jimenez, who called Espinoza Martinez a “ranking member of the Latin Kings.” A Homeland Security press release also called Espinoza Martinez a “Latin Kings gang member.”
But earlier this month, First Assistant U.S. Attorney Jason Yonan and Assistant U.S. Attorney Minje Shin acknowledged they would not try to prove Espinoza Martinez’s gang membership at trial.
That prompted Lefkow to bar gang evidence from the case. She wrote in an order that, “without evidence showing that [Espinoza Martinez] is a member of the Latin Kings or that the Latin Kings instructed [Espinoza Martinez] to send the alleged murder-for-hire information, the prejudicial nature of such testimony outweighs any probative value.”
In an emergency hearing hours after that ruling last week, Yonan told [Judge Joan] Lefkow that “nearly every piece of evidence in this case touches, in some fashion, on the Latin Kings.”
But the trial still kicked off. The feds called only three witnesses Wednesday, who testified over the course of nearly three hours, combined. Then, in closing arguments Thursday, Yonan told jurors that Espinoza Martinez was “angry” about immigration enforcement last fall in Little Village, where he lived.
“He was fixated, and obsessed, with Gregory Bovino,” Yonan told the jury.
Prosecutors told jurors about a message Espinoza Martinez sent over Snapchat to Jimenez in early October. It followed a picture of Bovino and read, “2k on info cuando lo agarren,” “10k if u take him down,” and “LK … on him.”
Jimenez testified that he understood that to mean “$2,000 when they grab him … $10,000 if you kill him … Latin Kings are on him.”
Martinez’ brother explained one piece of evidence DOJ attempted to use against him: a gun that the brother (who has a concealed carry permit) was seeking for himself. And his attorneys emphasized that there was no evidence of an actual hit.
[Dena] Singer told the jury, “the government has failed to prove their case. You know it.”
No money exchanged hands, she said. No weapons were purchased. Social media, she said, “is riddled with things that aren’t true. … with people sending and sharing things.” There was no evidence that Espinoza Martinez intended for the murder to happen, or that he took a “substantial step,” she said.
Ultimately, live coverage of the trial made it sound like Martinez was passing on the chatter from his neighborhood, not plotting a hit himself (and it probably helped frame the case that the informant was seeking immigration protection himself).
As Seidel notes, this marks the 15th case, of 31, that have collapsed in Chicago since the invasion (I tracked the collapse of all the cases from just one day, September 27, here).
Espinoza Martinez is one of 31 known defendants charged in Chicago’s federal court with non-immigration crimes tied to the Trump administration’s aggressive deportation campaign last fall. With Thursday’s acquittal of Espinoza Martinez, 15 of them have now been cleared.
DOJ has pointed to this case, over and over, to claim there’s a real threat against Stephen Miller’s goons, including in their failed bid to get SCOTUS to bless Miller’s deployment of the National Guard to invade Chicago.
An alleged leader of the Latin Kings gang in Chicago is being prosecuted for placing a bounty of $10,000 on the murder of a Border Patrol Chief. Hott Decl. ¶¶ 24; Parra Decl. ¶ 17. These activities substantially interfere with DHS’s ability to enforce federal immigration laws in the Chicago area. See, e.g., Hott Decl. ¶¶ 43-47, 63. And it was clearly erroneous for the district court to discredit or minimize the unrebutted sworn testimony that those acts of violence and threats of violence in fact occurred.
There may well be; the actual Latin Kings may well be seeking to target Bovino (one of the people arrested for ransacking an FBI vehicle in Minnesota is more credibly claimed to be a Latin King). But if they are, then FBI wouldn’t learn of it because they are doing showboat arrests, not investigations.
Which is one of the many points in this compilation of quotes about how Kash Patel is destroying the FBI. Many of these anecdotes have been told anonymously in past reporting, but they are more powerful laid out like this; set aside some time to read this in full. FBI is not chasing complex crime anymore; they’re creating photo ops that please Donald Trump.
Patel directed the F.B.I., which has no immigration-enforcement authority, to support Immigration and Customs Enforcement in conducting raids and making arrests. Field offices began assigning F.B.I. agents and analysts to work immigration shifts, pulling them away from other priorities like counterterrorism, public corruption and white-collar crime.
John Sullivan, former section chief in the intelligence division: We’d been told that when Trump watched footage or saw a picture of a raid, he got mad that he didn’t see F.B.I. raid jackets.
ICE was saying they wanted their teams to commingle with our teams. Tactically, you don’t commingle units that haven’t trained together. My bosses said, If we work on immigration, we use our teams and our case info. They put together a list of people already in F.B.I. files we had concerns about, so we’re not just targeting people over their citizenship status.
They also had to juggle Kristi Noem, the secretary of the Department of Homeland Security, who wanted to ride in our tactical vehicle to do her TV stuff. That makes all the operators uneasy, and it makes them less safe.
And that makes it harder for FBI to do the complex investigations only they can do.
Midwest case agent: I was a grunt agent. I enjoyed trying to take apart large criminal organizations piece by piece.
They relabeled task forces from drugs to immigration and pushed us toward focusing on deportation versus convictions for actual drug offenses.
Unfortunately, what used to be our focus, long-term investigations, are now short-term hits. You hit the guy carrying the bag, not the guy who made the call, because that’s how you drive up the arrest and prosecution numbers. But the guy carrying the bag, you can’t flip anymore, because he’s getting deported.
Because F.B.I. agents are posting up with Homeland Security, citizens think we’re part of ICE, which disrupts other investigations. It used to be that you could sit in front of a house, watching another house, and a lot of the time, people were OK with that. They might help you. Now they’re scared.
All this was unrolling against the background of Jack Smith’s testimony. While there were moments of interest — Smith forcefully explained why Stan Woodward’s attack on Jay Bratt was bullshit, for example — mostly I feel the same way Phil Bump does. Everyone was just performing for the cameras.
There wasn’t much use to the hearing. There’s no actual question to adjudicate. No serious and unbiased observer questions Smith’s objectivity or credibility and no serious observer questions that Trump tried to overturn the 2020 election, triggering the riot that overwhelmed the building on Jan. 6, 2021. In effect, then, the existence of the hearing necessarily served to reinforce the falsehood that there was a debate in the first place.
Smith summarized the importance of recognizing reality in his opening remarks.
“The rule of law is not self-executing,” he said. That is, the bounds of the law are real only to the extent that they are respected. Smith, better than most, understands what it looks like when that respect evaporates.
The product of the hearing wasn’t a studious consideration of the validity of his work since, as stipulated above, there was nothing serious to mull over. Instead, the primary output of the hearing was probably a tidy stream of social-media-friendly video snippets. Members of the House (nearly all of whom will soon face primaries or reelection) saw an opportunity to make news and most of them tried.
What this means, in effect, is that the hearing not only didn’t resolve any tension between reality and surreality, it simply dug each side in a little deeper.
Perhaps the most effective moment in the hearing was Jared Moskowitz’ soliloquy, which combined a reminder of all the times the very same Republicans who performed Donald Trump’s assault on Smith’s investigation expressed terror during January 6 itself.
The AI slop the White House released yesterday really embodies what Pam Bondi’s DOJ has become.
Bullshit all the way down.