DOJ to Apple: Start Cooperating or You’ll Get the Lavabit Treatment
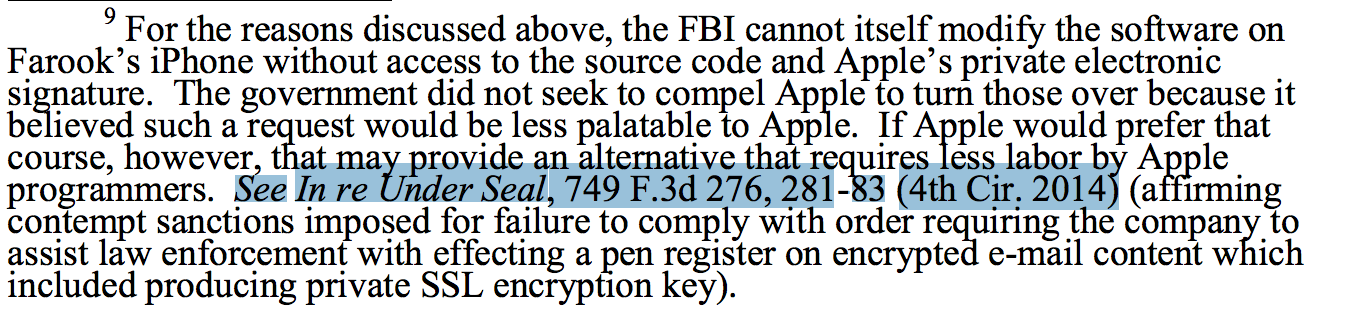
DOJ has submitted its response to Apple in the Syed Farook case. Amid invocations of a bunch of ominous precedents — including Dick Cheney’s successful effort to hide his energy task force, Alberto Gonzales effort to use kiddie porn as an excuse to get a subset of all of Google’s web searches, and Aaron Burr’s use of encryption — it included this footnote explaining why it hadn’t just asked for Apple’s source code.
That’s a reference to the Lavabit appeal, in which Ladar Levison was forced to turn over its encryption keys.
As it happens, Lavabit submitted an amicus in this case (largely arguing against involuntary servitude). But as part of it, they revealed that the reason the government demanded Lavabit’s key is because “in deference to [Edward Snowden’s] background and skillset, the Government presumed the password would be impossible to break using brute force.”
But that says that for phones that — unlike Farook’s which had a simple 4-digit passcode — the government maintains the right to demand more, up to and including their source code.
The government spends a lot of time in this brief arguing it is just about this one phone. But that footnote, along with the detail explaining why they felt the need to obtain Lavabit’s key, suggests it’s about far more than even Apple has claimed thus far.


Seems to me the only thing the FBI is competent about is intimidating others. Maybe they should wear brownshirts.
It’s clear that it’s about the MIC wanting access to everything. Not that they can use everything they get now, or even need everything they get now, but that they think they need access to everything.
Gotta make that haystack even bigger so they can get more money and continue not finding the few needles that are actually in it.
Briefs like that are one of the later stages of public acknowledgment that a society is becoming a police state.
Later, they won’t even have to threaten the few remaining “independent” companies into compliance.
I have read, and recommend you read (if you want a one-stop information service on the Apple case), the Congressional Research Service report just issued on Encryption. Lays out some facts on encryption, walks slowly and carefully through the law on point (which is both laptop/desktop law as well as smartphone law); and discusses how the law might apply to the issues in the Apple case. Doesn’t discuss policy or PR issues, but rather is quite neutral and informative; it reads like it was written by a law clerk, not an advocate.
.
http://www.fas.org/sgp/crs/misc/R44407.pdf
Link to a ZDNet Article on Apple calling the latest DOJ filing a cheap shot. That’s putting it mildly.
.
Seems possible this is Obama, Lynch and DOJ more than FBI. Or maybe it’s all the SOBs.
Oops prior link led with https:// and that won’t work, remove it, or this link should work better. Sorry.
Must see top of http://www.groklaw.net
Note: site is *NOT* ssl/tls but PJ talks about email which should
be using STARTTLS these days. Either way, we are most assuredy
talking about RSA under the hood.
Unfortunately, I am of very strong belief that RSA is pwned by NSA.
It is NOT trustable. All your primes are belong to US. The NSA has
been sieving primes for decades now.
The only alternative is eliptic curve which while more difficult
than factoring a large semiprime, may also be attackable via
other weaknesses in the implementation (see DROWN for example).
The only true trustable encryption is the use of One-Time-Pad,
which has the two problems of securely transmitting the OTP
and never re-using the OTP.
If you can securely transmit the OTP you can just securely transmit
the original message instead.
The ultimate solution to all of these attacks is to go back,
to use cash and talk face-to-face. I aways recommend that
one never do any banking transactions online. Paper is safer.
quote”The ultimate solution to all of these attacks is to go back,
to use cash and talk face-to-face. I aways recommend that
one never do any banking transactions online. Paper is safer.”unquote
I’ve got $25 that says 3 million smartphone owners would erupt in coast to coast, raucous, gut splitting laughter. But I agree with you. Unfortunately, give it a few years and paper currency will be a relic. By statute.
I recently had this nightmare in which an EO was used to reinterpret the Invention Secrecy Act of 1951 and in dawn raids DoJ SWAT teams seized Apple patents, along with the source code and several engineers…
quote”I recently had this nightmare in which an EO was used to reinterpret the Invention Secrecy Act of 1951 and in dawn raids DoJ SWAT teams seized Apple patents, along with the source code and several engineers…”unquote
Yeah, and I recently had this nightmare in which an EO was used to reinterpret the 2nd Amendment and in dawn raids during a nationwide Jade Helm type exercise, the US military, using BACKGROUND CHECK lists of gun owners, began house to house forced weapon confiscation..which in turn, began our second bloody civil war. Only to wake up to a police/surveillance state preparing for that very nightmare.