Why Did Apple “Object” to All Pending All Writs Orders on December 9?
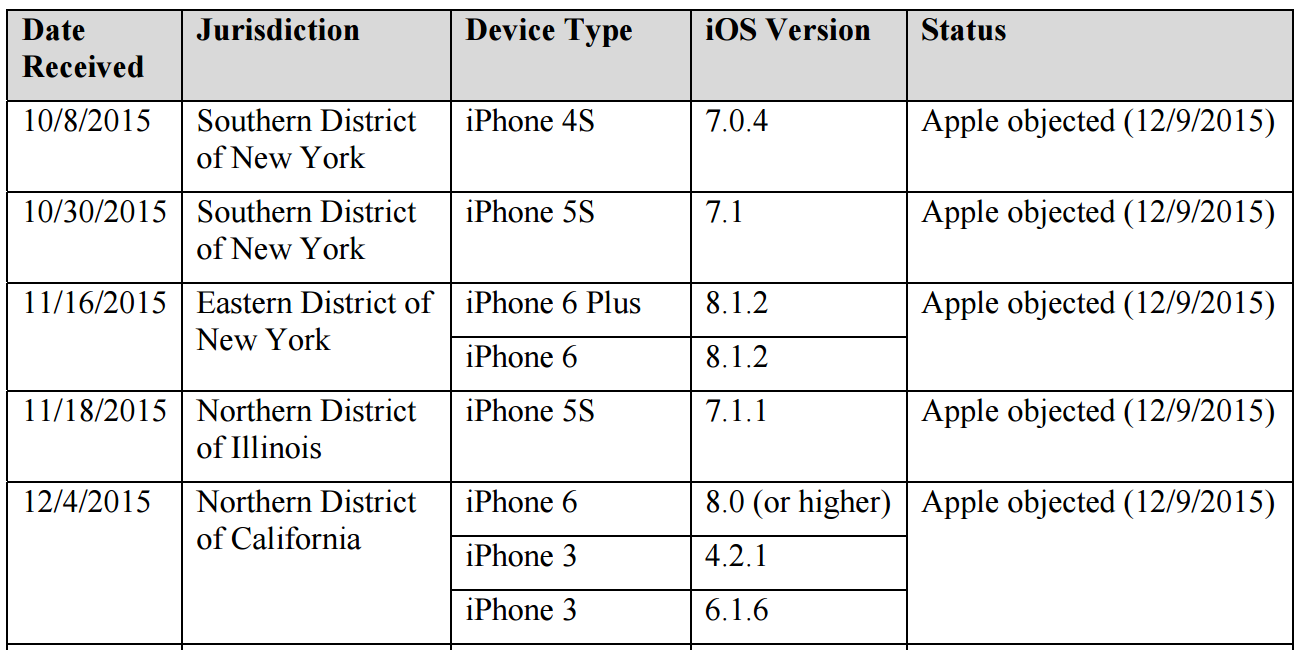
As I noted the other day, a document unsealed last week revealed that DOJ has been asking for similar such orders in other jurisdictions: two in Cincinnati, four in Chicago, two in Manhattan, one in Northern California (covering three phones), another one in Brooklyn (covering two phones), one in San Diego, and one in Boston.
According to Apple, it objected to at least five of these orders (covering eight phones) all on the same day: December 9 (note, FBI applied for two AWAs on October 8, the day in which Comey suggested the Administration didn’t need legislation, the other one being the Brooklyn docket in which this list was produced).
The government disputes this timeline.
In its letter, Apple stated that it had “objected” to some of the orders. That is misleading. Apple did not file objections to any of the orders, seek an opportunity to be heard from the court, or otherwise seek judicial relief. The orders therefore remain in force and are not currently subject to litigation.
Whatever objection Apple made was — according to the government, anyway — made outside of the legal process.
But Apple maintains that it objected to everything already in the system on one day, December 9.
Why December 9? Why object — in whatever form they did object — all on the same day, effectively closing off cooperation under AWAs in all circumstances?
There are two possibilities I can think of, though they are both just guesses. The first is that Apple got an order, probably in an unrelated case or circumstance, in a surveillance context that raised the stakes of any cooperation on individual phones in a criminal context. I’ll review this at more length in a later post, but for now, recall that on a number of occasions, the FISA Court has taken notice of something magistrates or other Title III courts have done. For location data, FISC has adopted the standard of the highest common denominator, meaning it has adopted the warrant standard for location even though not all states or federal districts have done so. So the decisions that James Orenstein in Brooklyn and Sheri Pym in Riverside make may limit what FISC can do. It’s possible that Apple got a FISA request that raised the stakes on the magistrate requests we know about. By objecting across the board — and thereby objecting to requests pertaining to iOS 8 phones — Apple raised the odds that a magistrate ruling might help them out at FISA. And if there’s one lawyer in the country who probably knows that, it’s Apple lawyer Marc Zwillinger.
Aside the obvious reasons to wonder whether Apple got some kind of FISA request, in his interview with ABC the other day, Tim Cook described “other parts of government” asking for more and more cases (though that might refer to state and city governments asking, rather than FBI in a FISA context).
The software key — and of course, with other parts of the government asking for more and more cases and more and more cases, that software would stay living. And it would be turning the crank.
The other possibility is that by December 9, Apple had figured out that — a full day after Apple had started to help FBI access information related to the San Bernardino investigation, on December 6 — FBI took a step (changing Farook’s iCloud password) that would make it a lot harder to access the content on the phone without Apple’s help. Indeed, I’m particularly interested in what advice Apple gave the FBI in the November 16 case (involving two iOS 8 phones), given that it’s possible Apple was successfully recommending FBI pursue alternatives in that case which FBI then foreclosed in the San Bernardino case. In other words, it’s possible Apple recognized by December 9 that FBI was going to use the event of a terrorist attack to force Apple to back door its products, after which Apple started making a stronger legal stand than they might otherwise have done pursuant to secret discussions.
That action — FBI asking San Bernardino to change the password — is something Tim Cook mentioned several times in his interview with ABC the other night, at length here:
We gave significant advice to them, as a matter of fact one of the things that we suggested was “take the phone to a network that it would be familiar with, which is generally the home. Plug it in. Power it on. Leave it overnight–so that it would back-up, so that you’d have a current back-up. … You can think of it as making of making a picture of almost everything on the phone, not everything, but almost everything.
Did they do that?
Unfortunately, in the days, the early days of the investigation, an FBI–FBI directed the county to reset the iCloud password. When that is done, the phone will no longer back up to the Cloud. And so I wish they would have contacted us earlier so that that would not have been the case.
How crucial was that missed opportunity?
Assuming the cloud backup was still on — and there’s no reason to believe that it wasn’t — then it is very crucial.
And it’s something they harped on in their motion yesterday.
Unfortunately, the FBI, without consulting Apple or reviewing its public guidance regarding iOS, changed the iCloud password associated with one of the attacker’s accounts, foreclosing the possibility of the phone initiating an automatic iCloud back-up of its data to a known Wi-Fi network, see Hanna Decl. Ex. X [Apple Inc., iCloud: Back up your iOS device to iCloud], which could have obviated the need to unlock the phone and thus for the extraordinary order the government now seeks.21 Had the FBI consulted Apple first, this litigation may not have been necessary.
Plus, consider the oddness around this iCloud information. FBI would have gotten the most recent backup (dating to October 19) directly off Farook’s iCloud account on December 6.
But 47 days later, on January 22, they obtained a warrant for that same information. While they might get earlier backups, they would have received substantially the same information they had accessed directly back in December, all as they were prepping going after Apple to back door their product. It’s not clear why they would do this, especially since there’s little likelihood of this information being submitted at trial (and therefore requiring a parallel constructed certified Apple copy for evidentiary purposes).
There’s one last detail of note. Cook also suggested in that interview that things would have worked out differently — Apple might not have made the big principled stand they are making — if FBI had never gone public.
I can’t talk about the tactics of the FBI, they’ve chosen to do what they’ve done, they’ve chosen to do this out in public, for whatever reasons that they have.What we think at this point, given it is out in the public, is that we need to stand tall and stand tall on principle. Our job is to protect our customers.
Again, that suggests they might have taken a different tack with all the other AWA orders if they only could have done it quietly (which also suggests FBI is taking this approach to make it easier for other jurisdictions to get Apple content). But why would they have decided on December 9 that this thing was going to go public?
Update: This language, from the Motion to Compel, may explain why they both accessed the iCloud and obtained a warrant.
The FBI has been able to obtain several iCloud backups for the SUBJECT DEVICE, and executed a warrant to obtain all saved iCloud data associated with the SUBJECT DEVICE. Evidence in the iCloud account indicates that Farook was in communication with victims who were later killed during the shootings perpetrated by Farook on December 2, 2015, and toll records show that Farook communicated with Malik using the SUBJECT DEVICE. (17)
This passage suggests it obtained both “iCloud backups” and “all saved iCloud data,” which are actually the same thing (but would describe the two different ways the FBI obtained this information). Then, without noting a source, it says that “evidence in the iCloud account” shows Farook was communicating with his victims and “toll records” show he communicated with Malik. Remember too that the FBI got subscriber information from a bunch of accounts using (vaguely defined) “legal process,” which could include things like USA Freedom Act.
The “evidence in the iCloud account” would presumably be iMessages or Facetime. But the “toll records” could be too, given that Apple would have those (and could have turned them over in the earlier “legal process” step. That is, FBI may have done this to obscure what it can get at each stage (and, possibly, what kinds of other “legal process” it now serves on Apple).
October 8: Comey testifies that the government is not seeking legislation; FBI submits requests for two All Writs Act, one in Brooklyn, one in Manhattan; in former case, Magistrate Judge James Orenstein invites Apple response
October 30: FBI obtains another AWA in Manhattan
November 16: FBI obtains another AWA in Brooklyn pertaining to two phones, but running iOS 8.
November 18: FBI obtains AWA in Chicago
December 2: Syed Rezwan Farook and his wife killed 14 of Farook’s colleagues at holiday party
December 3: FBI seizes Farook’s iPhone from Lexus sitting in their garage
December 4: FBI obtains AWA in Northern California covering 3 phones, one running iOS 8 or higher
December 5, 2:46 AM: FBI first asks Apple for help, beginning period during which Apple provided 24/7 assistance to investigation from 3 staffers; FBI initially submits “legal process” for information regarding customer or subscriber name for three names and nine specific accounts; Apple responds same day
December 6: FBI works with San Bernardino county to reset iCloud password for Farook’s account; FBI submits warrant to Apple for account information, emails, and messages pertaining to three accounts; Apple responds same day
December 9: Apple “objects” to the pending AWA orders
December 10: Intelligence Community briefs Intelligence Committee members and does not affirmatively indicate any encryption is thwarting investigation
December 16: FBI submits “legal process” for customer or subscriber information regarding one name and seven specific accounts; Apple responds same day
January 22: FBI submits warrant for iCloud data pertaining to Farook’s work phone
January 29: FBI obtains extension on warrant for content for phone
February 14: US Attorney contacts Stephen Larson asking him to file brief representing victims in support of AWA request
February 16: After first alerting the press it will happen, FBI obtains AWA for Farook’s phone and only then informs Apple


Here’s part of what the govt. motion says: “ … the Order is tailored for and limited to this particular phone. And the Order will facilitate only the FBI’s efforts to search the phone; it does not require Apple to conduct the search or access any content on the phone. Nor is compliance with the Order a threat to other users of apple product. … As such, compliance with the Order presents no danger for any other phone and is not “the equivalent of a master key, capable of opening hundreds of millions of locks”.”
.
That statement was signed off on by Eileen M. Decker, AUSA. Hey Ms. Decker: Will you, in open court, swear that a forced compliance with this Order will NEVER EVER be cited as precedent for use by any government entity against any other iPhone? Will you pledge to go to jail and stay there for six years if the FBI either cites it directly or uses its existence to pressure someone, at any time EVER in the future for any other phone? Will you pledge in open court, that you will bring along Jim Comey to serve jail time with you? No? Then tell us, what WILL you do, if this promise is ever broken? Huh? If you won’t do anything, then your words are meaningless, don’t you agree? And why should anyone rely on them? Come now, answer the question.
.
Link to motion:
.
http://www.wired.com/wp-content/uploads/2016/02/Apple-iPhone-access-MOTION-TO-COMPEL.pdf
Thin entering wedge: They used the ticking time bomb scenario to justify torture; then they used torture to interrogate Khalid Sheikh Mohammed about whether there were any ticking time bombs.
When is Apple going to start calling people like Mike Hayden who agree with them that the value of secure communications for everyone is far higher than the occasional utility of access to a single device? Strange bedfellows to be sure, but on the same side of this issue.
.
“But that’s just one in a long line of things Jim Comey hasn’t been honest about.”
.
Are we past the point where it is easier and less time consuming to just track the few things Jim Comey has been honest about?
So, Farook left this phone in his car. We can probably assume that the FBI has some metadata from the phone company. We can also assume that someone probably called Farook, after the shooting, asking, “Why?” or “Are you alive?” if they did not recognize him. So, the FBI is probably telling the truth in that the phone probably was used. They probably determined that fact. Isn’t it strange that Comey is saying that he is concerned with them contacting terrorists after the incident? Wouldn’t the terrorists see it on the news? Did they need a detailed account? I think Comey is saying that because phone-company data before the attack probably showed that the phone was hardly used at all. But after, yes, the county or some co-worker probably phoned Farook.
In all these other cases, Apple probably provided good iCloud backups, but no information was found. And yes, I think your implication is probable. The FBI probably followed the correct procedure for iCloud information in the other cases, and deliberately changed the password in this case, knowing that Farook would not use a government-issued phone to plot that conspiracy. He probably suspected that the phone had management software on it, and that’s the reason why he had a personal phone. It would be good to know how many employees in San Bernadino pay extra for a personal phone.
I find footnote 26,
“If the government did have any leads on additional suspects, it is inconceivable that it would have filed pleadings on the public record, blogged, and issued press releases discussing the details of the situation, thereby thwarting its own efforts to apprehend the criminals. See Douglas Oil Co. of Cal. v. Petrol Stops Nw., 441 U.S. 211, 218-19 (1979) (“We consistently have recognized that the proper functioning of our grand jury system depends upon the secrecy of grand jury proceedings. . . . [I]f preindictment proceedings were made public, many prospective witnesses would be hesitant to come forward voluntarily, knowing that those against whom they testify would be aware of that testimony. . . . There also would be the risk that those about to be indicted would flee, or would try to influence individual grand jurors to vote against indictment.”).”
as the most caustic part of Apple’s brief, and I wonder whether it is just invective, or if there’s some avenue of discovery that Apple can open because of its inclusion.
re: Dec. 9, 2015
.
Perhaps not a coincidence of timing:
On December 08, 2015 google publically announces that Google/NASA/LockheadMartin have a working “quantum computer”– the
D-Wave X-2. This quantum computer that uses “qubits” (quantum bits) that enable computing speeds ‘3,600 times faster than a supercomputer.’
.
http://www.nature.com/news/physics-quantum-computer-quest-1.16457
.
A quantum computer could be used to BREAK current encryption methods, because it can find the prime factors of any massively large number quickly—a feat that usually is beyond regular computing power.
.
This makes the built-in physical bottle neck in Apple’s newer iPhones all the more important for maintaining the security of the iphone. (i.e., instructions to autowipe after 10 failed attempts to enter the code).
.
With a quantum computer you won’t need centuries to crack the iphone’s encryption, but you MIGHT need more than 10 tries.
While D-wave Systems,the Vancouver based manufacturer of the supercomputer had indeed announced the General Availablityof their expanded in size quantum computer their long-term customer Lockheed-Martin had alraedy announced that the machine will not be installed & working until January 2016
.
January 2016 was a month ago… It should be up and running, was there a setback?
Clarification: not truly a “physical” bottleneck as the locks are software-enabled and software defeat-able (w/Apple’s cooperation).
.
Some news from John Gruber about Apple’s possible future plans for phone security.
.
https://daringfireball.net/linked/2016/02/24/iphone-impregnability
Interesting suggestion.
“… There are two possibilities I can think of, though they are both just guesses. The first is that Apple got an order, probably in an unrelated case or circumstance, in a surveillance context that raised the stakes of any cooperation on individual phones in a criminal context…”
so, as many may have suspected, i among them, the u. s. dept of justice’s san bernardino claim against apple may be a deceitful claim exploiting the contemporary social politics of “terrorism” and, in particular, exploiting american judges’ (and politicians’) terror about alleged terrorism in order to gain a prosecutorial advantage in a matter not related to “terrorism”.
the dept of justice really would benefit greatly in the long run from a president who will clean the place out, as our previous great hope, president obama, failed to do.
i’m not sure this argument is solid, but it occurs to me that if the doj can break apple’s encryption on a (fake) terrorism complaint, then they might hide subsequent uses of the technology in non-terrorism cases – with american judges’ acquiescence – using a state’s secrets argument, thus withholding critical info from defense attorneys. this is not the first time this thought has troubled me.
or maybe just using a “proprietary secrets” argument to the judge to get away with hiding info from public and decense.
could doj really get away with that one?
In regard to the timing of this fight, it seems pretty obvious that a few years ago, probably pre-Snowden, but if post-snowden, then with all due speed, Apple drew a line at where they would make their stand with the government. That’s to say, although Comey has been planning this for a few years, it would be safe to say that Apple views this struggle as “in their DNA” as they would say, perhaps referencing the Ridley Scott commercial. So, it would be very surprising these legal arguments and strategy weren’t thought out a few years ago, and the FBI merely reached the red line.
Thank you Marcy! You are putting the entire systemic illegal government into the light of Day!
The Bill of Corrupt Government has gone far enough! Next on the agenda is the RICO LAW being applied to those in and working in conjunction our government being held accountable in Courts of Law!
I just noticed the Nature article I linked to was from Dec 2014.
.
Here’s the Dec 8, 2015 public announcement from google about its new quantum computer:
.
http://googleresearch.blogspot.com/2015/12/when-can-quantum-annealing-win.html
with respect to quantum computers, should they prove viable, nature had this article on the propect that quantum computing would essentailly quarantee privacy.
nature, vol 27, p. 443 (march 27,2014).
“the ultimate physical limits of privacy”, artur ekert and rennato renner.
i would add this caveat, privacy is possible UNLESS the principal had been engrained in law that encryptions schemes must be surrended to the reigning government policing/natsec authority.
copying from the physical text in front of me (i tore the article out of our copy):
“… recent developments in quantum crypography show that some of these quezyions [about privacy] can be… discussed in precise and operational terms, suggesting that privacy is indeed possible under surprisingly weak assumptions.”
so maybe all this legal folderol by the dept of justice is about sertting rules just prior to the introduction of quantum computing.
It’s a very important legal battle that could shape the rules of government-private interactions for generations. Unless the USG backs off to avoid the judiciary resolving the matter rather than the legislature, it will certainly not be settled until well into the next administration.
.
I’ve put up a Table of Players and a detailed Timeline, both nascent but growing, as static pages to help keep track of the details and documents as the story unfolds over the coming years.
.
http://logophere.com/SideBar%20Pages/DoJ%20v%20Apple%20Portal.htm
.
Worst case scenario: Congress successfully stonewall’s Obama’s USSCt nomination, Trump appoints Glenn Beck to replace Scalia, then Trump appoints Sarah Palin or Ann Coulter to replace Ginsburg when she kicks-off, all before the case reaches the USSCt.
.
And people keep asking me why I’m depressed . . .
You are assuming that the Republican majorities in Congress will remain. If Hilary is the nominee I suspect that there will be little change in Congress. But if a ‘real’ democrat runs a strong campaign the likelihood is that it will sweep a Democratic majority into the House and lead to Democratic victories in the Senate.
I wonder if Casper Bowden’s warnings about forced compliance on Remote Computer Services is somehow part of this dispute
http://www.networkworld.com/article/2866286/microsoft-subnet/former-microsoft-chief-privacy-officer-on-the-cloud-conspiracy.html
Hmmm …
‘Most software already has a “golden key” backdoor: the system update
Software updates are just another term for cryptographic single-points-of-failure.’
by Leif Ryge – Feb 27, 2016 1:25 pm UTC
http://arstechnica.com/security/2016/02/most-software-already-has-a-golden-key-backdoor-its-called-auto-update/
The judge in Brooklyn has ruled that the government can’t compel Apple to provide the iPhone data. It’s a drug case, where the guy had already pleaded guilty.
http://www.sfgate.com/business/technology/article/NY-judge-US-cannot-make-Apple-provide-iPhone-data-6861454.php
http://www.rawstory.com/2016/02/federal-judge-rules-justice-dept-cannot-order-apple-to-unlock-iphone-seized-in-drug-bust/