Ho hum. Another day, another David Weiss filing that may face significant evidentiary challenges at trial.
In past posts, I have shown how one after another sex worker, payments to whom prosecutors have made central to their allegations that Hunter Biden cheated on his taxes, may pose evidentiary problems if the case goes to trial.
In one case, David Weiss included in the tax indictment the first Venmo payment — and its misleading payment description and Weiss’ likely incorrect date — that Hunter made after two new devices accessed the account, 12 minutes apart, from two different cities. In another, I showed that a sex worker the IRS actually interviewed about her dates with Hunter was among the last people Hunter spent time with before he attempted to reclaim the part of his digital life hosted at Apple, using a laptop that would eventually be found at Fox News pundit-shrink Keith Ablow’s office when the DEA searched it in February 2020.
Even as the IRS spent years scrutinizing Hunter’s digital payments, they appear to have ignored how his digital life faced one after another compromise, most (but potentially not all) undoubtedly arising from the erratic habits of an addict. Those potential compromises should have elicited an entirely different investigative focus, but they also will make any digital evidence obtained from Hunter Biden’s devices difficult and at times impossible to validate for trial.
Take the texts that Hunter Biden sent Hallie in the two days after he purchased the gun for which he has been charged with three felonies, texts that Weiss has admitted he did not seek until last year, apparently only after indicting the President’s son. Prosecutors are very excited about obtaining these texts, after the fact, to prove that Hunter was smoking crack during the days he possessed a gun.
On October 13, 2018, and October 14, 2018 (the day after and two days after he purchased the firearm), the defendant messaged his girlfriend about meeting a drug dealer and smoking crack. For example, on October 13, 2018, the defendant messaged her and stated, “. . . I’m now off MD Av behind blue rocks stadium waiting for a dealer named Mookie.” The next day, the defendant messaged her and stated, “I was sleeping on a car smoking crack on 4th street and Rodney.”
Weiss doesn’t say what time these texts were sent. Nor does he say whether these were telephony or app texts (Hunter was using at least WhatsApp in the period), and if the former, via which phone account.
But it happened on the same days that Hunter was informed that someone, whose name does not otherwise show up in public emails, emailed Hunter to tell him “you left your phone,” followed, after three attempts, by a shared Note that appears to link to a live Apple account (the times here are UTC-3, so one hour ahead of EDT; I hope I’ve adjusted all the times below to EDT).
And, indeed, Hunter does appear to have left his phone — or phones, plural — somewhere, probably the day before he bought the gun.
In those same two days in which those texts were sent to Hallie, there were four different attempts to replace phones via an Asurian protection plan, two of which ended in the delivery of phones he is known to have adopted as his primary phones afterwards, two of which tied to other numbers that ended in uncertain status. In addition to those iPhones he would use to replace his main phones, Hunter (or someone else) accessed his digital identity from a Samsung Galaxy, a rare deviation from Hunter’s commitment to Apple products.
A week later Hunter’s account would begin to be accessed using the laptop that would ultimately end up with the FBI.
The traffic for just those three days looks like this, with the emails from Joey bolded and two key account changes italicized:
October 12, 12:56PM: As you requested, your temporary [AT&T] password is: ****** Use your user ID and temporary password to sign in to your account.
October 12, 12:56PM: Looks like you recently updated the AT&T password.
October 12, 12:57PM: Critical security alert for your linked Google Account, Sign-in attempt was blocked for your linked [RosemontSeneca] Google Account [device not specified]
October 12, 3:25PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 431] has been started
October 12, 3:32PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 431] has been started
October 12, 3:38PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 579] has been started
October 12, 3:40PM: Your [AT&T] insurance claim [phone ending in 96]
October 12, 3:44PM: Your [AT&T] insurance claim [phone ending in 13]
October 12, 3:49PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 701] has been started
October 12, 3:55PM: Please complete and return your claim documents Wireless Number: **94
October 12, 3:57PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 799] has been started
October 12, 4:03PM: Please complete and return your claim documents Wireless Number: **29
October 12, 5:35PM: Hello. Review your AT&T order
October 12, 6:22PM: Good news. Your replacement device [grey Apple iPhoneX] has shipped. [phone ending in 13]
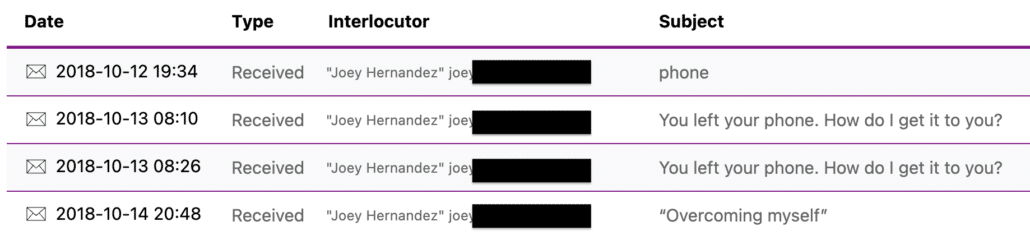
October 12, 6:24PM: Phone [from Joey]
Hey, You left your phone and other things. Tried to reach you at 202 and 302 all day but no luck. Let me know where to overnight.
October 12, 7:20PM: Good news. Your replacement device [iPhone 8] has shipped. [phone ending in 96]
October 12, 8:00PM: Verify your Samsung account [accessing Hunter’s iCloud]
October 12, 11:31PM: Someone Just Checked Your Background Report
October 13, 7:10AM: You left your phone. How do I get it to you?
joey
October 13, 7:26AM: You left your phone. How do I get it to you?
joey
October 13, 11:13AM: Let’s setup your AT&T replacement device [phone ending in 13]
October 13, 12:35AM: Someone Just Checked Your Background Report
October 13, 2:00PM: Hello, Review your AT&T order [changes to wireless]
October 13, 9:17PM: Your [RosemontSeneca] Google Account was just signed in to from a new Samsung Galaxy Note 9 device
October 13, 11:36PM: Wells Fargo Has Registered Your Mobile Device
October 14, 2:24PM: Your Apple ID password has been reset
October 14, 2:24PM: Your Apple ID was used to sign in to iCloud on an iPhone X
October 14, 3:28PM: Wells Fargo card added to Apple Pay
October 14, 3:36PM: Verify your Samsung account [on iCloud]
October 14, 7:48PM: “Overcoming myself” [from Joey]
When you have a minute, read ….
Open my shared note:
Interspersed with this traffic, Hunter’s accountant was trying to get him to file his 2017 taxes, Twitter was informing him of this story showing that Jared Kushner hadn’t paid taxes for years, Hunter was draining his bank account one $800 withdrawal after another, and his business partner was approving a payment to Hunter’s lawyer that would all but drain the Hudson West business associated with CEFC. A different business partner, Eric Schwerin, was also pushing Hunter to resolve their business interests during the 2018 tax year, something he failed to pull off.
Without the location and IP addresses, it’s not entirely sure what happened here (Weiss should have that with the iCloud data). It’s not even clear that Hunter had a phone, at all, between the time he lost his phones, plural, on October 11 and started using his new iPhone X on October 14 (though he did have a third phone tied to an account he used with sex workers). Hunter may have used the Samsung as a temporary phone for those two days or borrowed someone else’s Samsung to check his email; but it wasn’t verified to his iCloud account before October 14 at 3:36PM, and so may not have been able to access some Apple services. Importantly, however, that phone accessed his RosemontSeneca Google account after Hunter had started using one of his new replacement iPhones, something that doesn’t make sense if he was borrowing it.
If the texts to Hallie were sent after Hunter changed his wireless account at 2PM on October 13, they might be traced to a secure telephony account. But if they were sent via iMessage or WhatsApp before Hunter changed his iCloud password at 2:24PM on October 14, then you’d have to use location and IP data to rule out that someone else sent those texts to Hallie, using Hunter’s still accessible iCloud account via his lost phones (plural, apparently).
Because this particular verification challenge involves iCloud, which should have the location and IP data to verify which devices were used, and because (unlike the sex workers) it wouldn’t involve Hunter’s copresence with someone accessing his bank account via biometrics that others might access if he were wasted, this should be something that prosecutors could definitively prove, if indeed Hunter did send these texts.
If they can’t prove the location and IP from which these texts were sent, they may not be admissible at all, because prosecutors may not be able to prove that they are, in fact, Hunter’s words and not those of someone using his lost phones.
If this goes to trial, it might be worth forcing prosecutors to go through the effort to prove Hunter did send the texts, because it not only demonstrates how uncertain this evidence can be five years after the fact, but it would also show that Hunter spent hours trying to reclaim his digital identity — possibly using the laptop that would end up in Ablow’s possession — during the period when, prosecutors would be arguing, he was sleeping [in] a car and smoking crack.
Plus, that process would demonstrate something else. First, note that Hunter never verifiably made efforts that he did in August (the day before the dual Venmo access) to shut down access others would have via those lost devices to his digital identity. There’s no evidence here that Hunter deleted those phones, as he had only just finished doing weeks earlier with an iPad taken in August. That is, if Joey or whoever had one or two phones that Hunter had been using for weeks or months, there would be a great deal of data on them that would allow them, or anyone who subsequently got the phones, to carry out a much more systematic compromise of Hunter’s digital identity in the future.
There’s also no evidence that Hunter changed passwords besides the AT&T one, including for the RosemontSeneca email account that hosted all the work emails that would become so controversial years later. If he didn’t do that, then at least one of those two lost phones could likely access that account without interruption.
I’m not yet ready to show it, but this process, the incomplete effort to reclaim his digital identity, continued through the period where Hunter’s account started being accessed by a new laptop on October 21. And, depending on how the progression from prosecutors’ initial August 2019 iCloud warrant to the December 2019 warrant for that same laptop itself to the warrant to expanded scope of Hunter’s iCloud in July 2020 culminating in December 2023 in the use of those iCloud texts to substantiate a gun case occurred — something that Derek Hines deliberately obfuscates in this same filing — it may mean that this entire investigation has been built on this impossibly rocky foundation since 2019.
The laptop that FBI started using as evidence without first fully validating it destroys chain of custody not just because it was accessed by a hostile person over the course of months before being delivered to the FBI, but also because Hunter’s use of it would have been built on a digital identity that was totally compromised.
Normally, financial records are what make tax cases easy to prove (and, to be sure, many of the financial records used for Hunter’s tax indictment will be easily verifiable). Normally, these kinds of digital communications are what make other indictments easy to prove without having to rely on a sympathetic witness like Hallie Biden, one personally implicated in the insecure disposal of a gun.
But even ignoring the likelihood that more nefarious people might have compromised Hunter’s identity in this period (for which these is some evidence), Hunter’s addiction meant that his digital identity was persistently in a state of half-compromise through this entire period. His addiction led him to do things that prosecutors have now charged him for. It also adds a good deal of validation challenges for the kind of evidence that normally is routine.