Hunter Biden Lost His Phone(s) in the Same Days He Bought a Gun
Ho hum. Another day, another David Weiss filing that may face significant evidentiary challenges at trial.
In past posts, I have shown how one after another sex worker, payments to whom prosecutors have made central to their allegations that Hunter Biden cheated on his taxes, may pose evidentiary problems if the case goes to trial.
In one case, David Weiss included in the tax indictment the first Venmo payment — and its misleading payment description and Weiss’ likely incorrect date — that Hunter made after two new devices accessed the account, 12 minutes apart, from two different cities. In another, I showed that a sex worker the IRS actually interviewed about her dates with Hunter was among the last people Hunter spent time with before he attempted to reclaim the part of his digital life hosted at Apple, using a laptop that would eventually be found at Fox News pundit-shrink Keith Ablow’s office when the DEA searched it in February 2020.
Even as the IRS spent years scrutinizing Hunter’s digital payments, they appear to have ignored how his digital life faced one after another compromise, most (but potentially not all) undoubtedly arising from the erratic habits of an addict. Those potential compromises should have elicited an entirely different investigative focus, but they also will make any digital evidence obtained from Hunter Biden’s devices difficult and at times impossible to validate for trial.
Take the texts that Hunter Biden sent Hallie in the two days after he purchased the gun for which he has been charged with three felonies, texts that Weiss has admitted he did not seek until last year, apparently only after indicting the President’s son. Prosecutors are very excited about obtaining these texts, after the fact, to prove that Hunter was smoking crack during the days he possessed a gun.
On October 13, 2018, and October 14, 2018 (the day after and two days after he purchased the firearm), the defendant messaged his girlfriend about meeting a drug dealer and smoking crack. For example, on October 13, 2018, the defendant messaged her and stated, “. . . I’m now off MD Av behind blue rocks stadium waiting for a dealer named Mookie.” The next day, the defendant messaged her and stated, “I was sleeping on a car smoking crack on 4th street and Rodney.”
Weiss doesn’t say what time these texts were sent. Nor does he say whether these were telephony or app texts (Hunter was using at least WhatsApp in the period), and if the former, via which phone account.
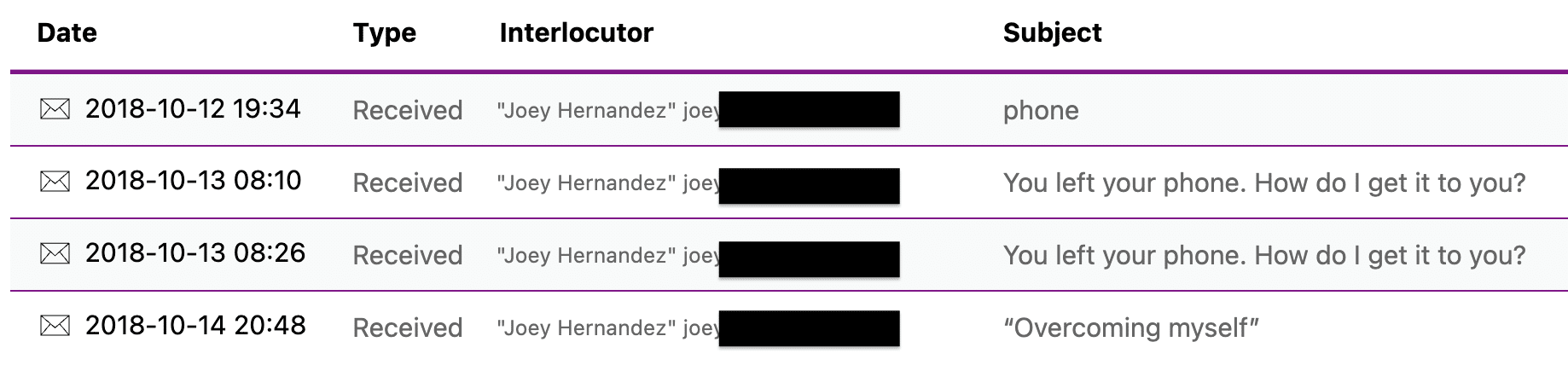
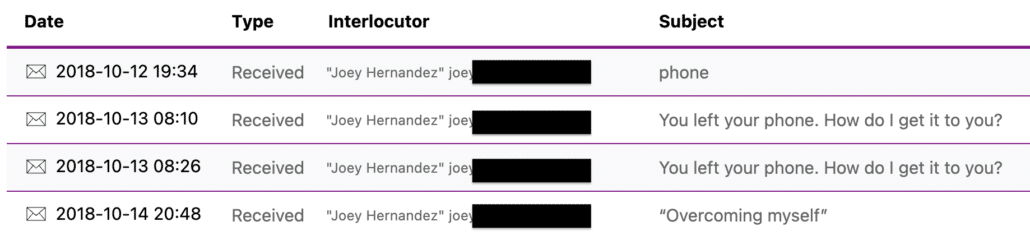
But it happened on the same days that Hunter was informed that someone, whose name does not otherwise show up in public emails, emailed Hunter to tell him “you left your phone,” followed, after three attempts, by a shared Note that appears to link to a live Apple account (the times here are UTC-3, so one hour ahead of EDT; I hope I’ve adjusted all the times below to EDT).
And, indeed, Hunter does appear to have left his phone — or phones, plural — somewhere, probably the day before he bought the gun.
In those same two days in which those texts were sent to Hallie, there were four different attempts to replace phones via an Asurian protection plan, two of which ended in the delivery of phones he is known to have adopted as his primary phones afterwards, two of which tied to other numbers that ended in uncertain status. In addition to those iPhones he would use to replace his main phones, Hunter (or someone else) accessed his digital identity from a Samsung Galaxy, a rare deviation from Hunter’s commitment to Apple products.
A week later Hunter’s account would begin to be accessed using the laptop that would ultimately end up with the FBI.
The traffic for just those three days looks like this, with the emails from Joey bolded and two key account changes italicized:
October 12, 12:56PM: As you requested, your temporary [AT&T] password is: ****** Use your user ID and temporary password to sign in to your account.
October 12, 12:56PM: Looks like you recently updated the AT&T password.
October 12, 12:57PM: Critical security alert for your linked Google Account, Sign-in attempt was blocked for your linked [RosemontSeneca] Google Account [device not specified]
October 12, 3:25PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 431] has been started
October 12, 3:32PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 431] has been started
October 12, 3:38PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 579] has been started
October 12, 3:40PM: Your [AT&T] insurance claim [phone ending in 96]
October 12, 3:44PM: Your [AT&T] insurance claim [phone ending in 13]
October 12, 3:49PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 701] has been started
October 12, 3:55PM: Please complete and return your claim documents Wireless Number: **94
October 12, 3:57PM: Thanks for using your AT&T Device Protection Plan! Your claim [ending in 799] has been started
October 12, 4:03PM: Please complete and return your claim documents Wireless Number: **29
October 12, 5:35PM: Hello. Review your AT&T order
October 12, 6:22PM: Good news. Your replacement device [grey Apple iPhoneX] has shipped. [phone ending in 13]
October 12, 6:24PM: Phone [from Joey]
Hey, You left your phone and other things. Tried to reach you at 202 and 302 all day but no luck. Let me know where to overnight.
October 12, 7:20PM: Good news. Your replacement device [iPhone 8] has shipped. [phone ending in 96]
October 12, 8:00PM: Verify your Samsung account [accessing Hunter’s iCloud]
October 12, 11:31PM: Someone Just Checked Your Background Report
October 13, 7:10AM: You left your phone. How do I get it to you?
joey
October 13, 7:26AM: You left your phone. How do I get it to you?
joey
October 13, 11:13AM: Let’s setup your AT&T replacement device [phone ending in 13]
October 13, 12:35AM: Someone Just Checked Your Background Report
October 13, 2:00PM: Hello, Review your AT&T order [changes to wireless]
October 13, 9:17PM: Your [RosemontSeneca] Google Account was just signed in to from a new Samsung Galaxy Note 9 device
October 13, 11:36PM: Wells Fargo Has Registered Your Mobile Device
October 14, 2:24PM: Your Apple ID password has been reset
October 14, 2:24PM: Your Apple ID was used to sign in to iCloud on an iPhone X
October 14, 3:28PM: Wells Fargo card added to Apple Pay
October 14, 3:36PM: Verify your Samsung account [on iCloud]
October 14, 7:48PM: “Overcoming myself” [from Joey]
When you have a minute, read ….
Open my shared note:
Interspersed with this traffic, Hunter’s accountant was trying to get him to file his 2017 taxes, Twitter was informing him of this story showing that Jared Kushner hadn’t paid taxes for years, Hunter was draining his bank account one $800 withdrawal after another, and his business partner was approving a payment to Hunter’s lawyer that would all but drain the Hudson West business associated with CEFC. A different business partner, Eric Schwerin, was also pushing Hunter to resolve their business interests during the 2018 tax year, something he failed to pull off.
Without the location and IP addresses, it’s not entirely sure what happened here (Weiss should have that with the iCloud data). It’s not even clear that Hunter had a phone, at all, between the time he lost his phones, plural, on October 11 and started using his new iPhone X on October 14 (though he did have a third phone tied to an account he used with sex workers). Hunter may have used the Samsung as a temporary phone for those two days or borrowed someone else’s Samsung to check his email; but it wasn’t verified to his iCloud account before October 14 at 3:36PM, and so may not have been able to access some Apple services. Importantly, however, that phone accessed his RosemontSeneca Google account after Hunter had started using one of his new replacement iPhones, something that doesn’t make sense if he was borrowing it.
If the texts to Hallie were sent after Hunter changed his wireless account at 2PM on October 13, they might be traced to a secure telephony account. But if they were sent via iMessage or WhatsApp before Hunter changed his iCloud password at 2:24PM on October 14, then you’d have to use location and IP data to rule out that someone else sent those texts to Hallie, using Hunter’s still accessible iCloud account via his lost phones (plural, apparently).
Because this particular verification challenge involves iCloud, which should have the location and IP data to verify which devices were used, and because (unlike the sex workers) it wouldn’t involve Hunter’s copresence with someone accessing his bank account via biometrics that others might access if he were wasted, this should be something that prosecutors could definitively prove, if indeed Hunter did send these texts.
If they can’t prove the location and IP from which these texts were sent, they may not be admissible at all, because prosecutors may not be able to prove that they are, in fact, Hunter’s words and not those of someone using his lost phones.
If this goes to trial, it might be worth forcing prosecutors to go through the effort to prove Hunter did send the texts, because it not only demonstrates how uncertain this evidence can be five years after the fact, but it would also show that Hunter spent hours trying to reclaim his digital identity — possibly using the laptop that would end up in Ablow’s possession — during the period when, prosecutors would be arguing, he was sleeping [in] a car and smoking crack.
Plus, that process would demonstrate something else. First, note that Hunter never verifiably made efforts that he did in August (the day before the dual Venmo access) to shut down access others would have via those lost devices to his digital identity. There’s no evidence here that Hunter deleted those phones, as he had only just finished doing weeks earlier with an iPad taken in August. That is, if Joey or whoever had one or two phones that Hunter had been using for weeks or months, there would be a great deal of data on them that would allow them, or anyone who subsequently got the phones, to carry out a much more systematic compromise of Hunter’s digital identity in the future.
There’s also no evidence that Hunter changed passwords besides the AT&T one, including for the RosemontSeneca email account that hosted all the work emails that would become so controversial years later. If he didn’t do that, then at least one of those two lost phones could likely access that account without interruption.
I’m not yet ready to show it, but this process, the incomplete effort to reclaim his digital identity, continued through the period where Hunter’s account started being accessed by a new laptop on October 21. And, depending on how the progression from prosecutors’ initial August 2019 iCloud warrant to the December 2019 warrant for that same laptop itself to the warrant to expanded scope of Hunter’s iCloud in July 2020 culminating in December 2023 in the use of those iCloud texts to substantiate a gun case occurred — something that Derek Hines deliberately obfuscates in this same filing — it may mean that this entire investigation has been built on this impossibly rocky foundation since 2019.
The laptop that FBI started using as evidence without first fully validating it destroys chain of custody not just because it was accessed by a hostile person over the course of months before being delivered to the FBI, but also because Hunter’s use of it would have been built on a digital identity that was totally compromised.
Normally, financial records are what make tax cases easy to prove (and, to be sure, many of the financial records used for Hunter’s tax indictment will be easily verifiable). Normally, these kinds of digital communications are what make other indictments easy to prove without having to rely on a sympathetic witness like Hallie Biden, one personally implicated in the insecure disposal of a gun.
But even ignoring the likelihood that more nefarious people might have compromised Hunter’s identity in this period (for which these is some evidence), Hunter’s addiction meant that his digital identity was persistently in a state of half-compromise through this entire period. His addiction led him to do things that prosecutors have now charged him for. It also adds a good deal of validation challenges for the kind of evidence that normally is routine.




A reminder to all new and existing community members participating in comments:
— We have been moving to a new minimum standard to support community security over the last year. Usernames should be unique and a minimum of a minimum of 8 letters.
— We do not require a valid, working email, but you must use the same email address each time you publish a comment here. **Single use disposable email addresses do not meet this standard.**
— If you have been commenting here but have less than 1000 comments published and been participating less than 10 years as of last October 2022, you must update your username to match the new standard.
Thank you.
” Importantly, however, that phone accessed his RosemontSeneca Google account after Hunter had started using one of his new replacement iPhones, something that doesn’t make sense if he was borrowing it.”
If Hunter borrowed that phone to access his online accounts, the Google one,Samsung likely will save the credentials, if Hunter didn’t “BOTH” sign out of Google and then “Remove” that account from Google’s login portal, then it’s entirely possible that Hunter’s Google account was accessed, possibly unintentionally, by the owner of the Samsung.
Any indication of the time frame in hours and minutes that hunter was signed into Google on that 2nd Samsung (Not Hunter) sign-in?
None. I’m working from the email alerts.
DOJ should have this all, and so presumably Hunter got it in discovery. But with their confession that they never accessed the iCloud for gun crime data, it is exceptionally likely no one at DOJ has done that kind of analysis — to see whether accounts were left open.
Thanks…more will be revealed I guess. What an Ogre…err, Shrek, errr…onion of a case. Keep peeling away the many layers.
Also, thanks for all you do as well.
Proving which phone was used is really complex. In networking each ‘port’ (maybe a physical port with a plug, maybe an antenna, if using WiFi) has a unique identifier called a MAC Address, which is twelve hexadecimal numbers, like this: 45:AF:09:32:B8:E2. (Sometimes colons are omitted, like this: 45AF:0932:B8E2 or even this: 45AF0932B8E2.)
Cell phones have two MAC Addresses, one for the cellular system which is usually assigned dynamically, plus a WiFi Mac address usually built into the hardware (which might be changeable in software.) To prove which phone sent a text you need the MAC Address of that particular phone, which might be either the cellular (dynamically assigned) or the hardware WiFi MAC Address… Worse, for the prosecution that MAC Address is only visible to the first router the phone connects to, out of maybe a dozen routers used for a cross-country Internet connection, possibly involving half-a-dozen companies, each with their own procedures, logging and privacy policies.
Oh! You need five-year-old router logs to prove your case? Have fun, particularly if other countries are involved! (Logs only need to be retained for a year in the U.S., per my very brief attempt to research this.)
That’s if these were telephony texts?
MAC Addresses are ubiquitous in the networking world, and any network packet, regardless of whether it involves text, voice, Telnet, FTP, SSH, or HTTP or HTTPS (the last two are used with Internet browsers, like Firefox) will include the originating and destination MAC Address. This goes for phones, tablets, laptops, desktops and servers.
If you want to know more about this you can study the 7-Layer OSI model of networking, which is essentially the ‘reference implementation’ for networking, and the 5-Layer Cisco model of networking, (a descendant of the OSI model) which is the one mainly used in the real world. Older versions of networking exist, going back at least as far as the version used at PARC Xerox in the 1970s, but in the OSI model of networking and it’s descendants are the primary form of networking in use today. All modern cellular service is essentially Voice Over Internet Protocol (VOIP) or just plain Internet when it’s not carrying an actual phone call.
Note that I’m using the word ‘packet’ colloquially. Depending on which network layer we’re discussing it might be a ‘packet,’ ‘segment’ or ‘frame,’ and these are the main things that need to be understood to know how something might be identified.
Actual POTS (Plain Old (analog) Telephone Service) uses a different model/set of standards.
All this being said, there may be other ways to prove that Hunter sent the messages, but the MAC Address is pretty fundamental and a great way for Lowell to raise doubts if he wishes to.
The MAC address is not included in a TCP/IP packet as you describe.
The only identifying info in the packet is the source IP address — which is often shared by multiple users, and also changes frequently (especially on mobile networks). The carriers are frequently subpoenaed for address-time-customer details.
The MAC address is only used on the local network, it does not travel past the first layer 3 router.
Clarifying though — on WiFi and mobile networks, the local network/broadcast domain is large and untrusted. Your MAC address can be harvested by any listener in range, and this is used for many bad things.
But the recipient of your HTTPS TCP/IP packets (e.g. Google) does not know your MAC address and has to fall back to other identification tricks, with your involvement/consent, or without.
Such as Browser ID, but if someone were using Hunter’s devices with cookies on them, they’d still come in under his Browser?
At the service level (e.g. iCloud), identification would be via an authentication token (app) or cookie (browser). That determines the account logged in, and (somewhat weakly) the device used, but of course not the operator of the device.
This token/cookie would be correlated to an IP address which would (weakly) suggest the device’s physical location.
And if someone just picked up Hunter’s phone, unlocked it via his (passed out) Face ID, they would appear to be him in all ways to all parties.
Logins to his account from multiple locations could be misuse by another person, or could be the vagaries of IP address allocation (or VPN etc) depending on the details.
The combination of password resets, multiple devices, and multiple locations in condensed time all lead me to a conclusion of a likely account takeover attempt, and apparent success.
Passed out Face ID won’t work. Both eyes must be open.
If Google account were being used the Ad ID associated with the device may link browser, cookies, and MAC IDs — but whether the Google Ad ID activity is still available is up in the air.
ADDER: It’s an Apple so I’m less familiar with location services but I wonder if it’s possible location could be paired with browser activity and other non-Apple services like Google account location and Google Ad ID.
As I noted elsewhere, I was using the word ‘packet’ casually. Technically the source and destination MAC Addresses are in the frame, but you’ve got to be pretty deep into networking to even know the word, so I said ‘packet’ instead. I noted that at 2:26 in the very same post you’re replying to.
Fair point. I wanted to be careful because at the depth of detail that was under discussion, there seemed to be some confusion about that data would be available or dispositive.
No prob. It’s definitely a complex issue revolving around a complex subject.
Need to rule out version iOS 14/higher or the setting for private MAC address applied because Wi-Fi could assign private MAC for each new network used.
https://support.apple.com/en-us/102509
The laptop shared with the FBI was iOS 14.
Not sure what the Ablow laptop was — probably the same, tho.
Welp…
Not to mention iOS phones have (3) MAC addresses, one for each network interface — cell, bluetooth, and Wi-Fi (which can apparently be more than one if iOS 14 or later).
Android adopted the randomization of Wi-Fi MAC addresses in Android 10.
After Snowden revealed that the NSA was harvesting MAC addresses from scanning WIFI connection requests in metropolitan areas, the industry started randomizing MAC addresses beginning with Apple. Not sure if they even use MAC addresses for cellular connections or if such connections are packet switched. The main problem with using a MAC address as a unique identifier is that they are local vs TCP/IP which is global, and MAC addresses only need to be unique to that area of the network.
MAC address is hardware identity unless virtualized like iOS 14 randomization for Wi-Fi network only. The handset itself still has the same MAC.
Traditionally, that’s true. However, the networking industry has been moving away from that due to security concerns.
I’m going to point you right back to Apple and ask you to note c a r e f u l l y what this says and doesn’t say:
https://support.apple.com/en-us/102509
Private address for the Wi-Fi network interface — an address available on a Wi-Fi network — yes. Abso-fucking-lutely no mention of the unique MAC address for the handset set, no mention of the MAC address for the Bluetooth interface.
Each device has a unique hardware ID, but this is not visible to app software, and is not sent over the network.
MAC addresses are attributes of network interfaces. Each network interface has one or more unique MAC addresses. This is how the device identifies itself on the local network. If the IP address is your mailing address (1600 Penn Ave), the MAC address might be the map and lot number on the county real estate records (Wash DC, Map 99, Lot 4A). All can be set by software nowadays, but MAC used to be burned into the hardware ROM.
Randomizing the WiFi network interface MAC address is good but not adequate if your eavesdropper is nearby and you have Bluetooth enabled. I think your analysis is correct that BT MACs are not randomized on iOS, and that that is a risk.
Note that you cannot harvest the content of the messages (they are encrypted) but you can identify the talkers. I think that randomizing BT MAC address would break pairing of your devices.
I think the laptop would have been OS-10.something, which is the Apple OS for computers, not IOS, which is the Apple OS for phones and tablets. (I don’t pay a lot of attention to the Apple world, so consult with a current Apple user on this – stuff may have changed since I was last able to give an accurate answer about Apple gear.)
OS-10 was originally built on top of a BSD Unix, which makes certain technical assumptions possible, though not necessarily accurate… drift has probably occurred, so once again, a current Apple user should be consulted, but if you assume a Mac is running UNIX under the hood you won’t be too far wrong.
iOS 14 would be on an iPhone, not a laptop. Did you mean OS X 10.14?
I did.
OTOH
“iPhones have been exposing your unique MAC despite Apple’s promises otherwise.”
https://arstechnica.com/security/2023/10/iphone-privacy-feature-hiding-wi-fi-macs-has-failed-to-work-for-3-years/
Agreed except for some nitpicks which aren’t worth recording. MACs on Macs are a very complex issue and I’ve only scratched the surface. But the problem of identifying the five-year-old phone as the one in HB’s possession on a particular dateis fundamental to proving who sent the texts and it won’t be easy. If the phone was assigning itself random MAC Addresses, does the log about what address was assigned on what day still exist? For that matter, does the phone still exist, either physically or in software (as in did someone do a hard-reset at some point?)
Leaving MAC addresses aside, there might be other ways to prove who/where the messages came from, but once again, are there still logs available?
The first question I have is physical proof of human bodies on location if Wi-Fi was used. Who was in the building and when.
No arguments. There are a number of questions which need to be answered about these text messages in order to prove/disprove anything.
BTW, apropos of nothing but pure geekiness, did you know that Ken Thompson has publicly abandoned Apple for Linux, which he mainly runs on Raspberry Pis? I saw him in person at a Linux convention and he discussed this in some detail! I was quite stoked.
Right. That’s sort of what I was thinking. But that would only be true if Hunter were texting (iMessage) Hallie from laptop inside Dad’s home or something. Unlikely.
Thumbs up on the leading paragraph. I needed that chuckle. Regarding the rest, I see plenty of reasonable doubt here working in Hunter’s favor.
Brilliant work by EW, Troutwaxer, et al.! I feel privileged to be a regular, highly informed reader of the Comments at EmptyWheel.net! The discussion of MAC addresses, etc. above is so informative, I hope Hunter Biden’s defense attorneys are reading this. Since the Hunter Biden “laptop” story broke, I have been telling anyone who will listen, that proving anything in a court of law using the e-mails and texts obtained from this laptop or series of hard drives, was going to be problematic! IANAL, but I was a CPA who used to do forensic accounting and the chain of custody on the hard drives is so utterly compromised as to be inadmissible. Not to mention Mr. Magoo at the Pretty Good Computer Repair Shoppe violated Delaware escheat laws by appropriating Mr. Biden’s equipment without public notice and too soon (less than one year). I hope the judge throws it all out.
Maybe I am overactive in my imagination but within foreign intelligence services around the world, there must be something like a file for the hundred or so most politically influential Americans that includes their family members to see if any turn up potentially vulnerable to influence or compromise. We have already had one Presidential impeachment which originated in a rat f#cking operation on Hunter Biden. Isn’t it about the same time they are doing this that Hunter is descending into coke and sex addicted madness? Guilliani’s Ukrainian and Russian operation was trying to put together the Burisma scandal, Hunter Biden, the subject himself, is a coked up sex addict losing iphones and laptops all over the place and Guiliani’s operatives and Putin’s operatives don’t know? In the movable feast entourage of Hunter Biden’s life at the time, who is accessing Hunter Biden’s Icloud account? Where is the counter-intelligence investigation is I think what you mean, Marcy, by “Those potential compromises should have elicited an entirely different investigative focus”. Somebody made all these laptops or disk images of laptops I don’t know which.
The structure and manner of David Weiss’ prosecution of Hunter Biden seems like another version of what we saw with the Durham investigation of Michael Sussman. It is an unusual prosecution in that another person would not likely face these charges with the same fact set. And there is also the same willful blindness when obvious counterintelligence implications color all the evidence.
“Where is the counter-intelligence investigation is I think what you mean, Marcy, by “Those potential compromises should have elicited an entirely different investigative focus”.”
Agreed completely!
[FYI – your broken HTML fixed. /~Rayne]
Thank Rayne!
The network ID details and message timing along with device position location and history will be important for Hunter’s legal defense but since the background political goal of the prosecution is ostensibly keeping “the Biden crime family” in the news, what are the chances this case gets decided before November ’24?
I can’t stop being amazed by the double standard involved with the Hunter Biden gun prosecution. This morning, while reading news of the drug OD death of Adam Harrison, the son of Pawn Stars celeb and Trump supporter, Rick Harrison, I was remined of another star from that show: “Chumlee” Russell.
https://people.com/crime/pawn-stars-austin-chumlee-russell-had-12-guns-and-meth-in-home/
This guy got popped with 12 guns in his home and a bunch of drugs. He got off with three years probation. The show which made him famous has gun sales as one of its main features. Now it appears that Chumlee wasn’t the only person associated with that gun dealer who did drugs. Lord knows how many others from the cast are also users. But Hunter Biden, who was not arrested, not caught possessing drugs, never busted with a gun in his possession, is facing many years because he wrote a memoir admitting to his earlier addiction.
It’s okay for Republican drug users to sell guns, but it’s not okay for Dem addicts to buy them? Bizarre.
The unmitigated gall of Donnie Jr. in this TMZ piece on Harrison’s death:
https://www.tmz.com/2024/01/19/pawn-stars-rick-harrison-son-adam-dead-dies-overdose/
He’s sorry a celebrity’s son OD’d and died, but he’s a total dick about a VP/POTUS’s son who survived addiction.
https://www.washingtonexaminer.com/news/2791968/trump-jr-hunter-biden-refusal-appear-congress-iowa/
I am beginning to wonder about the level of tolerance for prosecutorial misconduct in the case of Hunter Biden.
Maybe it’s the homebrew but this seems to be apropos: https://www.youtube.com/watch?v=7PCkvCPvDXk
Here are some other data points, hopefully relevant. As it appears Hunter has 3 phones at any given time, on top of whatever burners, text apps, borrowed devices. 2 primary that he keeps at all times, possibly 1 business and 1 personal, but that gets blurred. And another of the phones is Joe’s old phone.
10/5/18 Hunter flies from LA to East Coast
10/7/18 a friend in LA says he’s checking on him via iMessage through email [not sure if phone is already lost and that’s why not using phone text]
10/13/18 8:15am Hunter begins using an old phone number that was at some point ex-wife’s primary number, texting a family member that he is waiting for his other phone by mail, possibly the one with Joey or maybe a newly ordered device
10/13/18 Hunter tells a family member he needs his computer (not sure which computer he is referring to. At some point during this time frame he leaves a computer at a family member’s house and there’s drama to get it back)
10/13/18 9:30pm connects an iPhone 8 to Apple ID per Dimitrelos (might be the ex wife’s old phone?)
10/14/18 Hunter texts a family member he just left AT&T and cites his number as a completely different number
10/16/18 texts family member he still needs his computer and asks them to bring out, and that per the family member’s prior suggestion that he replace his laptop because its broken, he listened then and immediately replaced his broken laptop (not sure which laptop either was)
10/17/18 7:01am Hunter makes the ex-wife’s number the Trusted number for Apple ID
10/17/18 11:48am texts a friend he lost his phone and hasn’t downloaded contacts yet
10/28/18 Hunter texts his lost phone number that has an LA area code “Who has my phone?”; no response
It really is about time American politicians got back to work on the real issues facing their country. What the Presidents son is doing or not doing, really. He had a disease and did some very unwise things, but it is a disease which caused the problems.
If they found Biden’s son’s computer with some one who it did not belong to it is interesting no one checked to see if it had been stolen. As to the pictures on it, who cares. Showing them around is simply wrong, an invasion of privacy, and bat shit crazy.
Buying a gun and doing drugs. It isn’t the smartest thing to do, but I’m sure there are millions of Americans who are high and in possession of guns and even kill people and a lot of that seems to be just O.K. Biden’s son was ill so yes, his behaviour is going to be off, but this carry on, is a bit much
I know that things that are evidence have to be kept in a safe place, without others accessing them. So how is that going to work in Hunter Biden’s case, where his computer was found some where else.
A few points/questions
1) How certain are you that he lost his phone (or phones) October 11? As opposed to days before or weeks? Is the timing of the email from Joey the main indicator or are there other data points?
2) timestamps for the emails cited by Weiss
10/13/18 10:30pm EST= meeting Mookie
10/14/18 5:37pm EST = sleeping on a car
They appear to be regular texts sent using the phone previously used by his ex wife ( ending in 73). I can’t say with certainty but I believe that to be the case.
3) the 10/14/18 email from Wells Fargo Online added Apple Pay, what email was that sent to? On Marco Polo it says “email redacted”. It’s bizarre to me that sometimes they redact stuff but other times don’t
4) the AT&T timeline looks interesting, I need to double check to follow along. I did notice it appears he switched to T-Mobile on 10/2/18 based on texts received, but then switched back to AT&T, likely due to losing phones.