Right wing purveyors of the Hunter Biden “laptop” story say that John Paul Mac Isaac, the legally blind computer repairman who made a copy of a laptop that he said Hunter Biden dropped off, then sent a copy of the data to Rudy Giuliani, was perfectly entitled to do so. They point to the intake form JPMI used, stating that,
Equipment left with the Mac Shop after 90 days of notification of completed service will be treated as abandoned and you agree to hold the Mac Shop harmless for any damage or loss of property.
In Hunter Biden’s countersuit against JPMI, he noted that Delaware law only deems tangible personal property to be abandoned after a year, and requires some bureaucracy before someone can assert to own the property.
8. Contrary to Mac Isaac’s Repair Authorization form, Delaware law provides that tangible personal property is deemed abandoned when “the rightful owner has left in the care or custody of another person and has failed to maintain, pay for the storage of, exercise dominion or control over, and has failed to otherwise assert or declare the ownership rights to the [] property for a period of 1 year.” (25 Del. C. § 4001) (emphasis added). The procedure to obtain lawful title to abandoned personal property requires the person in possession of the property to file a petition in a court of competent jurisdiction. (25 Del. C. § 4003). Other obligations must then also be satisfied before obtaining lawful title, such as the court sending notice to the owner and the petitioner posting notice in five or more public places, and advertising the petition in a newspaper. (25 Del. C. § 4003(b)). [emphasis original]
The requirements of Delaware law have attracted the most attention amid debates whether JPMI was entitled to share the laptop with Rudy Giuliani.
More important to questions of Computer Fraud and Abuse Act lawsuits like the one Hunter filed against Rudy Giuliani, however, Abbe Lowell notes that JPMI’s intake form promises to “secure [his customers’] data.”
12. Moreover, even if the Repair Authorization form were enforceable under Delaware law, by its own terms, it provides abandonment of only any “equipment” that is left behind at the Mac Shop, and not the data on or embedded within any such equipment. In fact, the Repair Authorization form states that the Mac Shop will make every effort to “secure your data.” (Compl. Ex. A). Customers who sign Mac Isaac’s Repair Authorization form do not, therefore, waive any rights under Delaware law for the data that any equipment might contain. Reputable computer companies and repair people routinely delete personal data contained on devices that are exchanged, left behind, or abandoned. They do not open, copy, and then provide that data to others, as Mac Isaac did here.
13. At no time did Mr. Biden grant Mac Isaac any permission to access, review, copy, or disseminate for his own purposes any electronically stored data that ever was created or received or maintained by Mr. Biden (regardless of how Mac Isaac came into possession of such material). [my emphasis]
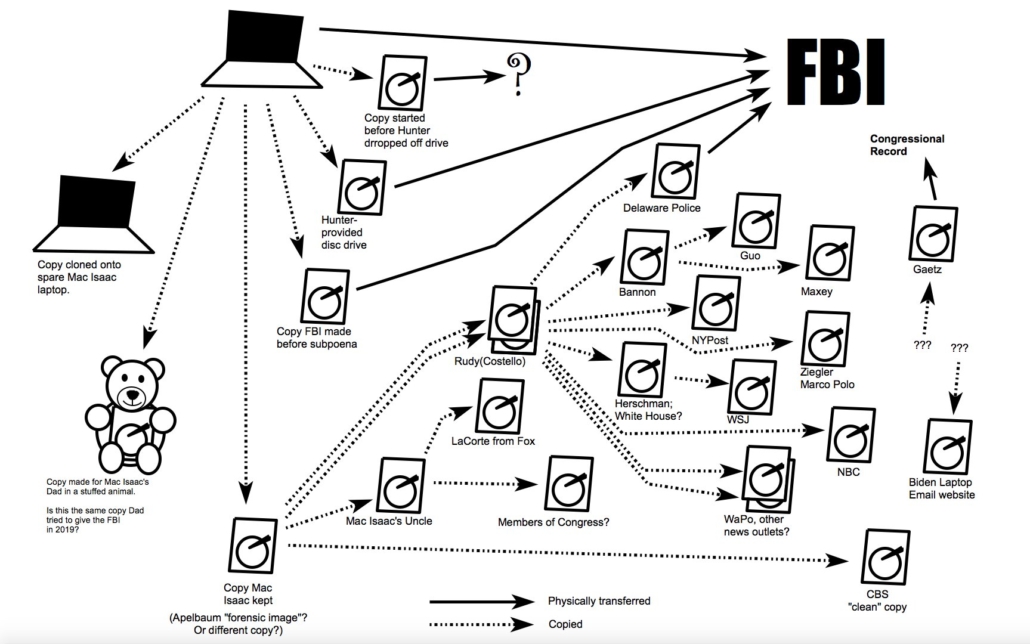
Hunter Biden did not, if he indeed signed that intake form, authorize JPMI to grant other people access to his data. Yet JPMI gave it to Rudy who gave it to half the world, including the NY Post, as this illustration from Thomas Fine lays out.
There are multiple theories of CFAA that Abbe Lowell might have in mind as he sues those who’ve disseminated Hunter’s data: I discussed that cracking the password of the iPhone stored on the device or accessing data stored in the cloud might qualify. It’s also possible, however, that Lowell would argue that simply accessing the drive that JPMI shared amounts to unauthorized access, even under JPMI’s own intake form, because he said he would keep the data secure.
Those details will undoubtedly be a part of all the litigation going forward.
But there’s another detail about the intake form that deserves more attention. JPMI didn’t identify the laptops that were dropped off, beyond simply saying they were three MacBook Pros.
JPMI doesn’t claim to have paperwork tying a serial number to any of these three laptops until the FBI put one, for the laptop given to the FBI, on a subpoena in December 2019.
JPMI doens’t claim to have proof that the laptop he would go on to give to the FBI — some of the contents of which he shared with Rudy Giuliani who then shared it with half the world, including the NY Post — was the laptop he claims someone dropped off on April 12, 2019.
Normally, that would not be a big deal. But, as described in his book, the laptop he gave the FBI does not match any of the three laptops he claims were dropped off on April 12, 2019.
One at a time, I performed a quick inspection of the machines. The fifteen-inch laptop was a complete write-off. It had extensive liquid damage, and because the drive was soldered to the logic board, data recovery was beyond my capability. (If a Mac can’t power on, you won’t be able to access the drive and get to the data.)
The thirteen-inch 2015 MacBook Pro was in slightly better shape. It could boot up, but the keyboard was unresponsive. I pulled out an external keyboard and asked for permission to log in.
[snip]
I moved on to the last Mac, a thirteen-inch 2016 MacBook Pro. The drive was soldered onto the logic board. This one powered on but then would shut down. I suspected that there was a short in the keyboard or trackpad, and if I took it apart, I could at least get it to boot and possibly recover the data.
JPMI described three machines:
- A 15″ laptop, of unknown date, with soldered drive
- A 13″ laptop from 2015
- A 13″ laptop from 2016 with a soldered drive
By description, JPMI claims the last one is the one he gave to the FBI.
Based on the serial number, the laptop turned over to the FBI is a 13-inch 2017 PowerBook purchased in October 2018 (the October 2018 purchase date is consistent when it was added to Hunter’s Apple account).
It can’t be the first laptop described here, because it’s a 13″ PowerBook, but it’s a different year — 2017 rather than 2015 or 2016 — than both the 13″ PowerBooks JPMI described.
The difference in year might be no big deal.
The other description JPMI gives about the laptop he claims to be the one he recovered is: According to several people who’ve checked, the laptop shared with the FBI has a removable hard drive.
The entire reason why JPMI claims to have copied the files in the manner he did — by dragging-and-dropping files — is because he didn’t have ports to plug both a keyboard, power, and a cable to his own server. Instead, he plugged in the server and a keyboard, and did the drag-and-drop in three passes, recharging the battery between each pass.
That’s what, he claims, led him to look at Hunter’s files more closely, starting with dick pics and moving onto an “income” document conveniently marked with a purple dot.
Finally, I went in the back to check on Hunter’s liquid-damaged MacBook Pro. It had powered off, dying overnight during the file transfer. I now realized that this was not going to be a simple drag-and-drop procedure. There was about three hundred gigabytes’ worth of data, but not enough charge in the battery to do it all in one go. I started to charge the unit again, planning to give it a couple of hours before making a second attempt. But I also decided to see what had been successfully transferred to the server, praying I didn’t have to start all over again.
[snip]
I changed the folder view to a columns view, to see the files and folders in an alphabetical list. Clicking on a folder in the list opens up a new column with the contents of the folder, and clicking on a file in that column brings up a preview of the file. Eventually, in two separate windows, I would be able bring up both the original desktop and what I had copied, compare them, and transfer the missing files to the recovery window. But first I had to wait until there was enough of a charge in the battery to power on the Mac and keep it on.
[snip]
Here’s where things started to get interesting.
The previous recovered window was open on the left, and I was waiting for the hundreds of files on the original to populate to the right. Scrolling down, I started to see files that didn’t align. I started to individually drag and drop the files to the recovery folder. It took only a few files before I noticed pornography appearing in the right column.
[snip]
I continued copying files until I got to one titled “income.pdf.” I likely wouldn’t even have noticed it if it hadn’t been tagged with a purple dot. On a Mac, you can apply tags, or color codes, to files as an organizational aid. It seemed odd that someone who clearly had zero organizational skills would bother tagging this one file purple. It was begging to be clicked open. So I did.
But once JPMI realized the battery was draining, he could have simply swapped the hard drive into a separate laptop, with functioning keyboard, to copy the files that way.
Indeed, that seems to be (per Gary Shapley’s notes) what the FBI did: just put the hard drive in a new laptop.
FBI determined in order to do a full forensic review a replacement laptop had to be purchased so the hard drive could be installed, booted and imaged.
[snip]
c. Lesley said (while laughing) that because a lot of p[e]op[l]e are going to be asking for the laptop
d. Josh Wilson stated that (while laughing) so whoever they are they are going to have to buy a laptop to put the hard rive in so they can read it [fixed errors in people]
Once you understand the laptop had a removable drive, then JPMI’s excuse for snooping in Hunter’s private files disappears.
But here’s why I can’t stop thinking about the fact that JPMI has no proof of which laptops he received and the laptop described in his book doesn’t match the one he shared with the FBI. One explanation for this discrepancy is ineptitude: during the entire period he was writing the book, he never even consulted the subpoena (the data for which he had provided the FBI). Another is he needed to invent an excuse, after the fact, to explain why he was reading Hunter’s stuff.
But there’s one other potentially related issue.
There aren’t three laptops. There are at least four.
The fourth is the laptop found at Keith Ablow’s in 2020, the one reportedly discovered after Hunter Biden left in February 2019. That laptop is reportedly one that Hunter first signed onto on September 1, 2018, at 10:34AM PDT, also a 13″ MacBook Pro, but one with a touch bar. The next day, Apple emailed Hunter to tell him he had gotten a new laptop — something that didn’t happen for many of his other new devices (including the one that first accessed his iCloud account in October 2018, the one that would end up with the FBI).
If that’s correct, then Hunter initiated the laptop left at Ablow’s in February 2019 in September 1, 2018. And the laptop ultimately shared with the FBI was initiated on October 21, 2018. Though there were accesses to his iCloud and other accounts from new devices almost every week in this period, there’s no sign at all that the touch bar MacBook (as opposed to one after another iPhone and an iPad) had been lost or inactivated.
And if the activity that packaged up Hunter’s digital life happened on the same laptop that ended up in a computer repair shop in Wilmington, then both would be presumed to be at Ablow’s in the same period in late January to early February. That’s an odd occurrence in the first place, since Hunter was going to get treatment, not to work on his memoir. But it’s also odd that the laptop ultimately shared with the FBI stopped synching on the same day that a laptop — possibly the Ablow one? — was purportedly deleted.
There are two problems with this story. None of the three laptops that JPMI describes receiving is the one shared with the FBI. And there’s not a good explanation for why two Hunter Biden laptops would be at Ablow’s property and why the one presumably in Hunter’s presence would stop synching the same day some other laptop was deleted.
This is all background for another post. But one thing that’s clear is none of the laptops JPMI describes in his book can be the one shared with the FBI. And there’s another laptop out there, which would have been present in the same place and time as the laptop that ultimately was shared with the FBI.