John Paul Mac Isaac’s Serial Inaccuracies and the Ablow Laptop
Right wing purveyors of the Hunter Biden “laptop” story say that John Paul Mac Isaac, the legally blind computer repairman who made a copy of a laptop that he said Hunter Biden dropped off, then sent a copy of the data to Rudy Giuliani, was perfectly entitled to do so. They point to the intake form JPMI used, stating that,
Equipment left with the Mac Shop after 90 days of notification of completed service will be treated as abandoned and you agree to hold the Mac Shop harmless for any damage or loss of property.
In Hunter Biden’s countersuit against JPMI, he noted that Delaware law only deems tangible personal property to be abandoned after a year, and requires some bureaucracy before someone can assert to own the property.
8. Contrary to Mac Isaac’s Repair Authorization form, Delaware law provides that tangible personal property is deemed abandoned when “the rightful owner has left in the care or custody of another person and has failed to maintain, pay for the storage of, exercise dominion or control over, and has failed to otherwise assert or declare the ownership rights to the [] property for a period of 1 year.” (25 Del. C. § 4001) (emphasis added). The procedure to obtain lawful title to abandoned personal property requires the person in possession of the property to file a petition in a court of competent jurisdiction. (25 Del. C. § 4003). Other obligations must then also be satisfied before obtaining lawful title, such as the court sending notice to the owner and the petitioner posting notice in five or more public places, and advertising the petition in a newspaper. (25 Del. C. § 4003(b)). [emphasis original]
The requirements of Delaware law have attracted the most attention amid debates whether JPMI was entitled to share the laptop with Rudy Giuliani.
More important to questions of Computer Fraud and Abuse Act lawsuits like the one Hunter filed against Rudy Giuliani, however, Abbe Lowell notes that JPMI’s intake form promises to “secure [his customers’] data.”
12. Moreover, even if the Repair Authorization form were enforceable under Delaware law, by its own terms, it provides abandonment of only any “equipment” that is left behind at the Mac Shop, and not the data on or embedded within any such equipment. In fact, the Repair Authorization form states that the Mac Shop will make every effort to “secure your data.” (Compl. Ex. A). Customers who sign Mac Isaac’s Repair Authorization form do not, therefore, waive any rights under Delaware law for the data that any equipment might contain. Reputable computer companies and repair people routinely delete personal data contained on devices that are exchanged, left behind, or abandoned. They do not open, copy, and then provide that data to others, as Mac Isaac did here.
13. At no time did Mr. Biden grant Mac Isaac any permission to access, review, copy, or disseminate for his own purposes any electronically stored data that ever was created or received or maintained by Mr. Biden (regardless of how Mac Isaac came into possession of such material). [my emphasis]
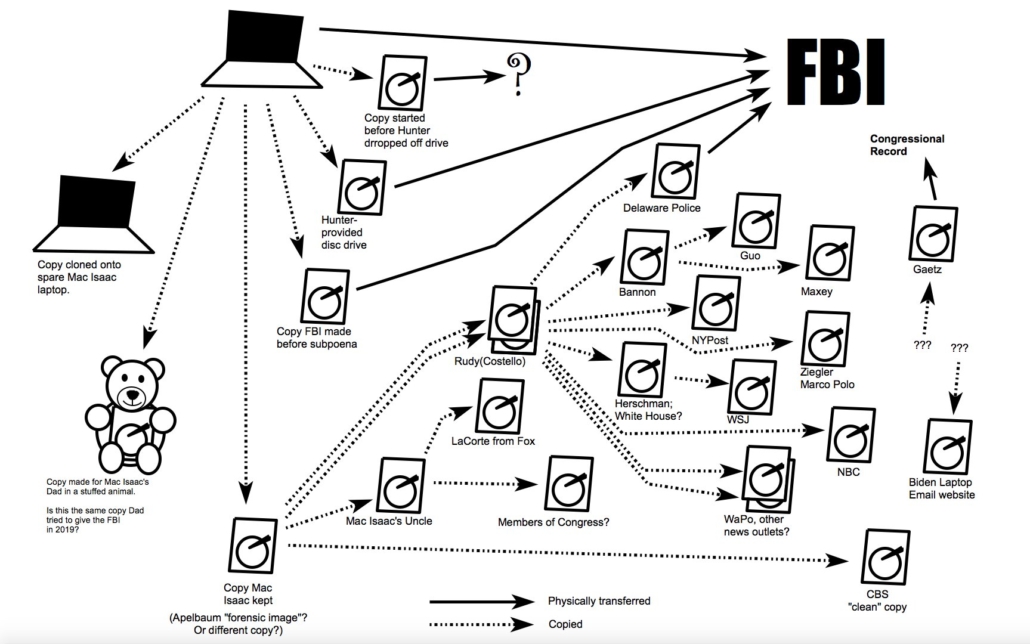
Hunter Biden did not, if he indeed signed that intake form, authorize JPMI to grant other people access to his data. Yet JPMI gave it to Rudy who gave it to half the world, including the NY Post, as this illustration from Thomas Fine lays out.
There are multiple theories of CFAA that Abbe Lowell might have in mind as he sues those who’ve disseminated Hunter’s data: I discussed that cracking the password of the iPhone stored on the device or accessing data stored in the cloud might qualify. It’s also possible, however, that Lowell would argue that simply accessing the drive that JPMI shared amounts to unauthorized access, even under JPMI’s own intake form, because he said he would keep the data secure.
Those details will undoubtedly be a part of all the litigation going forward.
But there’s another detail about the intake form that deserves more attention. JPMI didn’t identify the laptops that were dropped off, beyond simply saying they were three MacBook Pros.
JPMI doesn’t claim to have paperwork tying a serial number to any of these three laptops until the FBI put one, for the laptop given to the FBI, on a subpoena in December 2019.
JPMI doens’t claim to have proof that the laptop he would go on to give to the FBI — some of the contents of which he shared with Rudy Giuliani who then shared it with half the world, including the NY Post — was the laptop he claims someone dropped off on April 12, 2019.
Normally, that would not be a big deal. But, as described in his book, the laptop he gave the FBI does not match any of the three laptops he claims were dropped off on April 12, 2019.
One at a time, I performed a quick inspection of the machines. The fifteen-inch laptop was a complete write-off. It had extensive liquid damage, and because the drive was soldered to the logic board, data recovery was beyond my capability. (If a Mac can’t power on, you won’t be able to access the drive and get to the data.)
The thirteen-inch 2015 MacBook Pro was in slightly better shape. It could boot up, but the keyboard was unresponsive. I pulled out an external keyboard and asked for permission to log in.
[snip]
I moved on to the last Mac, a thirteen-inch 2016 MacBook Pro. The drive was soldered onto the logic board. This one powered on but then would shut down. I suspected that there was a short in the keyboard or trackpad, and if I took it apart, I could at least get it to boot and possibly recover the data.
JPMI described three machines:
- A 15″ laptop, of unknown date, with soldered drive
- A 13″ laptop from 2015
- A 13″ laptop from 2016 with a soldered drive
By description, JPMI claims the last one is the one he gave to the FBI.
Based on the serial number, the laptop turned over to the FBI is a 13-inch 2017 PowerBook purchased in October 2018 (the October 2018 purchase date is consistent when it was added to Hunter’s Apple account).
It can’t be the first laptop described here, because it’s a 13″ PowerBook, but it’s a different year — 2017 rather than 2015 or 2016 — than both the 13″ PowerBooks JPMI described.
The difference in year might be no big deal.
The other description JPMI gives about the laptop he claims to be the one he recovered is: According to several people who’ve checked, the laptop shared with the FBI has a removable hard drive.
The entire reason why JPMI claims to have copied the files in the manner he did — by dragging-and-dropping files — is because he didn’t have ports to plug both a keyboard, power, and a cable to his own server. Instead, he plugged in the server and a keyboard, and did the drag-and-drop in three passes, recharging the battery between each pass.
That’s what, he claims, led him to look at Hunter’s files more closely, starting with dick pics and moving onto an “income” document conveniently marked with a purple dot.
Finally, I went in the back to check on Hunter’s liquid-damaged MacBook Pro. It had powered off, dying overnight during the file transfer. I now realized that this was not going to be a simple drag-and-drop procedure. There was about three hundred gigabytes’ worth of data, but not enough charge in the battery to do it all in one go. I started to charge the unit again, planning to give it a couple of hours before making a second attempt. But I also decided to see what had been successfully transferred to the server, praying I didn’t have to start all over again.
[snip]
I changed the folder view to a columns view, to see the files and folders in an alphabetical list. Clicking on a folder in the list opens up a new column with the contents of the folder, and clicking on a file in that column brings up a preview of the file. Eventually, in two separate windows, I would be able bring up both the original desktop and what I had copied, compare them, and transfer the missing files to the recovery window. But first I had to wait until there was enough of a charge in the battery to power on the Mac and keep it on.
[snip]
Here’s where things started to get interesting.
The previous recovered window was open on the left, and I was waiting for the hundreds of files on the original to populate to the right. Scrolling down, I started to see files that didn’t align. I started to individually drag and drop the files to the recovery folder. It took only a few files before I noticed pornography appearing in the right column.
[snip]
I continued copying files until I got to one titled “income.pdf.” I likely wouldn’t even have noticed it if it hadn’t been tagged with a purple dot. On a Mac, you can apply tags, or color codes, to files as an organizational aid. It seemed odd that someone who clearly had zero organizational skills would bother tagging this one file purple. It was begging to be clicked open. So I did.
But once JPMI realized the battery was draining, he could have simply swapped the hard drive into a separate laptop, with functioning keyboard, to copy the files that way.
Indeed, that seems to be (per Gary Shapley’s notes) what the FBI did: just put the hard drive in a new laptop.
FBI determined in order to do a full forensic review a replacement laptop had to be purchased so the hard drive could be installed, booted and imaged.
[snip]
c. Lesley said (while laughing) that because a lot of p[e]op[l]e are going to be asking for the laptop
d. Josh Wilson stated that (while laughing) so whoever they are they are going to have to buy a laptop to put the hard rive in so they can read it [fixed errors in people]
Once you understand the laptop had a removable drive, then JPMI’s excuse for snooping in Hunter’s private files disappears.
But here’s why I can’t stop thinking about the fact that JPMI has no proof of which laptops he received and the laptop described in his book doesn’t match the one he shared with the FBI. One explanation for this discrepancy is ineptitude: during the entire period he was writing the book, he never even consulted the subpoena (the data for which he had provided the FBI). Another is he needed to invent an excuse, after the fact, to explain why he was reading Hunter’s stuff.
But there’s one other potentially related issue.
There aren’t three laptops. There are at least four.
The fourth is the laptop found at Keith Ablow’s in 2020, the one reportedly discovered after Hunter Biden left in February 2019. That laptop is reportedly one that Hunter first signed onto on September 1, 2018, at 10:34AM PDT, also a 13″ MacBook Pro, but one with a touch bar. The next day, Apple emailed Hunter to tell him he had gotten a new laptop — something that didn’t happen for many of his other new devices (including the one that first accessed his iCloud account in October 2018, the one that would end up with the FBI).
If that’s correct, then Hunter initiated the laptop left at Ablow’s in February 2019 in September 1, 2018. And the laptop ultimately shared with the FBI was initiated on October 21, 2018. Though there were accesses to his iCloud and other accounts from new devices almost every week in this period, there’s no sign at all that the touch bar MacBook (as opposed to one after another iPhone and an iPad) had been lost or inactivated.
And if the activity that packaged up Hunter’s digital life happened on the same laptop that ended up in a computer repair shop in Wilmington, then both would be presumed to be at Ablow’s in the same period in late January to early February. That’s an odd occurrence in the first place, since Hunter was going to get treatment, not to work on his memoir. But it’s also odd that the laptop ultimately shared with the FBI stopped synching on the same day that a laptop — possibly the Ablow one? — was purportedly deleted.
There are two problems with this story. None of the three laptops that JPMI describes receiving is the one shared with the FBI. And there’s not a good explanation for why two Hunter Biden laptops would be at Ablow’s property and why the one presumably in Hunter’s presence would stop synching the same day some other laptop was deleted.
This is all background for another post. But one thing that’s clear is none of the laptops JPMI describes in his book can be the one shared with the FBI. And there’s another laptop out there, which would have been present in the same place and time as the laptop that ultimately was shared with the FBI.




“…because a lot of poopie…”
I’d be laughing too.
Yikes. Fixed it. Damned OCR.
I had to have a hard drive – internal – copied once. Took it to an office-supply place with a repair ability, where they stuck it into a holder and copied the contents to a new (external) hard drive. They didn’t have to open any of the files, even if they did it one-by-one. (I’ve copied files that way. Opening them isn’t needed. It’s “save link as” in Windows.)
Pre-cloud, that would have been called making a back-up. Some users did that every day, week, or month, with one or more back-up drives, sometimes kept off-site for physical security reasons. If your computer went down or got bricked, you only lost what you did since the last back-up. A graphic artist friend, who doesn’t like to use the cloud, backs up every night, and keeps the back-up drive separate from his computer.
Opening up any files, which presumably changes them and the h/d to some degree, seems like a bullshit excuse, especially for someone supposedly in the computer repair business.
I also wonder about needing to charge the battery. I have owned about 8 or 9 MacBook Pros and they required lots of repairs (young grandchildren are tough on laptops). I do not remember ever having to have a charged battery. If the battery wasn’t holding a charge, plug it in and run off a wire.
As I understood that part, the laptop only had two ports (presumably two Firewire ports), and he needed one to connect an external keyboard and the other to connect a cable to his server. He was relying on the battery because there was no port left to plug it in.
I’m not an Apple aficionado, but I’d be highly surprised if it was not possible to start the back-up/transfer on battery power, then unplug the keyboard and plug in the mains power – Plug’n’play and all that being a key feature of Apple gear.
Yeah, that seems like it should have worked.
Unbelievable. A ‘mac’ repair guy that never heard of a ‘usb hub adapter’.
THIS! This is what hit my brain cells! A computer repair guy without a hub doesn’t exist in the real world! It’s a rubbish explanation.
I’ve tried not to be a backseat driver on JPMI and chain of custody, but this post and your comment give me the perfect chance to say, “JPMI might be a computer repair guy, but no one ever said he was a GOOD one” …
Fair! There are a lot of professional incompetents all around this situation.
Came here to say this. This computer guy is a total grifter, his explanations are ridiculously bad.
JPMI is supposed to be a computer expert. I don’t know a lot about Macs, but why wouldn’t he just connect a usb hub to one of the ports, then he can put two of the three needed cables (power, server, keyboard) in there.
Or he could charge the device, use one port for the cable to his server, other port for the keyboard and when the copying of the files is underway, then switch out the keyboard cable for the powercable.
JPMI is full of it.
JPMI is full of it beyond that. His book reads like a novel, at least the passage about cracking Hunter’s laptop. He describes his actions like he’s Philip Marlowe hired to find the embezzler at the illegal gambling club a case that of course turns into a murder mystery. Here’s the giveway that JPMI was deliberatly breaking into Hunter’s files:
“Scrolling down, I started to see files that didn’t align. I started to individually drag and drop the files to the recovery folder. It took only a few files before I noticed pornography appearing in the right column.
[snip]
I continued copying files until I got to one titled “income.pdf.” I likely wouldn’t even have noticed it if it hadn’t been tagged with a purple dot. On a Mac, you can apply tags, or color codes, to files as an organizational aid. It seemed odd that someone who clearly had zero organizational skills would bother tagging this one file purple. It was begging to be clicked open. So I did.” – “It was begging to be clicked open. So I did.”
The whole thing is a detective scenario in a film noir. JPMI has made a contract to protect the clients data but he’s the guy who breaks into it! Because the folder begs him to do it! Gimmie a break. Guilty.
It beggars belief that JPMI didn’t have a USB hub where he could plug a power source, keyboard and connection to another computer. They cost $10-30 and a repair shop would certainly have a number of them laying about. Charging the battery several times to transfer the files doesn’t make sense.
When contemplating a power-intensive process, such as a back-up, don’t most operating guides start with something like, “Make sure your computer is plugged in.” That would apply especially when you’re attempting to fix a computer, and haven’t established yet what isn’t working properly, such as the battery. This whole story is nuts.
This. To charge a battery one must first plug it in. Why unplug it and then proceed with the potentially fraught process of data recovery with a damaged Mac? It is beyond stupid. No one who is attempting a data recovery process would do so.
As for the limited number of ports on Macs, an “Authorized Mac Repair man” would have plenty of options to deal with this (as others have pointed out).
Apple used to sell a product called Time Capsule which was a router; a server; and held 2 terrabytes of data. It was a good way to back up data without using a cloud-based system.
I still find it amazing to the point of incredulity that the FBI would believe that the proper way to do a forensic analysis of a hard drive was to get another laptop and boot the drive. At the risk of repeating what others here have observed, booting the drive CHANGES IT and key forensic data is lost.
A simple and standard way to overcome this is to put the drive in an external cradle attached to separate machine. If it is readable, then a simple linux dd command will do a byte-by-byte copy of the entire drive without any write access. This is widely known
.
And this is from the Federal Bureau of Investigation. It’s right there in the name.
Looking forward to the next installment. Great detective work!
The linux dd command would copy everything from the source h/d as is, blank space as well as data. Forensically, I would think that’s preferable to copying data only by dragging and dropping specific files, which is what this idjut seems to have attempted. Hard to imagine anyone in the business would do that. Harder to imagine the files copied that way would be reliable enough to use in a criminal investigation.
Remember that prosecutors withheld the report on the viability of the laptop and the hard drive from Joseph Ziegler, presumably to keep him ignorant for testimony.
i *think* macos has had filevault on by default since 10.10. i believe that means only by pairing the t2 chip with the laptop will get you data 2015-on . i remember having to go uncheck it for other reasons. it was opt-out.
it would also mean dd would get you gibberish off desoldered hardware.
[Welcome to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security **as noted in the first comment of this thread.** Thanks. /~Rayne]
Not relevant at all to the HB saga writ large, but the above quote is an admission of malpractice, if not prelude to an outright fabrication of events. A drag-and-drop “procedure” (heh) is not only inherently risky, but also has no affordance for validating the copy. A competent operator would use TimeMachine, rsync, rclone, or a low-level platter duplicator.
i still do not understand why Hunter would leave a computer, especially a Mac, with this Isaac guy. I use Macs and I would not ever think of getting any repairs or support from anyone except Apple.
Was Isaac someone Hunter knew? Was his store extremely close to Hunter’s house in DE? Was there no Apple stores nearby? Did Hunter take it to Issac because he knew that some of the pictures on that machine were “unusual?”
Also, the fact that Issac does not apparently record serial numbers when accepting a computer from a customer is very unusual.
FWIW, Apple itself refers people to Apple-certified repair places that are not Apple stores. I’m guessing that this happens pretty frequently, as it seems to depend on what’s closest to where you’re located. I’m not saying that that’s what occurred with HB, though, if indeed he was the one who dropped off the 3 laptops.
Based on emails, Hunter has experience going to the Apple Store for repairs and orders of new devices.
And on the work orders, The NY Post, and even in the follow up reporting by better journalists, should have contacted prior customers and examined prior work orders to see if that’s a typical work order, or if Mac Isaac changed any verbage or any other discrepancies from SOP.
That would have required an interest in ‘the truth’ rather than keeping their focus on ‘the story’.
I am far from any Apple store. I use an outlet of a small chain of fixit shops. It never occurred to me to ask if it was Apple-certified; but they have looked after about two dozen iMacs, iPhones amd MacBooks, with good results.
Competent computer repair people are everywhere, even out here in the wilderness.
After the warranty expires Apple is really not needed/interested. Any shop experienced in Mac is OK. Apple likes all the exclusivity, but when the warranty expires you’re on your own.
Except:
If the place you go to is not a ‘certified Apple partner’, the shop cannot (or couldn’t at the time) get parts for Apple computers. Non-Apple partner shops could only get parts from ‘breakers’, because after-market parts for newer Apple computers aren’t available for about 3 years, and some are never available.
And Apple ‘Partner’ shops are required to have a ‘Certified Apple Technician’.
Did ‘Mac’ Isaac meet these qualifications?
Inquiring minds want to know.
He had worked at a genius bar before. So he had that qualification.
If ‘Mac’ Isaac was a certified Apple repair partner, he most certainly in violation of the terms of his agreement with Apple:
https://support.apple.com/aasp-program
‘Apple periodically audits and reviews Authorized Service Providers to ensure these high standards are consistently met.’
Was this joker an Apple Repair Partner, or is he just claiming to be?
And, did he bother to update his certification annually?
“Certifications are updated on a per product basis annually.”
It is fairly onerous and expensive to be Apple certified. Hard to see that this cluck really was. Has that aspect been confirmed?
Lol, and he once spent a night at a Holiday Inn Express?
The proof that it was him amounts to a purchase in a cigar bar that the person conveniently mentioned to JPMI, two phone calls involving a phone that may have been easily misdirected and “other intelligence” per FBI.
Givne that whoever had that laptop had his digital life, that would be easy to fake.
As far as phone calls being intercepted, there’s a couple of threads to pull.
One is the phone that was not traded in, that you pointed out previously. But another one is that Hunter appears to have placed one of his phones in Hallie’s car just before going to Ablow, in order to monitor the GPS location activity while he stayed at Ablow’s.
This appears to be 1st week January 2019. Based on data available, I believe that this phone is the one with the phone number on the Mac Isaac invoice. It’s not clear to me that he personally retrieved it but it appears to be a month before it reappears, as it appears to me to be the phone that backed up onto the Mac Isaac laptop, extracted on morning of 2/6/19.
Why/how do we know that was Hunter and not someone else?
Mac Isaac’s whole story falls apart when we know that that the hard drive was removable, different from what Mac Isaac claims to be the soldered in hard drive.
And, a PDF named Burisma with a purple dot, it’s a Christmas miracle, pointing out to the topic that’s blowing up in the news.
And one laptop has a Beau Biden foundation sticker. The laptop repair person just happens to be the only blind computer repair person, so who’s to say if it really was Hunter who dropped off, or any white guy pretending to be him.
There’s a whole lot of Christmas miracles in this whole saga.
Oh, ye of little faith!
I’ve brought this up before. After 2016, only some macbooks had removeable drives, and those drives have proprietary Apple pinouts. You cannot buy just any ssd drive and fit it into an Apple laptop (or any newer Apple, for that matter).
That’s the reason that the FBI bought a new laptop to fit the drive into (one that was the same model as the original). The pinouts would only fit an Apple that was that particular model.
If a MBP has a Touchbar on the keyboard than the drive storage is not removable from the motherboard except via a chip shop. If there is no touchbar, a 2016 and 2017 15″ MacBook Pro has a removable/upgradeable SSD; these are the last upgradeable MBP models. Note that the 2016 model was replaced by the 2017 model in mid-2017 timeframe while the mid 2015 Retina model continued production until July 2018 (yep, Apple maximizes their manufacturing ROI .) On those MBPs that are upgradable in 2016-17 models (again, the ones without touchbars) there are readily available SSD adapters for standard 2242 4x nvme drive to work inside them. The 2015 model is also SSD upgradable but uses a different Apple proprietary SSD pin connector than the 2016-17 non-touchbar models; SSDs from 2015 15″ models are backwards compatible with Retina models back to 2013 or so.
I know less about the 13″ models at this point but here’s a link to a blog that goes over much of this stuff:
https://beetstech.com/blog/apple-proprietary-ssd-ultimate-guide-to-specs-and-upgrades
There are also various videos and fixit instructions available on the internet that cover how SSD replacement and removal is handled for a given specific model of Apple laptops from that era, ifixit.com being one excellent resource there if you want to get into the nitty-gritty of how an upgrade can be done, etc, etc.
TY. That seems to confirm that the Ablow laptop did have a soldered hard drive.
The 2017, 13” laptop given to the FBI (S/N FVFXC2MMHV29, model ID MacBookPro14,1) is quite similar to the 2016 13” model ID MacBookPro13,1. Both of these version have only (2) USB-3 ports (used for charging and peripherals attachment), a removable solid state drive and lack the touch bar sensor. The 13” MBPs from these two years with soldered drives have (4) USB-3 ports as well as a touch bar sensor. The lame charging story is inconsistent with any models from these two years. A 13” MBP with a soldered drive and only two ports was not offered until 2019. I matched Model IDs from Apple’s MacBook Pro descriptions with those MBPs that have SSD upgrades offered by Other World Computing (OWC). I’d post a table for MBPs from 2014-2019 if I could fix the format.
Re: “I went in the back to check on Hunter’s liquid-damaged MacBook Pro. It had powered off, dying overnight during the file transfer,” all 3 reportedly had liquid damage, and other of his comments make clear that he’s referring to the 2016 13″ laptop with a soldered drive, as the quote about that one continues “… After working on it for about thirty minutes, I was relieved that the machine was able to power on and was mostly stable. I proceeded to inspect the drive. It was 256 GB in size and about 85 percent full. The drive passed its diagnostics, so I decided to perform a clone of the drive to the store server. … I would start the cloning process to run overnight …”
I’m not sure how to reconcile “the drive … was 256 GB in size and about 85 percent full” and “There was about three hundred gigabytes’ worth of data.”
Pure speculation, but that can happen if most of the data, so considered, was compressible. If there is a lot of text as opposed to binary data that would qualify.
Thanks.
Forgive me if this has been addressed before, but the intake form states “Equipment left with the Mac Shop after 90 days of notification of completed service will be treated as abandoned … [emphasis mine]”
Has JPMI put forward any evidence that he tried to notify Hunter?
JPMI’s lawyer Brian Della Rocca claimed:
But I haven’t been able to find an email to corroborate that claim in the exhibits.
Hmm. JPMI’s lawyer is misstating the record here about there ever having been direct contact with Hunter Biden. There are strong implications based on the public record but, as EW keeps pointing out, this is dependent on cloud location device data not direct, independent corroboration of Hunter having ever verbally or physically been within shouting distance of JPMI. (And, as to whether the fact that JPMI is considered legally blind enters into how and why this confusion was intentionally part of this from the start, well, it does seem to factor here.)
I applaud much of the effort by Emptywheel to get to the bottom of what exactly happened to the data that was on this laptop, where it came from and who touched it though. Pretty sure that at minimum various privacy laws were breached by people that were not Hunter’s intention nor fault. This would, sadly, not be the first time that an addict was taken advantage of either. Our society and politicians, their political operatives, etc, shouldn’t be encouraging people who are addicts to be continually abused/victimized just because they are an addict. This is a complex legal mess that Hunter Biden and his legal team have to deal with here, and, sadly for Hunter, a lot of this stuff he brought upon himself it seems. In addition to the abuse of Hunter Biden’s laptop and device information, If there’s strong evidence that he became an addict as the product of a foreign operation, that would be a most serious point to consider—so far, there has been no claim or strong evidence that this too was a foreign (or domestic?) dirty operation, only that people took advantage of him after he was an addict.
For addicts, the United States as a country, needs to have more compassion and protect them from being victimized
How do you protect someone from being victimized, especially someone who’s in a “disabled” state of mind?
Credit card companies and banks will try to get in touch with you if they smell a rat but if an Ablow or Rudy is trying to screw you, how would a friend, relative or authorities know?
Clearly an email from JPMI to rhbdc @ icloud.com wouldn’t establish that Hunter had ever met or communicated with JPMI. But if such an email doesn’t exist (and/or phone records showing calls to HB) it seems to me that would be problematic for JPMI.
Just as, per Abbe Lowell’s letter to DE AG Kathy Jennings requesting an investigation:
Can’t argue with that. No one can resist a purple tag.
Well, JPMI had been the “Lead Genius” at the Apple Store in Littleton, CO.
The purple dot made him do it!
Nice…
“It was begging to be clicked open. So I did.”
That is an astounding comment. WTAF reason is that for snooping into private data?
He wasn’t snooping into private data! The files were begging him to be opened! It wasn’t his fault! /s
I can’t imagine that potential customers would take their computers to him if they knew he’d done this, and deservedly not. I hope this puts him out of business.
The Mac Shop shuttered in 2020. JPMI blames Hunter Biden, Adam Schiff and CNN. And he sued them for it, giving Hunter the opportunity to countersue.
That kind of sounds like a ‘rapey’ guy blaming his conduct on the clothing of his victim.
I had the exact same reaction.
yup.
I can’t even comprehend writing something like that down while also claiming to protect customers’ privacy.
Also isn’t that a confession that the 90-day abandonment thing is BS? If he was snooping on the files while doing the work, then there’s no way the laptop was considered abandoned unless you’re just straight-up twisting space-time into a pretzel.
Question:
What are you referring to here, about the day the Mac Isaac-FBI laptop “stopped syncing”?
Per your article quoting the emails, “2/15/19: Robert’s MacBook is being erased. The erase of Robert’s MacBook started at 4:18 PM PST on February 15, 2019.” I’m not sure what you are referring to by the laptop stop syncing also on the same day.
https://www.emptywheel.net/2023/07/08/the-laptop-everyone-knows-as-hunter-bidens-appears-to-have-been-deleted-starting-february-15-2019/
That Thomas Fine illustration is something else. He indicates six copies, though, not including the “original” in the upper left corner, and with a couple of caveats. Three words kept leaping out at me: Chain of Custody.
I can’t tell if this is a bad version of a political hit job, or an effort on the part of an unfriendly spy service to sow discord/influence the 2020 or 2024 election/poison the US political climate/all of the above. There’s been a lot of discussion of the investigations by the DOJ and Congressional Republicans, but behind the scenes, the CIA and other intelligence agencies have to be running their own quiet investigations — likely including an effort to compare *all* these laptops with one another. JPMI is looking more and more like someone’s tool, but whose tool is very much up in the air.
This is one of the things that amazes me about this. The Secret Service–both a protective agency and a hacking LE, as you know–were supposed to have been investigating this. But there’s no peep of them responding to signs of compromise.
On review, that Venmo payment I highlighted is even more problematic. Hunter deleted a lost iPad starting 8/5.
So he loses an iPad. Two people get into his venmo, sandwiched around someone ASKING for payment of sex as art, and Weiss is going to use the similar, very next Venmo payment? Really?
It’s one thing that keeps me chasing this: the astonishment that, in fact, the ex-Vice President’s son appears to have been serially compromised, AT LEAST by his dealers, and the FBI never treated that as the important crime.
Hunter believes that during the night of 8/4 to 8/5 one of his laptops was stolen by a Russian drug dealer in Vegas. I’m not sure if an iPad is believed to have been stolen at that time as well, but it would make sense that would cause someone to delete their iPad, which for some reason finally finished being deleted on 9/11, 5 weeks later. I don’t know if 5 weeks is a normal time for Apple devices to delete.
Is that in his texts?
Yes. The Marco Polo Report on page 628 has the screen shot of texts the day after the laptop stolen. I think the time zone is Pacific.
Hunter described the incident in a home video recording in January, I think Jan 6, recounted by the Daily Mail.
https://archive.ph/5LJJm
^^^ This, this, this, this. ^^^
Secret Service has so much to account for, as does the FBI.
Amazing, too, how these failures are ignored by media which has inverted the amount of attention paid to Biden’s son’s potential compromise as compared to Trump’s sons’ and son-in-law’s compromise.
Even more bizarre since we were also talking about a former VP, who was running for POTUS, and the property of said former VP’s son.
I’m confused as to what exactly SS would be investigating and when that investigation would have even been required by law. By law, Ex-President (and their spouse) enjoy SS protection. Hunter would only interact with SS when he was around or near the ex-President and/or spouse until Joe Biden was President elect in late 2020. From the point in 2017 when Trump took office through late 2020 Hunter Biden would not be part of SS jurisdiction except incidentally, correct?
As for FBI, well, it’s clear, for the most part, the agencies agents weren’t being incredibly competent with the the alleged Hunter Biden devices and data images that they acquired during the time period of this ongoing scandal. Let’s hope they’re having more success with the Jan 6 2021 DP/GOP HQ bomber investigation than they seem to be here with Hunter’s data chain of custody… yikes?
From the USSS “About Us” page:
It’s the latter part of their mission that would initially intersect with Hunter Biden/Burisma et al. But if there was a whiff of someone trying to use Hunter to get to others (like his dad), it could also connect with their protective mission too.
Thanks for this. Do they work for Treasury any more? I thought they got moved somewhere else…ah, yes, Homeland Security 20 years ago.
The question I now have is what events of national significance the SS would be investigating here prior to late 2020? What was/is the legal basis for their investigation? Who and what would they be protecting? I mean, we should all hope that it wasn’t to protect just one man or small group of men from having to leave office if voted out.
In October 2020 — so as you point out, before Hunter became a protectee again — some LE began to consider whether the laptop was a foreign operation.
What’s not clear is if anyone looked at prior (potential) compromises, like whatever happened in August 2018, which could have served as groundwork for the Jan-February compromise.
“ By law, Ex-President (and their spouse) enjoy SS protection. Hunter would only interact with SS when he was around or near the ex-President and/or spouse until Joe Biden was President elect in late 2020.”
The law does not apply to Vice-Presidents, who lose protection 6 months after leaving office, children of Presidents and Vice President above the age of 16 also lose protection on the day their parent leaves office.
USSS, & elements of the FBI, were/are institutionally compromised by this time. Since 2021 they have an interest in not disclosing it, I believe that has driven much of their (in)actions.
This is definitely a combination of a political hit job and efforts by foreign intelligence to influence the 2020 (and now 2024) election. I see a lot of repeats of 2016. (With 2016, I also have a strong suspicion there was even foreign involvement with the Weiner laptop which has not been reported or confirmed)
With Hunter, I also see efforts by foreign intelligence to gain influence and/or have insight of Hunter, and via him of Joe, which fail in part due to Hunter’s personal life unraveling.
One US intelligence agency that did show interest in Hunter’s laptop is the NSA, which I don’t know if it is considered a LEA. This detail is via Mac Isaac, who says when he was called back by Sen Johnson, they handed the phone to NSA staff who asked only if he has ties to any other countries. While I don’t take Mac Isaac at face value on everything he says, I don’t know why he would invent the NSA phone call, because it makes it look like the deep state is actively monitoring a foreign plot involving Hunter’s laptop.
I have a hard time believing the “laptop story”. What it sounds like to me is a bunch of people positively wetting themselves with the need to make a bunch of hacked accounts public, and trying to figure out how to get around the criminal charges associated with said hacking. They found laptops belonging to Hunter, and decided it would be clever to create a hard drive (or two, or three) with all the hacked data and claim it (they) came from the laptop. But because they are stupid, their ruse fails even the most basic forensic analysis.
All of the things I read about “Hunter Biden’s laptop” sound like these people realizing how many holes there are in their story and making lame-ass attempts to fill them.
Umm… and I’m probably the last person to figure this out, aren’t I?
I expect the DOJ, or especially within the DOJ the FBI, is never going to go back to this laptop stuff. That I can understand. Closing ranks and keeping heads down before the election. But what about the State of Delaware?
the statute of limitations is almost expired on any original theft of the laptop.
Roll last scene from Burn After Reading? I joke but clearly FBI could be better than this if they weren’t so riddled with the beriddled.
I’m not the first to recommend EveryMac.com as a site to explore the different Apple devices.
This page describes the differences between early 2015, late 2016 and late 2016 w TouchBar 13” MBPro. They do have different SSD (solid state drives).
Power on the 2016 models is via USB-C ports – of which there are 4. Charging would not be an issue.
I felt at the start of this that they were hacking the one by trying to recover the drive with another (after previous attempts – because it seemed no one knew what they were doing – especially the shopkeeper.).
But this is beyond: That they managed to get a machine (a model that looks close enough, and/or maybe even the original, with automatic user sign-in) working, to log-in to the cloud stuff sounds like they were regularly impersonating Mr. Biden by powering up that machine to “backup” and do whatever with his stuff. Ablow’s office? Whoever, wherever- it’s all fairly easy to trace – and it is stupid and mad illegal from the beginning. It’s getting to be lots of potential charges. I was wondering if someone cloned the machine again for passing around: It’s a lot of machines now! If so, they probably found more effective help than the original shopkeeper guy. I already assume there’s more than a few copies of the drive still floating around, as well-
Mr. Mac Isaac’s store’s web page is gone (he moved to Colorado and opened a new store.) But you can find “www.demacshop.com” in the wayback machine (I looked at one from Nov 4 2016).
No Apple certification that I could see.
The data recovery page has this:
“We will transfer your data onto a different machine for you or for a fee we can provide you with a fresh internal or external hard drive for your data. If you need to send an under warranty hard drive back to Apple we will make sure your data is backed up and secure so you don’t risk any further loss and since we don’t need to open up your drive your warranty remains intact. ”
To me, that suggests technical competence rather than believing this file-by-file drag-and-drop nonsense or the earlier nonsense about how he somehow learned what was in the files as part of real work.
The yelp reviews are a hoot, (search for the mac shop delaware) many from, ahem, gushing admirers and damning haters three years after the store closed.
For the warranty, it is standard practice for some computer repair businesses to provide a backup service (and fee) of a client’s data prior to sending a laptop back for warranty repairs. That’s fine as long as no one who is not Apple certified don’t touch the internals on a laptop. If the laptop’s internals got touched then it used to be that it had to be an Apple certified tech poking around to guarantee that a current warranty claim would be honored by Apple. In general Apple used to be pretty strict about their warranty return/replacement policy, with any positive edge outcome being more anecdotal in nature rather than the main. That may have changed now with Apple’s public repair kits program now being somewhat available; that change was during the pandemic or later I think.
Here’s some data points to help unpack
a) 2016/2017 13” MacBook Pros variation
Entry Level: without Touch Bar, removable hard drive (Mac Isaac-FBI laptop)
Higher model: with Touch Bar, soldered in hard drive; (Ablow laptop)
https://everymac.com/systems/apple/macbook_pro/macbook-pro-touch-bar-faq/how-to-upgrade-macbook-pro-touch-bar-ssd-storage.html
2) Proof of a Touch Bar Mac at Ablow’s
Hunter gave CBS a picture of the laptop retrieved from Ablow, it has a Touch Bar
https://www.cbsnews.com/news/hunter-biden-laptop-photo/
d) Photo proof of a No Touch Bar Mac at Ablow’s
On 1/29/19, while still at Ablow’s, Hunter texts an accomplice in Delaware about planting gps tracking devices and cell phones into Hallie’s car. There are texts from Hunter of pictures of a MacBook Pro *WITHOUT THE TOUCH BAR* shopping for GPS devices, so different from the Ablow laptop above, evidence Hunter had 2 computers at Ablow’s, one w/ and one w/o a Touch Bar
4) weird photo of a No Touch Bar Mac but labeled “screenshot” from 2020
There’s a photo dated 10/23/20, of a MacBook Pro w/o Touch Bar open to a Hunter home video dated 5/22/18. Really bizarre. I believe Guo, Bannon, and Costello then each have their own copy. Bizarrely, this photo appears in the Album “screenshot” and has “screenshot” in the file name, seems weird because its a live photo of a laptop with an open screen.
5) Treatment vs writing while in rehab
Hunter’s family staged an intervention 12/26/18. Part of the calculation for selecting a treatment center included having space to write. Hunter was planning to write 2 books and a 10 part podcast series with Ablow, and was working on a “zine” with an artist friend (who was the only approved visitor for Hunter while he was with Ablow), after having taken a writing workshop at Esalen Institute the previous summer. So Hunter was going primarily for treatment, but also did expect to work on writing.
6) hard drive warranty starts weeks into Mac Isaac possession
Mac Isaac allegedly called Hunter to bring a hard drive, which he did. 3 year warranty expired 5/2/22. Weird that Hunter would activate the warranty at all, while it’s not in front of him, weeks after bringing it to Mac Isaac, and most certainly while he was in California. Not sure if there is an alternate explanation. (And weird Mac Isaac didn’t have hard drives to sell).
https://support-en.wd.com/app/warrantystatusweb
I have more, but will stop here, the moderators are probably upset for including this many words. Apologies, there’s just a lot here.
The 2015-2016 period was when Apple began switching drives from connectors to ones soldered in place, so the specific model is needed to know how the drive is attached. The Entry Level, non-touch bar 13” MacBook Pro has an SSD with a connector is the model (MacBookPro14,1) to which Marcy linked and it only has two Thunderbolt-3 (USB-C) ports for connecting to power and peripherals. Like most people who purchased one of these computers, I quickly gathered collection of dongles that allow one to plug in multiple peripherals given that the laptop has only two available ports. No repair shop should have had any difficulty connecting a power supply, keyboard, and an ethernet cable.
The lack of serial numbers is indeed quite odd. Apple’s support site has an identification list of all MacBook Pro’s going back to 2008. The instructions at the top of this list would seem useful in this case, “If you don’t have your Mac or it doesn’t start up, use one of these solutions instead: Find the serial number printed on the underside of your Mac, near the regulatory markings.” These printed serial numbers are well defined, have high contrast and are easy to read with a cell phone magnifier app (or similar tools employed by those a visual impairment).
The modern macintosh computers run a version of UNIX under the hood. Even this hack knows to use those UNIX tools to perform any serious system or drive investigations.
Ohh yeah, the serial numbers
* Dimitrelos and his 17 digit serial numbers
Are 17 digits serial numbers a thing? Maybe someone more technical than myself or fluent in Apple, knows what’s going on. Apple devices should have a 12 digit s/n. Dimitrelos records 12 digit s/n for each phone, but 17 digits for laptops, except for one laptop. The only MacBook that Dimitrelos records a 12 digit number is the Mac Isaac laptop, whose s/n was coincidentally already in the public domain, so I suspect that forced Dimitrelos hand to list the 12 digit. According to a Mac repair associate at an Apple Store that I walked into, 17 digit numbers aren’t a thing, only 12 digit serial numbers, which can be cross checked on various websites. So I absolutely believe that Dimitrelos is intentionally running interference here, along with his grammar shenanigans.
https://www.scribd.com/document/575556723/Final-Hunter-Biden-Laptop-Report-Redacted (page 14)
* The Last Heartbeat
What exactly are Apple heartbeats? Something that continuously pings while connected to the internet? Pings once a day? Hour? Week? Only when certain applications open? The device “Robert’s MacBook Pro” has a Last Heartbeat IP address of Ablow’s where Hunter stayed until 1st week Feb 2019, but the laptop was still used until 3/17/19, so why does the last heartbeat lead back Ablow?
Why do we believe Hunter was the one texting, when he told Katie Dodge he was AWOL in this period?
Well, *I believe* H sent the text because the text writing style and situational context are consistent, and have seen no suggestions or evidence any texts or emails were faked, outside of the resent emails discussed recently. Also, telling Dodge he’s AWOL seems consistent with giving plausible reason to family for not communicating while relapsing.
From Beautiful Things:
* I was previously warned by a moderator not to use “we”
The govt has to prove who sent the texts, e-mails, etc., not HB.
In what context would the government need to prove who sent the texts ? I am not aware of an investigation to prove that Hunter was hacked and to prosecute any potential hackers
For all the expenses put through in 2018, the government will have to prove that Hunter made the expense, and was charged what he believed he was paying. As I noted, they couldn’t even get the date of the 8/13/18 payment correct, and that’s one that will require a great deal of validation.
Because if he was charged for stuff he didn’t know about (or thought was a fraction of what it was accounted for), it’s no wonder he didn’t account for it correctly.
I get that, following along with you there, but I don’t see the connection with this conversation.
Why would Weiss be interested in the January 29 text messages with photos of a Mac Book not having a Touch Bar?
Except as I’ve shown, Ablow twice literally spoke for Hunter, the first time potentially as an effort to test whether Hunter could be tricked into believing he was still in touch with the world when he wasn’t.
I’m not trying to minimize the difficulty that Hunter is not speaking — though at trial, the onus will be on Weiss to prove that he is speaking or paying for every utterance.
I’m saying we have literal, affirmative proof that at times, someone else was speaking for him, and also abundant evidence that the tools of fakery were otherwise present.
There might be another alternate fact here as well. I don’t know Apple products well, but what I do know is they are not stupid, and soldering a hard drive to the motherboard in this day and age of modular computer devices seems just stupid. A precursory search for “MacBook Pro hard drive replacement” reveals nothing indicating Apple ever soldered the hard drives to the motherboard. Plenty of guides on how to replace the hard drive, though.
Apple makes money off of forcing its customers to pay a high premium for more storage on the laptops it sells. They always tried to do that but when the internal storage was customer upgradeable Apple wasn’t banking as much profit. Same thing applied to when RAM was user upgradeable…which has not been the case for even longer than internal storage. Now they bank the profit if you want to pay an extra $600+ premium to have a 4TB SSD on you motherboard when you order it…as you cannot upgrade it later. Same for RAM; pick what the max you think you’ll need far into the future as you are stuck with whatever you now order.
Afaik, Apple does not offer more than a paid 3 year warranty on it’s latest laptops… so buyer beware. If it wasn’t for places like California, Apple would not even maintain a parts inventory for these things past 5 years (California requires 7 years—was 5 but, hey, Apple so…).
Apple saves a ton on manufacturing costs by doing this full integration on mobo…as long as they don’t have a major parts screw up for parts that go onto the motherboards. Safe to say that they must have enough confidence that the mobo assemblies are going to fully functional for at least 3 years and statistically likely for 7 years at this point. This process allows Apple to innovate without having to worry much about standard parts market fluctuations effecting their bottom line basically; they don’t have to cater to much of the next “industry wide” user upgradeable bus fads pretty much.
Consider how it increases Apple’s income and market power by excluding from such a large market so many third-party component sellers. It also reduces the number of people to whom it has to disclose proprietary data about what’s needed to integrate a component into its devices.
I think there’s a pretty easy and intuitive distinction between equipment and data. Plus, contracts generally are interpreted against the party who drafted them.
Thus, JPMI is going to have a really hard time explaining why he grabbed the data, as opposed to the hardware which was brought to him. I’m not sure “begging to be opened” is going to be a sufficient explanation.
Has any congress member pushed back against Comer saying that Hunter’s data was illegally hacked?
Lol, you think it was “legally” hacked? You continue to be an unnecessary irritant.
I couldn’t find an explicit quote from Raskin. Certainly Lowell, Hunters attorney, would love it if some Representative or Senator would state that some of the data Congress is using was obtained illegally! Sadly, I did find a Nov 28th statement by Raskin’s office that might be a bit over the skis on protecting Hunter Biden from all criticism. It’s a pity his press releases aren’t a bit more nuanced—maybe a staff member wrote it?
Dan Goldman has pushed to get the provenance of the hard drive they have on the record.
Thanks for this further deep dive. Just a little accounting note: This post repeatedly conflates MacBook Pros and PowerBooks.
The excerpt from the JPMI book refers to a 15″ laptop (apparently a Mac of some kind) and two 13″ MacBook Pros. MW later refers to 13″ PowerBooks. The PowerBook was discontinued in 2006 and replaced by the MacBook Pro.
The post even contains a link to what it calls “a 13-inch 2017 PowerBook purchased in October 2018,” but the link goes to a MacBook Pro.
It’s easier to keep track of which computer is which if the right names are used! :-)
For what it’s worth: I’m typing this on the same model laptop as one of those JPMI said he received from Hunter Biden, a 2015 13″ MacBook Pro.
I’ve never really dealt with Apple products, but I do have experience in windows general computer repairs & the first thing that stuck out to me on that linked invoice was the $85 charge for data recovery on 3 machines. Perhaps this is what one would expect with Apple machines, but to me that is a suspiciously cheap price to try & recover data from 3 machines which were known, or should’ve been known, to have unknown other problems causing them to either not work properly or have difficulty operating. Seeing another comment mention the Wayback Machine having copies of the repair shop’s site I went to look at it. The data recovery page mentions:
“The most you will ever pay at The Mac Shop Inc. for a successful data recovery is $159.”
…
“If for any reason we are unable to get your data back you will only pay a $39 dollar attempt fee for time.”
So, the minimum charge should have been $117 as even failed recovery attempts were $39, so times 3 for the different machines.
[Welcome back to emptywheel. Please use the same username and email address each time you comment so that community members get to know you. This is your second username; you published a comment in 2018 under a different username. Please be sure to stick with the same username going forward on all future comments. Thanks. /~Rayne]
So, you get what you pay for…in legal fees?
Regarding Mac Isaac’s use of drag and drop, the service he was offering was data recovery, not disk imaging, and he certainly never claimed to maintain forensic integrity. The FBI can be faulted for failure to properly preserve evidence but I don’t think it fair to fault Mac Isaac in that regard.
I was going to flag the incorrect reference to PowerBooks in Marcy’s piece (the original PowerBooks were 20th century machines, and the later PowerBook G3/G4 models were last sold in 2006), but Carlllll beat me to it. Apple began calling its laptops MacBooks when it transitioned from PowerPC microprocessors to Intel CPUs.