James Comer’s War on Christmas: The Burial Ground of a Dick Pic Impeachment
Republicans have rolled out a shiny timeline in support of their impeachment stunt.
It is riddled with unsubstantiated and at times, false claims. As one example, it states as fact that a $40,000 loan repayment James Biden made in 2017 — when Joe Biden was a private citizen — was money laundered from China.
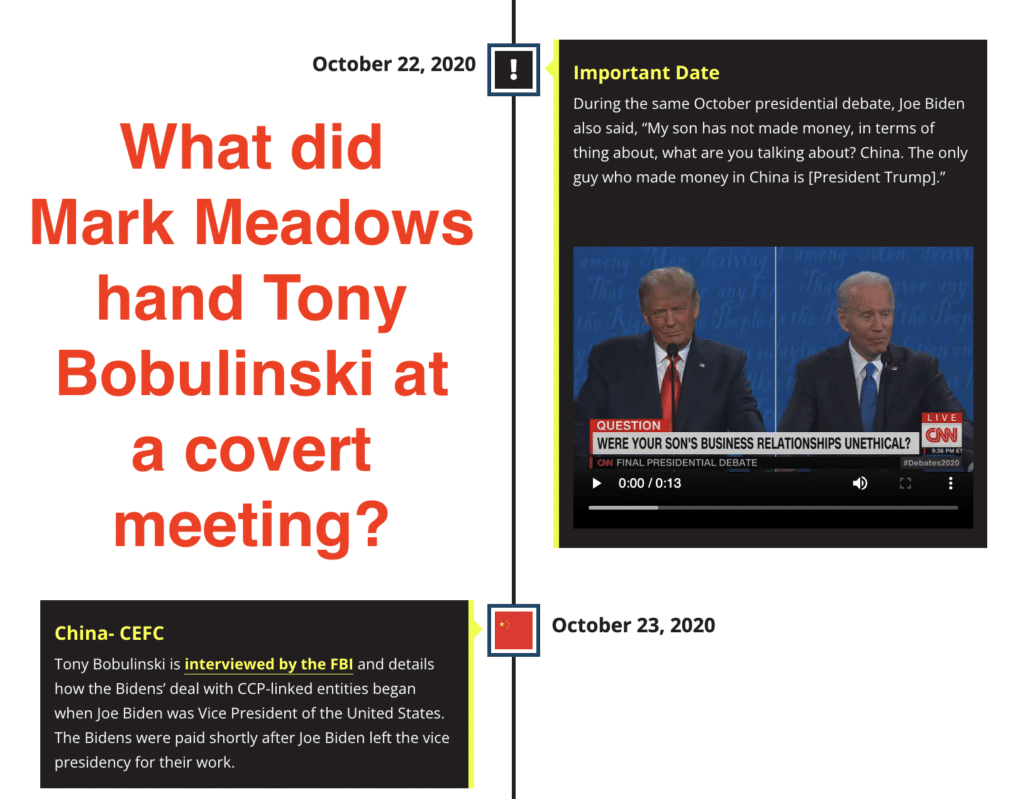
It juxtaposes a misleading (but potentially caveated) answer at the October, 22 2020 debate from Biden with Tony Bobulinski’s interview with the FBI the next day, but doesn’t mention that Trump hosted Bobulinski at that debate and then, according to Cassidy Hutchinson’s book, Mark Meadows handed him something at a covert meeting weeks later.
It doesn’t, however, mention Tony Bobulinski in its report about a meeting between Hunter and CEFC Chairman Ye Jianming on February 16, 2017 (the date of the meeting may not even be correct).
In the testimony Bobulinski gave to the FBI between attending the debate with Trump and having a covert meeting with Mark Meadows, he claimed to have attended that February 2017 meeting and seen Hunter receive a diamond.
BOBULINSKI first met in person with members of the BIDEN family at a 2017 meeting in Miami, Florida. BOBULINSKI, GILLIAR, WALKER, HUNTER BIDEN, and YE all attended the meeting. Also in attendance was Director JIAN ZANG (“ZANG”), a CEFC Director involved in forming new businesses and capitalizing them at the request of CEFC. At the meeting, BOBULINSKI witnessed a large diamond gemstone given as a gift to HUNTER BIDEN by YE.
Perhaps the silence about Bobulinski arises from the fact that Hunter Biden has claimed Bobulinski not only wasn’t at the meeting, but didn’t yet know of James Gilliar’s business ties to him. Rob Walker, who was at the meeting testified, twice, that he didn’t see a diamond pass hands at the meeting.
Walker has read about RHB receiving a diamond from people with CEFC, but he never saw the diamond.
And James Biden testified that an associate of Ye gave Hunter a diamond at his office (not the meeting) — but it ended up being worthless.
James B did recall RHB receiving a diamond from the Chinese but that they found out it was not valuable. RHB said that he received the diamond from an associate of the Chairman at his office [redacted] James B stated that the Chinese always gave something as a welcome gift. RHB was originally told that the diamond was worth $10,000, but James B took it to a friend of his and found out that it was worthless. James B is only aware of one diamond and was not aware of a larger diamond.
All this changes Biden’s statement at the debate significantly; Trump was working off a Bobulinski claim that isn’t backed by the available records.
And then weeks later (again, according to Hutchinson’s book), Trump’s Chief of Staff handed Bobulinski something that might be an envelope.
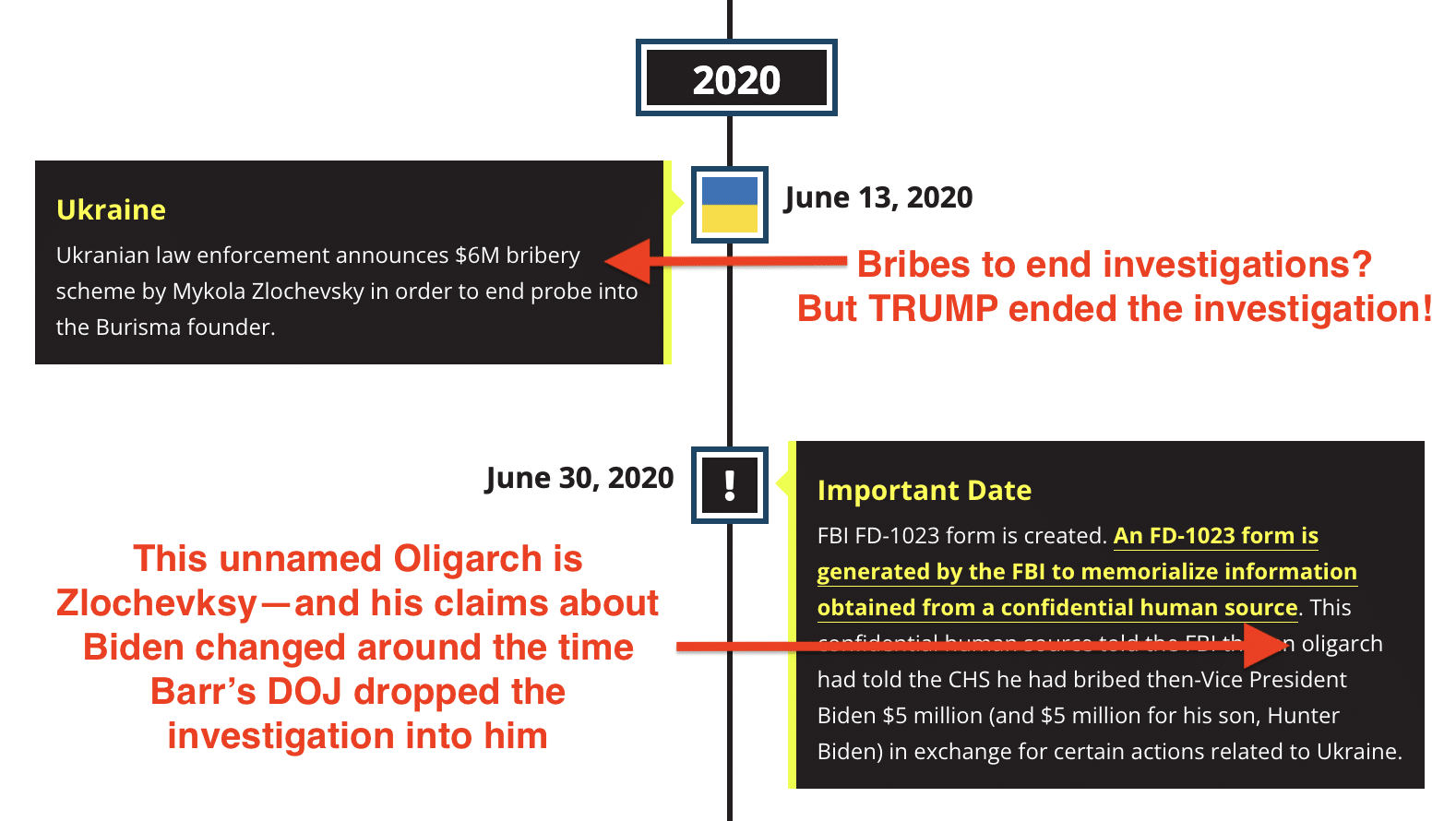
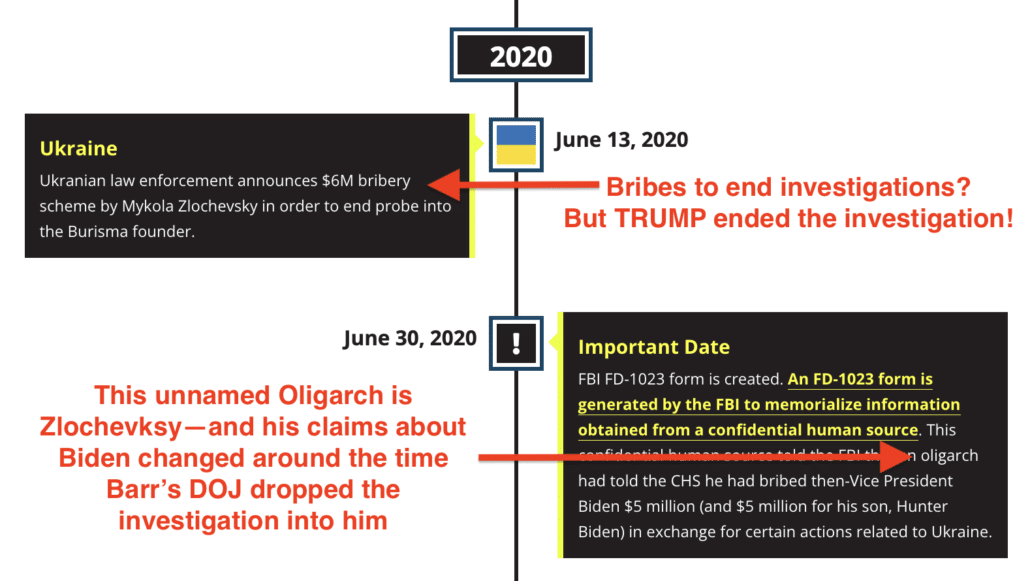
Much of the timeline focuses on Burisma owner Mykola Zlochevsky’s years-long effort to kill legal investigations into his corruption.
Unsurprisingly, the Republican timeline makes no mention of the investigation that — per Chuck Grassley — DOJ opened into the owner of Burisma in January 2016.
Likewise, James Comer forgot to mention that — again, per Chuck Grassley — Donald Trump’s DOJ shut down that investigation into Zlochevksy in December 2019, even while justifying his Perfect Phone Call with Volodymyr Zelenskyy with a claim to be concerned about corruption at Burisma.
Comer’s timeline definitely doesn’t mention that (per Chuck Grassley) Bill Barr’s DOJ shut down an investigation into Zlochevsky when it discusses that Zlochevsky was offering bribes to shut down investigations.
Maybe in addition to impeaching Trump for whatever he handed Bobulinski to make claims about big diamonds he couldn’t see, James Comer should open an impeachment investigation into why Bill Barr’s DOJ shut down that Zlochevsky investigation — and whether there’s a tie between the closure of the investigation and Zlochevksy’s new claims about Biden?
Wow. James Comer’s case for impeaching Donald Trump just keeps getting stronger and stronger!
Admittedly, Comer does take a break from substantiating an impeachment case against Trump by providing scandalous details about Biden … inviting his son to a party.
A party!! Joe Biden invited his son to a Christmas party!?!?!
This is truly scandalous stuff, particularly when contrasted to Bill Barr’s noble efforts to shut down an investigation into Zlochevsky at the same time that Trump was claiming publicly to support an investigation into Zlochevksy and Zlochevksy was, apparently, offering billions to those who shut down such investigations.
A Christmas party!
How dare a good Catholic like Joe Biden invite his own family member — his son!! — to a party at his residence? Surely the 18 Republicans from districts Biden won will be happy to explain their vote to impeach because they’ve decided to declare War on Christmas?
This impeachment gets better every day.
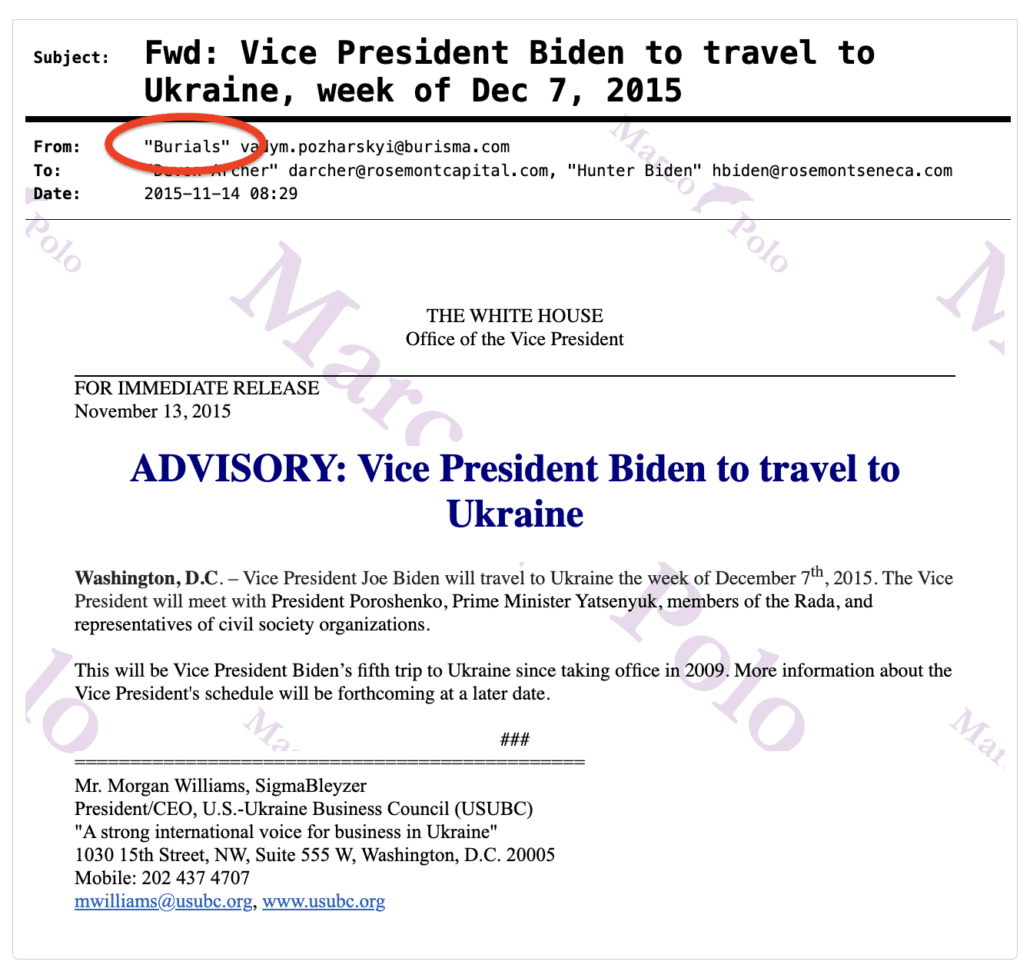
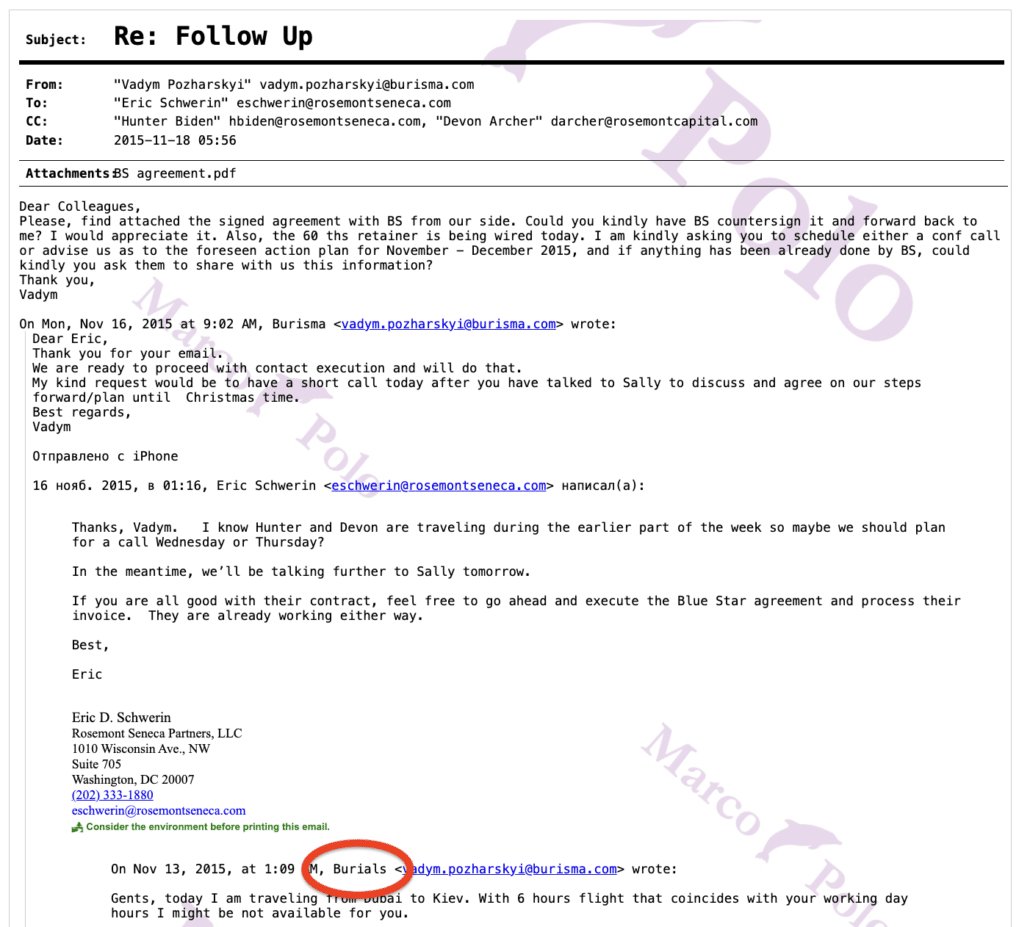
There’s one more utterly ridiculous detail I’m rather obsessed about. In addition to proposing to impeach Joe Biden because he invited his kid to a party, James Comer thinks it’s scandalous that Vadym Pozharskyi sent Hunter notice that his father was traveling to Ukraine.
Wow. Scandal. Pozharskyi knew and shared details about when Biden was traveling to Ukraine.
But I’m interested for a different reason. You see, this claim is almost certainly sourced to the copy of the “laptop” that House Republicans won’t explain — at least not on the record — how they obtained. In addition to the email from 2016 that was resent on September 1, 2020 when the hard drive was in Rudy Giuliani’s possession, this email is one with which I’m obsessed.
Here’s how it appears at BidenLaptopEmails dot com.
The President of the US-Ukraine Business Council got the alert from the White House, he sent it to Burisma, and Pozharskyi sent it — at least by all appearances — to just Devon Archer and Hunter.
As I circled, whoever’s email box this appeared in recognized Pozharskyi’s email not as “Burisma,” but instead as “Burials.” The email also had an identity for Hunter associated; most other emails that he received don’t identify himself.
There’s just one other email in the public set like this — an important one.
It was a thread sent over one week — from November 11 ET through 18, 2015. On it, Pozharskyi, Eric Schwerin, Archer, and Hunter discuss bringing in Blue Star Strategies — they’re the ones who tried to fix Zlochevsky’s legal troubles, with some initial but ultimately short-lived success.
This effort, outsourced as it was, was undoubtedly one of the sleaziest things Hunter was involved in. But the GOP didn’t include this email in their timeline (probably because it makes clear that Hunter did a pretty good job of firewalling off the legal influence peddling).
Anyway, from this email, it appears that it is Schwerin’s email account that, for a few days only, recognized Burisma as “Burials.” Only, he’s not listed as being on the other one.
I really have only suspicions about what explains this anomaly. I care about it, for two reasons. First, because the anomaly, especially on one of about ten or so that really get into Burisma’s efforts to suck Hunter and Archer into this corruption, does raise questions about the provenance of the set of emails loaded up on a laptop attributed to Hunter Biden.
Also because, according to a spreadsheet Joseph Ziegler was generous enough to share with the world, this is among the not quite 10% of emails that the IRS used in its own influence peddling investigation that they sourced to the laptop when it should have been included in returns from warrants obtained from Google on both Hunter and Schwerin’s Rosemont Seneca emails.
There’s a lot in Comer’s timeline that makes a great case for impeachment — of Donald Trump.
There’s a lot in his timeline that shows he continues to rely on fraudsters to make his case.
There’s a lot that tries to criminalize … Christmas!
And then there’s this, an email probably obtained from the famous “laptop,” one that raises some real questions about what got packaged up on a laptop attributed to Hunter Biden.











Amazing paragraph here
Looking at Comer’s timeline, even if any of the quids Comer lists were legit, where are the quos? Marcy proved that Zlochevksy got way more from Trump than from Biden. But what about Ye Jianming? What did Ye get from the private citizen Bidens other than a possible dirt nap? How about Gabriel Popoviciu? He got a 7-year prison sentence. The Moscow mayor’s widow? How is that Biden Ukraine support working out for Russia?
Shouldn’t Comer be able to document at least one tit for all the tats he accuses the Biden family of receiving?
It is absolutely the case that a number of these people saw Hunter as an easy mark. It is also the case that it generally didn’t work the way they wanted.
CEFC, for example, decided James Woolsey and friends was a better bet for his access to Trump.
The access to Hunter was a huge problem–no doubt about it. Ukraine, in particular, confused just about everyone for a while. But there are a number of points where you can see him drawing lines that people were paying a lot of $$ to cross.
Caveat emptor?
Non sequitur.
“…a number of these people saw Hunter as an easy mark. It is also the case that it generally didn’t work the way they wanted.”
Call it “let the buyer beware” or “buyer’s remorse”, none of the Comer examples that I pinpointed got the return they were expecting if they were influence shopping from Hunter Biden. Zlochevksy got nothing. Ye got the worst possible outcome. Popoviciu got pushed off on Freeh and Giuliani and ended up with nothing to show from his attempts to buy top Dem and Republican influence. Needless to say, they weren’t smart shoppers.
I think for someone like Zlochevsky, it’s not a zero sum game. Hunter didn’t work at all for his hopes to get Joe compromised and Zlochevsky’s legal problems ended. But having Hunter to offer up to basically sell to people in Trump’s orbit seems to have worked.
And by lying about Hunter, Fox has effectively compromised Joe in the face of the public anyway.
Zlochevsky seems to have played both ends off the middle, as my mom used to say. And (at least from the Barr/Trump perspective) won.
Three Republican lawmakers are demanding Special Counsel Jack Smith hand over all documents linked to his indictments of former President Donald Trump: Jim Jordan, James Comer, and Paulina Luna.
They want the documentation by December 15, 2023.
A recent court gaffe inadvertently unsealed on Wednesday, but later taken down revealed communications between Rep. Scott Perry, (R-PA) and former DOJ official Jeff Clark.
Perry also communicated with other House Republicans, texting Rep. Chip Roy, R-Texas, about “concrete evidence” of fraud in Michigan and Reps. Roy, Jody Hice, R-Ga., and Jim Jordan, R-Ohio, about “the Dominion voting system.”
I suspect Jim Jordan’s demand to Jack Smith is indicative of Jim being tied to the J6 shenanigans and Jim is getting nervous.
That Perry stuff was propery unsealed, AFAIK.
I think Jordan may be more worried about f-up indictments. In the Twitter warrant, CJ Boasberg said that there was still ongoing stuff (which should be obvious).
Congress is not entitled to detailed information about an ongoing investigation and prosecution. Jordan and Comer know that they won’t get it. They are grandstanding and misdirecting.
And fundraising.
Never forget the fundraising.
Always. Be. Grifting.
MAGA – Make America Grift Again
I think the only reason this has any traction at all is that the MSM (looking at CNN, NYT, WashPo and the increasingly feckless Kristin Welker) is giving Comer journalistic cover by not doing the fact-checking. EW and the rest of the board here didn’t have to dig very far to find gaping holes, yet the MSM wouldn’t risk their preferred horse race narrative by publishing it.
SC Weiss is possibly reading this, along with Abbe Lowell, and he knows any real trial is going to fall apart. So, Comer took a page from AG Barr and is trying to conduct a super-duper-pinky-swear-secret investigation where he can determine what comes out. SC Weiss can drag this out but at some point he must put up something like a report. Mueller and Durham did. I also still think he will close out the investigation by dismissing his charges against Hunter Biden when it appears politically safe to do. We’ll see how 2024 develops but I think this will be bubbling through the election, and then these things will stop..
HB could theoretically sue, but he’d have to show there is literally no predicate to go after him which unfortunately there is at a molehill stage. However, the whole mess does highlight the politicization of the prosecutorial system with partisan special counsels and I suspect we will need to develop a process to protect citizens from this kind of harassment.
Must the “curse of the MTP anchor chair”: whosoever sitteth in said chair achieves the power of fecklessness. Andrea Mitchell? David Gregory? (/s)
The added red text was very helpful. I’m sure we’ll see these edits in the next version, as well as details about Jared Kushner’s $2 billion Saudi deal. ;-)
Of course, James Comer’s black line proves everything is connected. Would the black line lie?
Very much agree! I love the snarky graphs, even though this time I started out reading the screaming red as Comer’s version, only because he *would* use screaming red–had he thought of it. Caught on fast though.
“There’s a lot in Comer’s timeline that makes a great case for impeachment — of Donald Trump.
There’s a lot in his timeline that shows he continues to rely on fraudsters to make his case.”
Has anyone seen a timeline (or such) like this one, using this (and other) available information, that does go directly after Trump and his cronies? Not inferentially, but directly. Even if it omits relevant things that would point away, or if it misleads in some other way. In sum, the exact reverse of typical slanted MAGA propaganda, using all this nutso Hunter Biden stuff. That would be nice.
“Burials” certainly shoots the idea syncing data between devices caused the re-up of that 2016 email.
This feels so much like Bush era disappearing emails all over again.
Don’t assume everything happened at once.
Between overseas trips and the addiction it would have been child’s play to check in on things every 7 months or so.
Oh, no assumption on timing — as I noted in a previous comment I don’t know how application updates figure into this, and between iOS and Google there were plenty between 2016 and 2021, in addition to contact(s) with data by primary user/sketchy investigators/suspicious individuals-groups.
But “Burials” instead of “Burisma” isn’t something that happens during a mere sync of data.
Low priority, but I would really like to see someone with a comprehensive copy of the emails and attachments do a search for every occurrence of the word “burials.” My suspicion is that either bad autocomplete OR a bad global find-and-replace happened. Either may have been limited to specific fields but what if it wasn’t?
I thought about auto-complete, but on my machine, it can only auto-complete addresses that are already listed or which have been received. So my thought was that “burials” has to be someone’s actual account, and it apparently links to a real burisma account. Beyond that, my mind blanks.
The Marco Polo set shows just a few others, which all refer to actual burials. This is really just these two emails threads (and as you’ll note, not even all the ones in that long thread).
Apple Mail will override the recipient quoted name (inside double quotes) with information from Contacts, either on-device or in iCloud depending on whether one is logged in.
So it’s possible someone (either Hunter Biden or the person who attached the hard drive/dataset to *their* Mac device) had a contact for “Burials” with that e-mail address (i.e., Apple Mail rewrote “Person” [email protected] to “Burials” [email protected] based on Contacts data).
(Rayne, I think my domain variations are going to get stuck in review and I apologize and will take steps. Thanks for all you do!)
But at some point some human had to change Burisma to Burials before Apple Mail will perform that override. What triggered that initial change? At this point it’s a rhetorical question because we don’t have all the context about manual changes to data.
No worries about clearing comments through moderation, so long as you understand this is a security measure applicable to all commenters whose identities aren’t algorithmically cleared and may take a bit longer because human at this end. Thanks for your patience.
I could understand a new contact, Burisma, being autocorrected to Burials and not noticed for a while. Was this the start of contacts between Schwerin and Pozharskyi? The other message could be from Schwerin’s mailbox if it was sent to him as bcc, when his name wouldn’t appear in the list of recipients.
With the caveat that exactly how the “readable name” part is genereated varies between mail applications, in most cases it will be automatically added the first time you add that person to your personal conctact list. This will most often happen automagically when you reply to a mail from that person, in which case the “readable name” part of the mail you reply to will be used. It is however also possible to add someone in manually.
Since it’s very unlikely that Pozharskyi would have sent a mail to Schwerin with “Burials” as the readable name, it’s more likely that it’s a manually added contact; ie someone gave Schwerin that email address to contact Burisma. It’s also not unlikely it’s the result of inadvertent tampering of the files afterwards, including a botch global-search-replace of “sma” to “als”.
Marcy probably already is aware of all this information and I apologize if this info duplicates any already on this site. As they used to say on the radio, first time caller long time listener. Grateful for this site.
As a (very) old SMTP e-mail administrator I thought I’d peek at the data and just see what it looks like.
There are 6333 e-mails in the 2019 folder which end abruptly on the 17th/18th of March 2019 (18th in GMT, 17th in PDT). These include a wide variety of human generated, robotically generated and spam e-mails received. These e-mails were received nearly continuously from January through March 17th/18th of 2019.
There are 8 “e-mails” from 2020, and two from 2021.
The 2019 e-mails (to a first scan) contain proper RFC5321 “Received:” headers showing they were sent, routed and received using SMTP protocol. They include dates and believable routing information. None of the 2020 or 2021 “e-mail” files contains any information showing these were sent or received using SMTP. They might well have been edited and saved on a single computer. And as Marcy points out these files contain dates well after the laptop was purloined.
The 2020 e-mails have a contained date (i.e, inside the “envelope”) of “Date: Mon, 31 Aug 2020 14:22:15 -0700” through “Tue, 3 Nov 2020 03:35:12 -0800”. (The final field is an offset to UTC). The 2021 e-mails have contained dates of “Wed, 24 Nov 2021 11:27:06 -0800” and “Wed, 24 Nov 2021 11:27:52 -0800”.
I want to set up a proper container to look at these files and the contents (safely) to do some more analysis. This was only a few minutes’ scanning. Sadly the .eml files have new creation, modify and access times, but there is plenty to look at from a frequency analysis and regularity point of view. And then of course the headers, and the syntax and semantic analysis of the contents.
Wow that would be really helpful. One thing I’m particularly interested in is why so many emails — more than half — have last modified dates in a few days in February 2019.
There are two sets of data that I have access to right now, one is bidenlaptopemails and the other is the ddosecrets data. The latter has the same data packaged two different ways. The timestamps on the ddos data .eml files are all the same: May 6, 2022. The bidenlaptopemails data do seem to have a range of file date/times, beginning on January 4th, 2018 and ending March 8th, 2022. These files I describe below.
Possibly, the original laptop first downloaded these files (from its mail server(s)) beginning on January 4th, 2018, so for example even though the oldest (by filesystem timestamp) file is an e-mail from June 23rd, 2015 (from the header information) it was actually downloaded in 2018. This is consistent with a new laptop being “born” and being configured for someone’s pre-existing e-mail services. As you know there are e-mails from 2009 but every file was filesystem dated post January 4th, 2018.
I do see a range of filesystem timestamps there from Jan 4, 2018 through December 2021 (!). The final transmission date from header information inside these files is (again!) March 18th, 2019. Then some attachment files which I will not look at (yet) that are dated March 8, 2022. So these later-dated files are either modified or re-downloaded after the purloin. Or, possibly, someone copied these files with an app that didn’t preserve modification times, but for the mail files the semi-uniform distribution of dates/times makes this less likely to me at first glance.
You know this already, but for the record please note that with privileges, modification and creation dates can be modified on a hard drive. So everything is sort of silly putty here just to make it more difficult.
I’m not sure which data set you are referring to regarding the February 2019 dates, and whether you are referring to the file system timestamps or the SMTP header information inside the files.
There is a lot going on here, not the least of which are seemingly redundant data sets that have travelled through different hands. I’d be more than happy to look into anything you are interested in specifically. I will keep looking at this after setting up a safe place.
Just re-stumbled on the Washington Post article quoting Matt Green and some of the principals. Real funny business here:
https://www.washingtonpost.com/technology/2022/03/30/hunter-biden-laptop-data-examined/
Just wanted to lift this out of your thoughtful comment, to make sure it didn’t get missed.
As a self-proclaimed “long time listener, first time caller,” thanks for de-lurking and offering your talents to the mutual conversation!
Amen to that, Peterr. I am reading these comments carefully and learning a ton from them. I know next to nothing about the subject, so I appreciate the careful explanations and hope against hope they will continue with more (sequestered) data.
DDOS lists the numbers of last modified date in their own report.
https://ddosecrets.com/wiki/Hunter_Biden_emails
Here’s what February looks like:
February 2019
February 9, 2019: 8,881 .emlx files modified
February 10, 2019: 455 .emlx files modified
February 11, 2019: 65,844 .emlx files modified
February 15, 2019: 4 .emlx files modified
February 16, 2019: 4 .emlx files modified
February 17, 2019: 2 .emlx files modified
February 18, 2019: 9 .emlx files modified
February 19, 2019: 14 .emlx files modified
February 20, 2019: 6 .emlx files modified
February 21, 2019: 42 .emlx files modified
February 22, 2019: 4 .emlx files modified
February 23, 2019: 2 .emlx files modified
February 24, 2019: 3 .emlx files modified
February 26, 2019: 4 .emlx files modified
February 27, 2019: 3 .emlx files modified
February 28, 2019: 6 .emlx files modified
There’s a great deal of reason to think that in that period — basically January 4 through February 13 — this laptop was being packaged up to do the greatest damage. So I’m wondering if there’s a way to figure out where those last modified dates come from.
DDosSecrets has two archives available which both use ZIP format(*A)(*E). I’m going to keep looking and also apply to receive the more detailed backup data (27 GB from the cloud) if it’s not legally ill-advised.
The archives labeled “Native Format” seem to have useful filesystem datestamps but they confused me at first. So many (5930) are from 2021, and two from 2022. This is in the folder dated “2019” !
It looks like 249 have Feb 2019 modification times. 123 have March, and none in April. This is, um, not the same number being reported by DDos. I promise to make a histogram chart of these datestamps and correlate them with the SMTP headers and get them to you somehow.
As you’ve noted, the laptop was apparently left at Ablow’s office in February 2019. If we believe the datestamps we see, the data on this machine was handled and modified repeatedly thereafter.
Someone had Mr. Biden’s password or had authentication (biometric? i.e., HB allowed them to register a finger) to get into the machine. Merely powering the machine on and not logging in would not produce these results.
For better or worse this has my complete attention now, and to some degree I was created to look at this particular issue. I will spare you the details of that for the moment. It began in the late 1970s…
Up to now I’ve had a mental roadblock regarding The Laptop; every time a news story came up I forcefully ignored it. I figured it was just another weak-sauce Podesta-style e-mail operation by the usual people. Now it seems much worse: reading your threads in detail and looking at the dates and contents of news stories it appears this has been a continuous, adaptive and largely successful operation combining Butter Emails with Gamergate to launder disinformation.
Using the Herridges and Nuzzis as data mules to propagate the memes from nypost through into more conventional outlets (CBS, New York Magazine) and on the the NY Times. This is a full scale infodemiologic infection (to borrow from Eysenbach) on the shoulders of an unwell son and his personal problems. It’s repellent and execrable.
Anyhow, in order of preference, one would prefer:
1) the original drive(*B)
2) a sector copy of the whole original drive(*C)
3) a file-by-file copy (i.e., Carbon Copy)
3a) a backup (i.e, cloud or Time Machine) of the partition
3b) an archive (cpio or tar, &etc) of the partition
4) a ZIP file of some files
5) a description of the dates and times
As you go down the list more forensic data is lost, and 4 and 5 have lost much really useful information. Still, there’s a ton of good info in the SMTP headers of received e-mails and maybe datestamps.
*A – ZIP only stores one datestamp (modification)(*E) vs. three (or more) in Mac OSX (creation, modification, “change” for permissions/owner)
*B – the original drive (if spinning) will contain recoverable blocks that have been deleted(*D) and log files showing access/download times for e-mail services and other operations. SSD drives (do we know which one it was? probably SSD) use a gnarly method to re-use blocks and make it harder to do block level forensics. In any case I don’t expect to be offered the disc.
*C – a real forensic copy (not whatever John Paul Mac Isaac was doing between system crashes as he described it)
*D – depending on whether the laptop used filesystem encryption (I bet it didn’t) the ‘deleted’ file parts easily could still be visible along with file metadata on a spinning drive.
*E – there are extended fields for more datestamps but I am not seeing them in use by DDos
My apologies for spamming this thread and not being totally up-to-date on this issue. I am trying to be as clear as possible so the other sysadmins don’t have to add or clarify details, and because I think you don’t forget anything.
Georgie, this is *not* spam. Many thanks for adding your technical voice to the conversation!
“Louis Armstrong, The Commanders – ‘Zat You, Santa Claus? (Visualizer)”
https://www.youtube.com/watch?v=cqIpxPvhb_8
Welcome! Always good to see another old nerd here. To answer one question, we’re definitely dealing with SSD wrt the Mac drive(s).
I had a little chuckle when I read this:
The chuckle was because that is exactly how I reacted to the “Biden laptop” stories and I’ve come to the same conclusion.
Most of all, I wanted to thank you for this:
I had suspected that and not yet had time to verify it because I’ve only looked at the two emails (the 2016/2020 pair).
As another not-*that*-old-nerd, I want to thank both of you for your technical insights (and Dr Wheeler for all her tireless work in this). I’m more of a generalist nerd and only know that the magic you both perform is real, with a vague sense of how it’s done, but without the detailed knowledge to perform it myself.
And yes, on privileges. Hunter had access to Hallie’s account for broad periods of time. He (or someone) turned family sharing off and on at two or three different periods.
I THINK Schwerin had access to Hunter’s work email, which would have become apparent to anyone who had hacked Hunter’s laptops.
We should also keep in mind that someone with the right technical skill (think Russian government hackers trying to plant a modified email) could in principle, modify any of this data including these SMTP timestamps in a way that left behind no traces.
There’s a reason chain of custody is important when forensic evidence is collected.
But the process of “packaging up” the laptop appears to have been a clown show, and the SMTP headers may be enough to prove that it was tampered with and to strongly suggest that the tampering occurred at specific times. (I.e. we can’t absolutely prove the timestamps are authentic, but why would someone with the technical skill to forge them even leave such traces at all?)
“There’s a reason chain of custody is important when forensic evidence is collected.”
THIS. Like Georgie Tirebiter, I had tuned out much of the “laptop” remix tales starting with the same WaPo story he cites, and for the same reasons. EW’s meticulous analysis revived my hope that a true accounting might be possible, and now that Georgie T has entered the fray it feels like between them (and the others here) the myths being propounded could be shot down.
All power to you folks!
There seem to be a lot of Bozos on this bus (laptop).
Thank you for your dilligent analysis, and anything that stimulates the site proprietor and commenters. (appreciate the Firesign Theatre reference)
..’bozo’s on this bus’ brought to mind’s eye the bus load of ‘Croco-Stimpys’ mindlessly chiming Happy Happy, Joy Joy,, & maybe Georgie can be the site’s own regnaD kciN, but with more success. Thanks to All Here!, this just keeps getting better & better,,
Yesterday I spent some some looking for information about metadata in gmail footers. Unfortunately, I neglected to save some useful info and forgot where I saw it. Then I looked at the wiki page about email migration. I was just about to mention that it would be helpful if an SMTP e-mail administrator could lend some insight about privileges, etc. And when I came back to this post, there was Georgie!
I have no skills in this area at all. But in my naive brain, it looks like some kind of migration happened on some of the dates Marcy is concerned about:
February 9, 2019: 8,881 .emlx files modified
February 10, 2019: 455 .emlx files modified
February 11, 2019: 65,844 .emlx files modified
So, to make this sound more plausible, Comer disappeared entire people from the events (people who if asked, would counter his claims), disappeared events that would counter his claims, reorganized some events that would blow the entire timeline into pieces if properly ordered, and is now hoping no one looks too closely at it?
Yeah, that sounds like the standard Repub “investigation” to me…
I would think that even a kangaroo court would have some semblance of a real kangaroo.
Newsflash: Marsupial on the loose in Ontario –
https://www.cbc.ca/news/canada/toronto/kangaroo-on-the-loose-located-oshawa-1.7046893
wHEN i saw the Dec. 2015 date, it really made me wonder. These Republicans were elected to govern one the most powerful countries on earth and here they are playing pick up sticks 9 years later with the same toys. Its time for these politicians to stop “playing” and get on with the business of the country. The U.S.A. along with a number of other countries have somethings which need to be attended to, roads, bridges, schools, health care, interest rates…………
If that is too much for them, send them to a play room and have the remaining adults do the business of the country.
The U.S.A. is too large and important a country to be playing childish games. IF some of these politicians continue at this rate the American government could be come irrelevant.
“Its time for these politicians to stop “playing” and get on with the business of the country”
The problem is, most people consider the business of the country to be actually running it, but the Republicans see the business of the country as NOT running it (“government is the problem”, remember?) and instead working on entrenching themselves in power via any means possible.
“What we’re seeing today is that the Biden family is under a whole lot more investigative scrutiny than what the media has reported. I think that you’re seeing our investigation that’s shined a light on the many wrongdoings of the Biden family has picked up a lot of credibility today, because now we see that there are a lot of crimes that this family’s committed and that played out in court today.”
James Comer, Fox News, July 26, 2023
OMG, will someone get this guy a high chair, milk and cookies, and some Legos?
A bit of rudimentary Spanish wordplay:
¡Ey—Republicanos! Comer mierda. También, Comer es mierda.
“RHB was originally told that the diamond was worth $10,000, but James B took it to a friend of his and found out that it was worthless.”
Hmm, OK, hope your friend’s trustworthy but how did a diamond worth nothing or 10k come to be worth 80k? Is Bobulinski able to value gemstones from a distance (possibly even without being present)?
So Zlochevsky “bribed then Vice-President Biden $5 million and $5 million for his son” and was investigated by Ukrainian authorities for bribery. Given the MAGA habit of accusing their opponents of their own sins, the obvious inference is that Zlochevsky gave Trump and his son(s), not forgetting Giuliani, millions to shut down the US investigation.
ps offering millions not billions
OT, is it time to start a trash talk thread? Army-Navy is this week and we just had a gross CFP vote.
Seriously, Alabama ahead of Florida State? Even with their third string freshman QB, they beat the spread by 8 1/2 points. The released excuse was that the third string QB means that FSU ‘can’t’ perform at a top-four level but their D shut down a highly ranked Louisville team knowing that their QB situation was suboptimal. I recall BYU getting a national championship with a far lighter resume. FWIW, Texas beat Alabama in Tuscaloosa so Saban would be the first one out in my book.
Ah, Army-Navy. If Army wins they’ll get the C in C trophy but if Navy wins I think the AFA retains it. Some of my colleagues at Canoe U (I was ROTC at Berkeley, an academic powerhouse) would tell me that all exams, reports, etc. would be deferred because all that would happen is that ‘Army-Navy’ would be the only answer. I wonder if it is also true at West Point.
On a semi-related note, where are the Space Farce guardians being trained? With the rest of the Chair Force in CO or somewhere else? While they could fulfill a key role in all fairness with cyber and satellite warfare, we’ll also wonder what they’ll do for an identity event like the most of us have. The moons of Endor only exist at Lucasfilms.
Oh, and the Bears just three-peated in water polo. It’s not a sport for the timid. My brother’s best friend played and they usually wore a half dozen Speedos in a game in order to have one left at the end.
I just put up an open thread. You can bring your trash talk there and any fruity holiday bread/cake.
Holy smokes, Comer went all in today on Joe Biden buying Hunter a car and Hunter paying him back. Do these people have any control over how idiotic they get?