Bret Baier’s False Claim, the Escort Service, and Former Fox News Pundit Keith Ablow
Deep into one version of what is referred to as the “Hunter Biden” “laptop,” (according to reports done for Washington Examiner by Gus Dimitrelos*) there’s a picture of a check, dated November 14, 2018, for $3,400, paid to a woman with a Slavic name. The check bears a signature that matches others, attributed to Hunter Biden, from the “laptop” also attributed to him. Along with a line crossing out Hunter’s ex-spouse’s name on the check, the check was marked on the memo line: “Blue Water Wellness” along with a word that is illegible–possibly “Rehab.”
The check appears in a chat thread, dated November 26, 2018, apparently initiated to set up tryst with an escort in New York City. Just over 12 hours after setting up that tryst, the Russian or Ukrainian woman who manages the escort service, Eva, wrote back, asking Hunter if he was in New York, because she had a problem with his check, that $3,400 check dated twelve days earlier. Hunter was effusively apologetic, and offered to pay the presumed sex worker via wire, because it’s the only way he could be 100% certain it would get to her. Shortly thereafter, he sent two transfers from his Wells Fargo account, $3,200 plus $30 fees, directly to the woman’s bank account, and $800 via Zelle drawn on Wells Fargo.
Those transfers from Hunter Biden’s Wells Fargo account to a presumed sex worker with a Slavic name took place between the day, October 31, 2018, when IRS Agent Joseph Ziegler, newly arrived on IRS’ international tax squad, launched an investigation into an international online sex business and the day, December 10, 2018, when Ziegler would piggyback off that sex business investigation to launch an investigation into Hunter Biden. The Hunter Biden investigation was initially based off a Suspicious Activity Report from Wells Fargo sent on September 21, 2018 and from there, quickly focused on Hunter’s ties to Burisma, precisely the investigation the then President was demanding.
Understand: The entire five year long investigation of Hunter Biden was based off payments involving Wells Fargo quite similar to this one, the check for $3,400 to a sex worker associated (in this case, at least) with what Dimitrelos describes as an escort service.
Research on the company yielded bank reports indicating that [Hunter Biden] made payments to a U.S. contractor, who also had received payments from that U.K. company.
Only, this particular payment — the need to wire the presumed sex worker money to cover the check — ties the escort service to one of the businesses of former Fox News pundit Keith Ablow: Blue Water Wellness, a float spa just a few blocks down the road from where Ablow’s psychiatric practice was before it got shut down amid allegations of sex abuse of patients and a DEA investigation. Emails obtained from a different version of the “laptop” show that on November 13, Blue Water Wellness sent Hunter an appointment reminder, albeit for an appointment on November 17, not November 14. That appointment reminder is the first of around nine appointment reminders at the spa during the period.
The tryst with the presumed sex worker with the Slavic name does appear to have happened overnight between November 13 and 14. Between 1:58 and 6:33AM, there were two attempts to sign into Hunter’s Venmo account from a new device, five verification codes sent to his email, and two password resets, along with the addition of the presumed sex worker to his Zelle account at Wells Fargo, which he would use to send her money over a week later. All that makes it appear like they were together, but Hunter didn’t have his phone, the phone he could use to pay her and so tried to do so from a different device. Maybe, he gave up, and simply wrote her a check, from the same account on which that Zelle account drew.
None of which explains why he appears to have written “Blue Water Wellness” on a check to pay a presumed sex worker. Maybe he was trying to cover up what he was paying for. Maybe he understood there to be a tie. Or maybe it was the advertising Blue Water did at the time.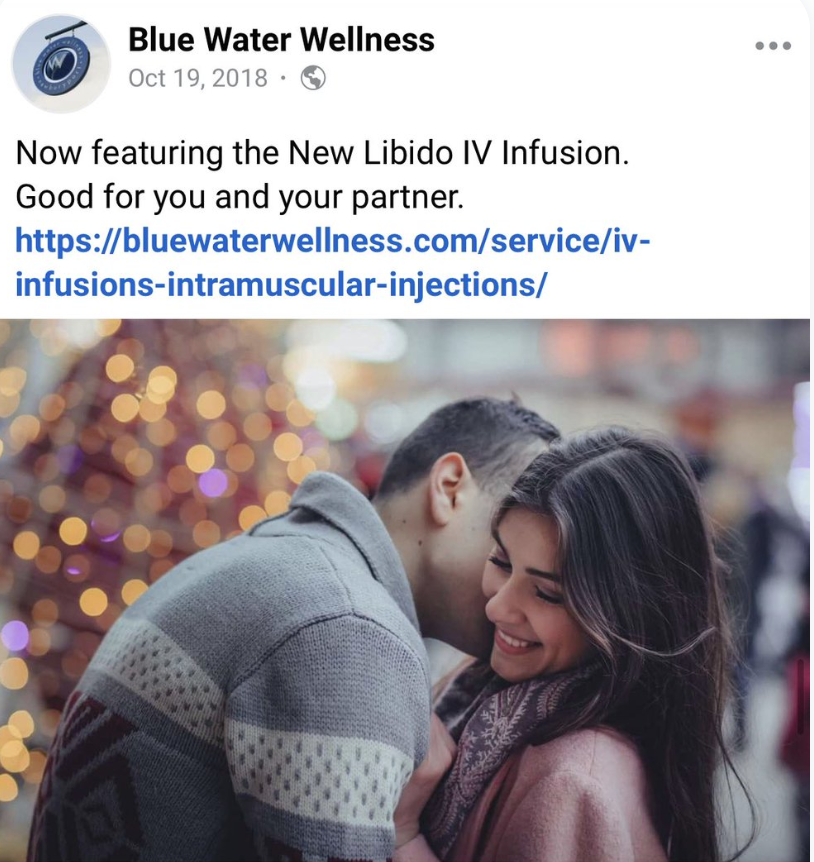
Deep in a different part of the laptop analyzed by Dimitrelos, though, a deleted invoice shows that Hunter met with former Fox News pundit Keith Ablow on the same day as Hunter apparently wrote that check to the presumed sex worker. The deleted invoice reflects two 60-minute sessions billed by Baystate Psychiatry, the office just blocks away from the float spa.
Emails obtained from a different version of the “Hunter Biden” “laptop” show that at some point on November 26, 2018, as Hunter first arranged a tryst in New York City and then, no longer in New York, sent a wire directly from Wells Fargo to the presumed sex worker, someone accessed Hunter’s Venmo account from a new device — successfully this time — one located in Newburyport, MA, where former Fox News pundit Keith Ablow’s businesses were.
There are a number of things you’d need to do to rule out the possibility of Russian involvement in the process by which a laptop purportedly belonging to Hunter Biden showed up at the Wilmington repair shop of John Paul Mac Isaac, from there to be shared with Rudy Giuliani, who then shared it with three different Murdoch outlets and a ton of other right wing propagandists, many of them members of Congress.
One of those would be to rule out that any of the sex workers tied to this escort service had a role in compromising Hunter Biden’s digital identity, thereby obtaining credential information that would make it easy to package up a laptop that would be especially useful to those trying to destroy the life of the son of Donald Trump’s opponent. There’s no evidence that any of the sex workers were involved, but throughout 2018, there are a number of device accesses involving Hunter’s Venmo account, the iCloud account packaged up on “the laptop,” and different Google accounts — including between the day on November 13 when Hunter appears to have met the woman with the Slavic name and the date on November 26 when he wired her money — that should at least raise concerns that his digital identity had been compromised. I’ve laid out just a fraction of them in this post and this post, both of which focus on the later period when Hunter was in the care of the former Fox News pundit.
If you wanted to compromise Hunter Biden, as certain Russian-backed agents in Ukraine explicitly did, doing so via the sex workers, drug dealers, and fellow junkies he consorted with in this period would be painfully easy. Indeed, in Hunter’s book, he even described other addicts walking off with his, “watch or jacket or iPad—happened all the time.” Every single one of those iPads that walked away might include the keys to Hunter’s digital life, and as such, would be worth a tremendous amount of money to those looking to score their next fix. To rule out Russian involvement, you’d have to ID every single one of them and rule out that they were used for ongoing compromise of Hunter or, barring that, you’d have to come up with explanations, such as the likelihood that Hunter was trying to pay a sex worker but didn’t have his phone with him and so used hers, for the huge number of accesses to his accounts, especially the iCloud account ultimately packaged up.
Of course, explaining how a laptop purportedly belonging to Hunter Biden showed up at Mac Isaac’s shop would also require explaining how a laptop definitely belonging to Hunter Biden came to be left in former Fox News pundit Keith Ablow’s possession during precisely the same period when (it appears) Hunter Biden’s digital life was getting packaged up, a laptop Ablow did nothing to return to its owner and so still had when the DEA seized it.
Bret Baier lied about the Hunter Biden laptop
Given the unanswered questions about the role of a former Fox News pundit in all this, you’d think that Fox personalities would scrupulously adhere to the truth about the matter, if for no other reason than to avoid being legally implicated in any conspiracies their former colleague might have been involved with, or to avoid kicking off another expensive defamation lawsuit.
Sadly, Bret Baier couldn’t manage to stick to the truth in his attempt to sandbag former CIA Director Leon Panetta on Friday. Baier debauched the gravity of an appearance purportedly focused on the Hamas attack and aftermath, with what he must have thought was a clever gotcha question about a letter Leon Panetta signed in October 2020 stating the opinion that the emails being pitched by Murdoch outlet New York Post, “has all the classic earmarks of a Russian information operation.” The letter not only expressed an opinion, but it cited four specific data points and two observations about known Russian methods, all of which were and remain true to to this day.
And in the process, Bret Baier made a false claim.
Bret Baier made a false claim and all of Fox News’ watchers and all the other propagandists made the clip of Bret Baier making a false claim go viral, because they apparently either don’t know or don’t care that Baier couldn’t even get basic facts right. They are positively giddy that Baier used the tragedy of a terrorist attack to demonstrate his own ignorance or willful deceit about Fox’s favorite story, Hunter Biden’s dick pics.
From the get-go, Baier adopted a rhetorical move commonly used by Murdoch employees and frothy right wingers sustaining their blind faith in “the laptop:” He conflated “the laptop” with individual emails.
Baier: I’d be remiss if I didn’t ask you about that letter you signed onto from former intelligence officials saying that the laptop and the emails had all the classic earmarks of a Russian information operation. Obviously the New York Post and others saying the Hunter Biden letter was the real disinformation all along. Um, that letter was used in the debate, I haven’t asked you this. But do you have regrets about that, now looking back, knowing what you know now? [my emphasis]
The spooks’ letter Panetta signed addressed emails, not “the laptop.” The only use of the word “laptop” in the letter was in labeling this a potential “laptop op,” a way to package up emails meant to discredit Joe Biden. The letter even includes “the dumping of accurate information” among the methods used in Russian information operations.
Having conflated emails and “the laptop,” Baier then asked whether Panetta thinks “it,” now referring just to “the laptop,” not even the hard drives of copies from the laptop in question, was real.
Panetta: Well, you know, Bret, I was extremely concerned about Russian interference and misinformation. And we all know it. Intelligence agencies discovered that Russia had continued to push disinformation across the board. And my concern was to kind of alert the public to be aware that these disinformation efforts went on. And frankly, I haven’t seen any evidence from any intelligence that that was not the case.
Baier: You don’t think that it was real?
Having first conflated emails and the laptop, then substituted the laptop for the emails addressed in the letter, Baier then falsely claimed that, “Hunter Biden said it was his laptop.”
Panetta: I think that, I think that disinformation is involved here. I think Russian disinformation is part of what we’re seeing everywhere. I don’t trust the Russians. And that’s exactly why I was concerned that the public not trust the Russians either.
Baier: I don’t want to dwell on this because we have bigger things to talk about. Bigger urgency. But obviously, Hunter Biden said it was his laptop, and this investigation continues. [my emphasis]
I understand how frothy right wingers misunderstand what Hunter Biden has said about the data associated with “the laptop,” but Baier presents as a journalist, and you’d think he’d take the time to read the primary documents.
Hunter Biden admits some data is his, but denies knowledge of the “laptop”
The claim that Hunter Biden has said “the laptop” was his arises from three lawsuits: first, from Hunter Biden’s response and counterclaim to John Paul Mac Isaac’s lawsuit, then of Hunter’s lawsuit against Garrett Ziegler, and finally, the lawsuit against Rudy Giuliani.
Regarding the first of those filings, Hunter Biden based his countersuit against JPMI on an admission that JPMI came into possession of electronically stored data, at least some of which belonged to him. But he specifically did not admit that JPMI “possessed any particular laptop … belonging to Mr. Biden.”
5. In or before April 2019, Counterclaim Defendant Mac Isaac, by whatever means, came into possession of certain electronically stored data, at least some of which belonged to Counterclaim Plaintiff Biden.1
1 This is not an admission by Mr. Biden that Mac Isaac (or others) in fact possessed any particular laptop containing electronically stored data belonging to Mr. Biden. Rather, Mr. Biden simply acknowledges that at some point, Mac Isaac obtained electronically stored data, some of which belonged to Mr. Biden.
Regarding JPMI’s claims that Hunter dropped off the laptop,
169. HUNTER knowingly left his laptop with Plaintiff on April 12, 2019.
170. Soon thereafter HUNTER returned to Plaintiff’s shop to leave an external hard drive to which Plaintiff could transfer the data from HUNTER’s laptop.
171. HUNTER never returned to Plaintiff’s shop pick up his laptop
Hunter denied sufficient knowledge to answer all of them.
169. Mr. Biden is without knowledge sufficient to admit or deny the allegations in paragraph 169.
170. Mr. Biden is without knowledge sufficient to admit or deny the allegations in paragraph 170.
171. Mr. Biden admits that, if he ever had visited before, he did not return to Plaintiff’s shop.
In response to JPMI’s claim that Hunter knew of the phone call his lawyer, George Mesires, made to JPMI in October 2020 and the email follow-up that in any case doesn’t substantiate what JPMI claimed about the phone call,
31. On October 13, 2020, Plaintiff received a call from Mr. George Mesires,1 identifying himself as HUNTER’s attorney, asking if Plaintiff still had possession of his client’s laptop and following up thereafter with an email to the Plaintiff. Copy of email attached as EXHIBIT C.
[snip]
174. HUNTER’s attorney, George Mesires contacted Plaintiff on October 13, 2020 about the laptop.
Hunter admitted that Mesires was his attorney but denied knowing anything more.
31. Mr. Biden admits that Mr. George Mesires was his attorney. Mr. Biden is without knowledge sufficient to admit or deny the remaining allegations in paragraph 31.
[snip]
174. Mr. Biden admits that Mr. Mesires was his attorney. Mr. Biden is without knowledge sufficient to admit or deny the remaining allegations in paragraph 174.
In response to JPMI’s claim that Hunter Biden said something about the laptop without mentioning JPMI,
172. When asked about the laptop in a television interview broadcast around the world, HUNTER stated, “There could be a laptop out there that was stolen from me. It could be that I was hacked. It could be that it was the – that it was Russian intelligence. It could be that it was stolen from me. Or that there was a laptop stolen from me.” See https://edition.cnn.com/2021/04/02/politics/hunterbiden-laptop/index.html.
173. HUNTER knew it was his laptop.
Hunter Biden admitted he made the comment that didn’t mention JPMI — a comment on which JPMI based a $1.5M defamation claim!! — but again denied knowing whether or not the laptop was his.
172. Admitted and Mr. Biden further answers that the statement makes no mention of or even a reference to Plaintiff.
173. Mr. Biden is without knowledge sufficient to admit or deny the allegations in paragraph 173.
Of some interest, in response to JPMI’s claim that the information that appeared in the NYPost came from Hunter, who voluntarily left his laptop with JPMI,
67. The information contained in the NY POST exposé came from HUNTER who voluntarily left his laptop with the Plaintiff and failed to return to retrieve it.
Hunter outright denied the claim.
67. Denied.
Hunter Biden claimed that Rudy hacked Hunter’s data
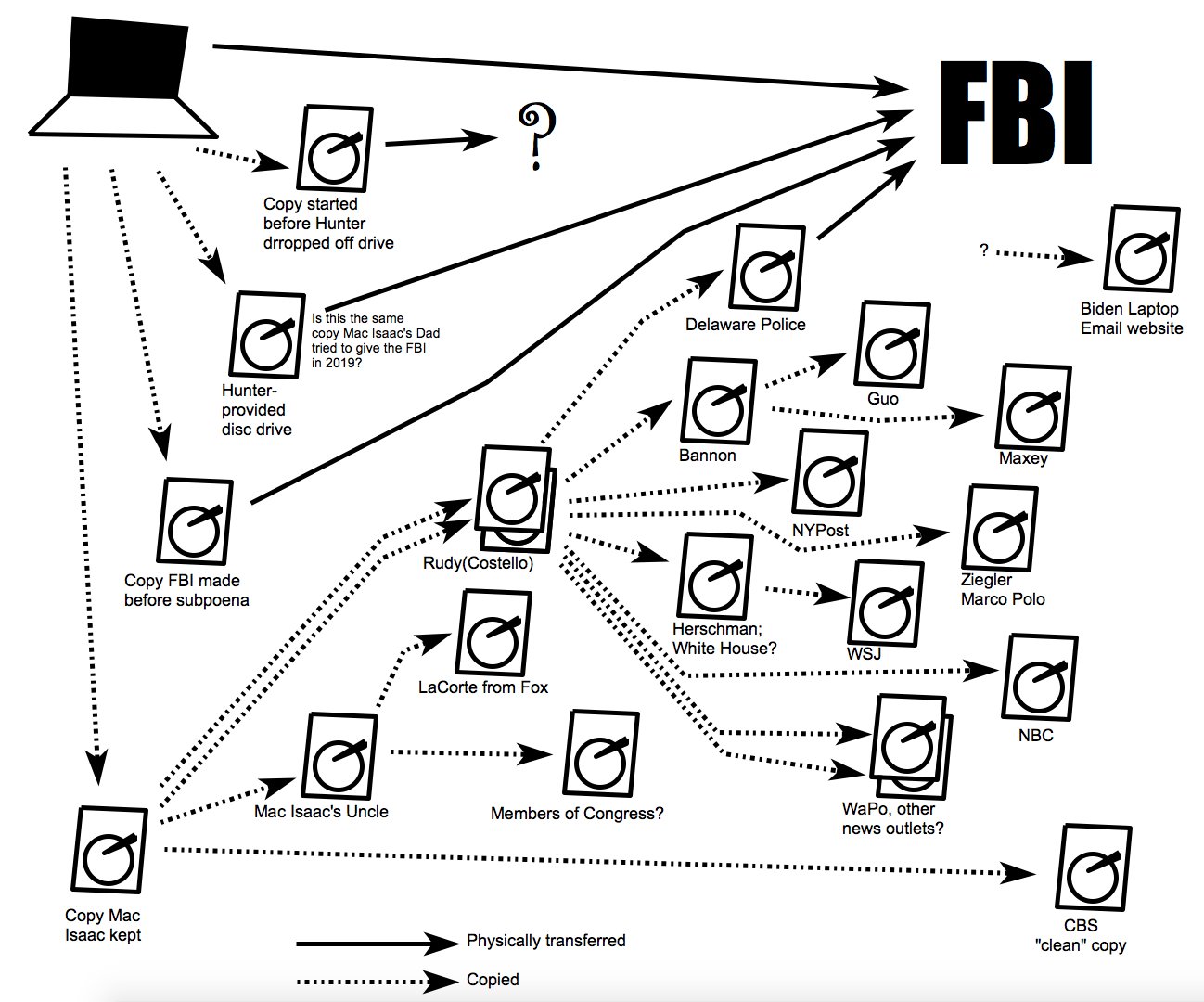
That last claim — the outright denial that the data in the NYPost story came from Hunter — is of particular interest given something Denver Riggleman recently said. He described that the Hunter Biden team now has the data that JPMI shared with others — apparently thanks to this countersuit — and they’ve used it to compare with the data distributed forward from there.
Also, we know now, since the Hunter Biden team has the John Paul Mac Isaac data that was given to Rudy Giuliani and given to CBS, we also know that that data had no forensic chain of custody and it was not a forensic copy of any type of laptop, or even multiple devices that we can see. It was just a copy-paste of files, more or less.
[snip]
We know that there’s different data sets in different portions of the Internet attributed to Hunter’s data — or, to Hunter’s laptop.
[nip]
Now that we do have forensic data — Hunter Biden team has more foensic data than anybody else out there — we can actually start to compare and contrast. And that’s why you see the aggressiveness from the Hunter Biden legal team.
The lawsuit against Rudy and Costello claims that at some point, Rudy and Costello did things that amount to accessing Hunter’s data unlawfully. Hacking.
23. Following these communications, Mac Isaac apparently sent via FedEx a copy of the data he claimed to have obtained from Plaintiff to Defendant Costello’s personal residence in New York on an “external drive.” Once the data was received by Defendants, Defendants repeatedly “booted up” the drive; they repeatedly accessed Plaintiff’s account to gain access to the drive; and they proceeded to tamper with, manipulate, alter, damage and create “bootable copies” of Plaintiff’s data over a period of many months, if not years. 2
24. Plaintiff has discovered (and is continuing to discover) facts concerning Defendants’ hacking activities and the damages being caused by those activities through Defendants’ public statements in 2022 and 2023. During one interview, which was published on or about September 12, 2022, Defendant Costello demonstrated for a reporter precisely how Defendants had gone about illegally accessing, tampering with, manipulating and altering Plaintiff’s data:
“Sitting at a desk in the living room of his home in Manhasset, [Defendant Costello], who was dressed for golf, booted up his computer. ‘How do I do this again?’ he asked himself, as a login window popped up with [Plaintiff’s] username . . .”3
By booting up and logging into an “external drive” containing Plaintiff’s data and using Plaintiff’s username to gain access Plaintiff’s data, Defendant Costello unlawfully accessed, tampered with and manipulated Plaintiff’s data in violation of federal and state law. Plaintiff is informed and believes and thereon alleges that Defendants used similar means to unlawfully access Plaintiff’s data many times over many months and that their illegal hacking activities are continuing to this day.
[snip]
26. For example, Defendant Costello has stated publicly that, after initially accessing the data, he “scrolled through the laptop’s [i.e., hard drive’s] email inbox” containing Plaintiff’s data reflecting thousands of emails, bank statements and other financial documents. Defendant Costello also has admitted publicly that he accessed and reviewed Plaintiff’s data reflecting what he claimed to be “the laptop’s photo roll,” including personal photos that, according to Defendant Costello himself, “made [him] feel like a voyeur” when he accessed and reviewed them.
27. By way of further example, Defendant Costello has stated publicly that he intentionally tampered with, manipulated, and altered Plaintiff’s data by causing the data to be “cleaned up” from its original form (whatever this means) and by creating “a number of new [digital] folders, with titles like ‘Salacious Pics’ and ‘The Big Guy.’” Neither Mac Issac nor Defendants have ever claimed to use forensically sound methods for their hacking activities. Not surprisingly, forensic experts who have examined for themselves copies of data purportedly obtained from Plaintiff’s “laptop” (which data also appears to have been obtained at some point from Mac Isaac) have found that sloppy or intentional mishandling of the data damaged digital records, altered cryptographic featuresin the data, and reduced the forensic quality of data to “garbage.”
2 Plaintiff’s investigation indicates that the data Defendant Costello initially received from Mac Isaac was incomplete, was not forensically preserved, and that it had been altered and tampered with before Mac Issac delivered it to Defendant Costello; Defendant Costello then engaged in forensically unsound hacking activities of his own that caused further alterations and additional damage to the data he had received. Discovery is needed to determine exactly what data of Plaintiff Defendants received, when they received it, and the extent to which it was altered, manipulated and damaged both before and after receipt.
3 Andrew Rice & Olivia Nuzzi, The Sordid Saga of Hunter Biden’s Laptop, N.Y. MAG. (Sept. 12, 2022), https://nymag.com/intelligencer/article/hunter-biden-laptop- investigation.html.
I don’t think Hunter’s team would have compared the data Rudy shared with the NYPost before Hunter denied, outright, that “The information contained in the NY POST exposé came from HUNTER.” But based on what Riggleman claimed, they have since, and did compare it, before accusing Rudy and a prominent NY lawyer of hacking Hunter Biden’s data.
Hunter Biden’s team admits they don’t know the precise timing of this: “the precise timing and manner by which Defendants obtained Plaintiff’s data remains unknown to Plaintiff.” DDOSecrets points to several emails that suggest Rudy and Costello did more than simply review available data, however. For example, it points to this email created on September 2, 2020, just after the former President’s lawyer got the hard drive.
September 2, 2020: A variation of a Burisma email from 2016 is created and added to the cache. The email and file metadata both indicate it was created on September 2, 2020.
But the lawsuit, if proven, suggests the possibility that between the time JPMI shared the data with Rudy and the time Rudy shared it with NYPost, Rudy may have committed federal violations of the Computer Federal Fraud and Abuse Act — that is, Hunter alleges that between the time JPMI shared the data and the time NYPost published derivative data, Rudy may have hacked Hunter Biden’s data.
If he could prove that, it means the basis Twitter gave for throttling the NYPost story in October 2020 — they suspected the story included materials that violated Twitter’s then prohibition on publishing hacked data — would be entirely vindicated.
For example, on October 14th, 2020, the New York Post tweeted articles about Hunter Biden’s laptop with embedded images that look like they may have been obtained through hacking. In 2018, we had developed a policy intended to, to prevent Twitter from becoming a dumping ground for hacked materials. We applied this policy to the New York Post tweets and blocked links to the articles embedding those source materials. At no point did Twitter otherwise prevent tweeting, reporting, discussing or describing the contents of Mr. Biden’s laptop.
[snip]
My team and I exposed hundreds of thousands of these accounts from Russia, but also from Iran, China and beyond. It’s a concern with these foreign interference campaigns that informed Twitter’s approach to the Hunter Biden laptop story. In 2020, Twitter noticed activity related to the laptop that at first glance bore a lot of similarities to the 2016 Russian hack and leak operation targeting the dnc, and we had to decide what to do, and in that moment with limited information, Twitter made a mistake under the distribution of hacked material policy.
If Hunter can prove that — no matter what happened in the process of packaging up this data before it got to JPMI, whether it involved the compromise of Hunter’s digital identity before JPMI got the data, which itself would have been a hack that would also vindicate Twitter’s throttling of the story — it would mean all the data that has been publicly released is downstream from hacking.
For Twitter, it wouldn’t matter whether the data was hacked by Russia or by Donald Trump’s personal lawyer, it would still violate the policy as it existed at the time.
Importantly, this remains a claim about data, not about a laptop. The lawsuit against Rudy and Costello repeats the claim made in the JPMI counterclaim: while JPMI had data, some of which belongs to Hunter, Hunter is not — contrary to Bret Baier’s false claim — admitting that, “Hunter Biden said it was his laptop.”
2. Defendants themselves admit that their purported possession of a “laptop” is in fact not a “laptop” at all. It is, according to their own public statements, an “external drive” that Defendants were told contained hundreds of gigabytes of Plaintiff’s personal data. At least some of the data that Defendants obtained, copied, and proceeded to hack into and tamper with belongs to Plaintiff.1
1 This is not an admission by Plaintiff that John Paul Mac Isaac (or others) in fact possessed any particular laptop containing electronically stored data belonging to Plaintiff. Rather, Plaintiff simply acknowledges that at some point, Mac Isaac obtained electronically stored data, some of which belonged to Plaintiff.
In two lawsuits, Hunter Biden explicitly said that he was not admitting what Baier falsely claimed he had.
I know this is Fox News, but Baier just blithely interrupted a sober discussion about a terrorist attack to make a false claim about “the laptop.”
Hunter Biden claims that Garrett Ziegler hacked Hunter’s iPhone
Hunter Biden’s approach is different in the Garrett Ziegler lawsuit, in which he notes over and over that Ziegler bragged about accessing something he claimed to be Hunter Biden’s laptop, but which was really, “a hard drive that Defendants claim to be of Plaintiff’s ‘laptop’ computer.” By the time things got so far downstream to Ziegler, there was no pretense this was actually a laptop, no matter what Baier interrupted a discussion about terrorism to falsely claim.
But that paragraph explicitly denying admission about this being a laptop is not in the Ziegler suit.
There’s a likely reason for that. The core part of the claim against Ziegler is that Ziegler unlawfully accessed a real back-up of Hunter Biden’s iPhone, which was stored in encrypted form in iTunes — just as I laid out had to have happened months before that lawsuit.
28. Plaintiff further is informed and believes and thereon alleges that at least some of the data that Defendants have accessed, tampered with, manipulated, damaged and copied without Plaintiff’s authorization or consent originally was stored on Plaintiff’s iPhone and backed-up to Plaintiff’s iCloud storage. On information and belief, Defendants gained their unlawful access to Plaintiff’s iPhone data by circumventing technical or code-based barriers that were specifically designed and intended to prevent such access.
29. In an interview that occurred in or around December 2022, Defendant Ziegler bragged that Defendants had hacked their way into data purportedly stored on or originating from Plaintiff’s iPhone: “And we actually got into [Plaintiff’s] iPhone backup, we were the first group to do it in June of 2022, we cracked the encrypted code that was stored on his laptop.” After “cracking the encrypted code that was stored on [Plaintiff’s] laptop,” Defendants illegally accessed the data from the iPhone backup, and then uploaded Plaintiff’s encrypted iPhone data to their website, where it remains accessible to this day. It appears that data that Defendants have uploaded to their website from Plaintiff’s encrypted “iPhone backup,” like data that Defendants have uploaded from their copy of the hard drive of the “Biden laptop,” has been manipulated, tampered with, altered and/or damaged by Defendants. The precise nature and extent of Defendants’ manipulation, tampering, alteration, damage and copying of Plaintiff’s data, either from their copy of the hard drive of the claimed “Biden laptop” or from Plaintiff’s encrypted “iPhone backup” (or from some other source), is unknown to Plaintiff due to Defendants’ continuing refusal to return the data to Plaintiff so that it can be analyzed or inspected. [my emphasis]
Hunter Biden’s team has backup for this assertion, thanks to the notes Gary Shapley took in an October 22, 2022 meeting about what was an actual laptop JPMI handed over to the FBI. On that laptop — which the FBI had confirmed was associated with Hunter Biden’s iCloud account and which it tied to data that could all be falsifiable to someone in possession of the laptop, which had means to intercept and redirect emails and calls to Hunter’s real devices, but which the FBI still had not validated 10 months after obtaining it — the iPhone content was encrypted.
Laptop — iphone messages were on the hard drive but encrypted they didn’t get those messages until they looked at laptop and found a business card with the password on it so they were able to get into the iphone messages [my emphasis]
Even the FBI needed to find a password to access the iPhone content that Ziegler has bragged about accessing. (Note: there have been four known accesses to this data, and every single one of them claims to have used a different means to break the encryption, which in my mind raises real questions about the nature of the business card). But the FBI had a warrant. Ziegler did not.
There are still a great deal of questions one would have to answer before entirely ruling out that Russians were involved in the process of packaging up Hunter Biden’s digital identity; the possible role of a Russian escort service is only one of at least three possible ways Russia might be involved. Yet Bret Baier is unwilling to pursue those questions — starting with the unanswered questions about the role that Baier’s former Fox News colleague played.
But with all those unanswered questions, Baier was nevertheless willing to interrupt a discussion about terrorism to make false claims about what is known.
Update: I’ve taken out that this was specifically a Russian escort service. Some outlets claim Eva is Ukrainian. Dimitrelos does claim that Hunter searched for “Russian escort service,” though.
Update: Added the Bluewater Wellness Intramuscular Injection ad from October 2018.
Update: Added the observation about a newly created email from DDOSecrets.
Update: I was reminded of Bret Baier’s opinion in the same days when Leon Panetta was expressing his doubts about this story.
During a panel on his Thursday evening show, Baier addressed the Post‘s story and the decision by both Twitter and Facebook to limit sharing of the story on their respective platforms because of concerns about spreading misinformation. The move elicited fierce pushback from conservatives and sparked a vote on a Congressional subpoena of Twitter CEO Jack Dorsey.
“The Biden campaign says the meeting never happened, it wasn’t on the schedules, they say,” Baier noted. “And the email itself says ‘set up’ for a meeting” instead of discussing an actual meeting.
Baier then played an audio clip from a SiriusXM radio interview of Giuliani, where he appeared to alter the original details of who dropped off the laptop from which the emails in question were purportedly obtained. The computer store owner who gave a copy of the laptop’s hard drive to Giuliani was also heard explaining how he is legally blind and couldn’t for certain identify just who delivered the computer to him.
” Let’s say, just not sugarcoat it. The whole thing is sketchy,” Baier acknowledged. “You couldn’t write this script in 19 days from an election, but we are digging into where this computer is and the emails and the authenticity of it.”
Featured image courtesy of Thomas Fine.
*As I have noted in the past, Dimitrelos prohibited me from republishing his reports unless I indemnify him for the privacy violations involved. I have chosen instead — and am still attempting — to get permission from Hunter Biden’s representatives to reproduce redacted parts of this report that strongly back Hunter’s claim of being hacked.




Hopefully some of the scowflaws involved in stealing and manipulating personal data for political points will face some jail time here.
The bulk of this post is tied to various civil suits/countersuits, not the criminal case in-chief being pursued by Special Counsel Weiss. No one is going to jail because of these suits, but it sure looks like some folks who came after Hunter are in danger of losing a lot of money.
Lol, nobody is going to jail on the criminal charges either, whether gun or tax. This is a ludicrous overblown turd pile.
Yeah, no one is going to jail directly over civil suits per se, that’s true enough. It does appear though that could well have been breaches of privacy and digital data laws, things like illegally obtaining access to passwords and accounts, etc, that may well be criminally prosecutable.
Do we know whether the gummint is investigating these apparent criminal offenses? (Sorry, if I’ m being obtuse, but it ain’t easy keeping all the events orderly.) Would we know if there is a criminal investigation open?
No
The suit against Ziegler was assigned to a brand new Judge in CD Cal., Judge Vera. The suit against Rudy G., also in CD Cal., was low numbered to Judge Vera from Judge Blumenfeld. Blumenfeld was a late Trump appointee. He clerked for now-deceased 9th Circuit Cynthia Holcomb Hall, a trail-blazer for women attorneys (first woman to clerk for a 9th Circuit Judge – Judge Chambers), but nevertheless a pro-government, pro-business toadie who I had the misfortune to appear in front of several times. A couple of raters at the The Robing Room say Blumenfeld is similar to Hall in judicial attitude, but I have no experience with him. I suspect that HB got a break with both cases going to Vera, whose background as a private practitioner working at good firms, working for Public Counsel, and then as a Superior Court Judge leads me to believe that he will be a straight-shooter type of judge.
Pretty much all federal judges at the District level are “pro-government, pro-business toadies”.
“Pretty much all” goes too far in my experience. I would go with “a majority” or “a sizeable percentage.” Also, the level “toadie -ism” can vary. Cynthia Hall was in a rarified league in that she almost always voted for the government while on the 9th Circuit, regardless of the merits. Even if she ruled against the government, she did it in a way that displayed her distaste for doing so.
I’ll stick with my description; it is a hell of a lot more than a majority.
Cannon being an obvious outlier in the pro-govt column, at least when the DOJ is in Dem hands, Lol.
I very much doubt that is true in the least as to her history before taking the bench and record as a judge once she did.
Cynthia Holcolm Hall is known for being the first female law clerk for the Ninth Circuit. But she also bears the unusual distinction of being the only U.S. Tax Court Judge to serve on one of the Circuit Courts of Appeal. (She did a stint as a district court judge prior to being elevated to the Circuit.)
While she was on the Tax Court, she lived primarily in Los Angeles. Chief Judge Tannenwald, a Tax Court institutionalist, attempted to make Judge Hall move to Washington, DC, where all of the other Tax Court judges lived and worked. Judge Hall refused, pointing out that her appointment did not require her to live in DC, and stating that she would attend all scheduled conferences in DC on her own dime.
They made Rudy related to get it before Vera.
Understood. Sorry I used the legal slang for doing this (“low-numbered”)-
NP. Just wanted to make sure that those not following docket understood that HB’s team took steps to make this happen.
I think keeping these and any other lawsuits together will be useful and important to the whole, not just for judicial economy.
[,] but potentially to the expense of judicial sanity.
Following this narrative, it would appear to me that Weiss will have a devil of a time tying H. Biden to the laptop, as compromised as it is with the already known finagling which would appear to be an absolutely necessary piece to tie H. Biden to the crimes for which he’s being charged WRT the IRS piece.
Abbe Lowell must be licking his chops preparing motions to dismiss the case and pieces of evidence, as well as the cross examinations of witnesses and evidence that does survive pretrial motions. Are Shapley and J. Ziegler on the government witness list? Will G. Ziegler join them as a hostile witness called by Lowell?
As for those three, it will be doubtful they’ll be fully prosecuted for the lying but there is a case there. Recall that in general incompetence in government work is not pursued criminally but criminality is. In Shapley’s case it’s lying to the investigators (what got Martha Stewart sent to Club Fed) but he may be able to skate as an ‘investigator’. G. Ziegler and perhaps J. Ziegler also tampered with the ‘laptop’ files which is absolutely criminal and not anything related to their government duties. I for one will enjoy seeing that smarmy twit Garrett going to jail.
Does Weiss actually need the laptop to bring tax charges?
He doesn’t to bring the gun charges he already brought, but may not be able to keep it out.
He might not need the laptop on tax charges–which may be why he focused on tax charges in the first place. But as I keep saying, the Shapley tour makes these things relevant going forward.
The more evidence there is of mishandling “the laptop,” the more it plays into claims that Hunter could make about selective prosecution.
“These folks were on a mission to get me, to get my dad, and the way they handled “the laptop” is just the tip of the iceberg. . . .”
“Selective prosecution”! Hahahahaha. Sure Jan. That doesn’t work for any defendant, and it won’t for Hunter, irrespective of the absurd laptop nonsense.
“Other than that, how did you enjoy the play, Mrs. Lincoln?”
Keep on singing, counselor.
Yes, for damn near every defendant, “selective prosecution” is a non-starter. But in this case, Trump, Barr, and other MAGA-adjacent DOJers have made no secret of their desire to use Hunter to go after “the Biden Crime Family.”
Not likely anywhere near enough.
I think the ‘laptop’ is the exception that proves the rule on selective prosecution, especially with very similar cases settled at a far lower cost and there is also the problem of the plea deal.
I think Lowell does have the skills to make it stick that the only reason Weiss is doing what he is doing was the political RWNM pressure.
99% of the time, bmaz is right about the defense strategy but this case has some exceptional elements that point to very selective prosecution indeed and I have no doubt Abbe Lowell to push that theory.
Yeah, this case is not that hyper special in the least. And the stupid ass laptop people keep fixating on because that is where the nutters pointed you is likely irrelevant to either the gun or tax allegations. Not that the thing would likely ever be admissible even if it was relevant. They will never make a proper chain of custody/foundation on it. You can’t button this up and solve it on the internet. And your bit that Abbe has the skills to show Weiss was being run by the RWNJs is similarly amusing. Why do you think that would see the light of day at a trial as opposed to being errata as to a file motion to dismiss for selective prosecution? By the way, what does the “laptop” prove as to selective prosecution? People are going insane on this nonsense.
Not an attorney, but I don’t think a “selective prosecution” defense is going anyplace, with the exception that when you add selective prosecution to everything else, forensic errors, obviously biased investigators, possible Russian disinformation, etc., maybe it’s the straw that breaks the prosecution’s back.
For the umpteenth time, how is that going to occur? You going to put Trump on the stand? That would be madness. How are you going to get all the related evidence in? Trump always threatens he will testify. But he won’t, because he can’t. The defense has to do one hell of a lot more than just blithely blurt out “selective prosecution!” in addition to their standard defenses. What it would/will take is light years beyond what is being bandied about here.
Perhaps I didn’t make it clear above, but I’m not expecting the ‘selective prosecution’ to be a major element in the case. I think there are better, more obvious problems with Weiss’s case and Lowell is on top of those. They’ll be the ‘steak and veggies’ of the case Lowell will serve up.
I think the ‘selective prosecution’ issue will be more like spice or sauce; the mixture of salt and herbs atop the steak Lowell will be serving. It won’t be a major element in the case so much as a side order of ‘fuck you, we know exactly why you’re doing this, Republican shithole.’ Something to make the jury (if the case gets that far) enjoy voting for the defense.
Seems to me Lowell would push “selective prosecution” for the same reason as Trump’s lawyers – to score political/pr points outside of court, not to win the argument.
The key detail any selective prosecution claim would be based on is with the witness whom David Weiss reportedly told that no one else in the US would be charged with these charges, as reported by NYT. If Lowell can get there, it (plus the prosecution #s on this gun charge) would be the one thing that would matter–proof that even the prosecutor knows AND HAS ACKNOWLEDGED he is selectively prosecuting Hunter.
That said, the pre-existing plea deals will be easier to get to.
Data fresh as grass… “So I fixed up the basement
With what I was a-workin’ with
Stocked it full of jelly jars
And heavy equipment
We’re in the basement,
Learning to print
All of it’s hot
All counterfeit”
https://youtu.be/mBRr_TqLDf4
From the Riggleman blockquote:
From the legal filing that follows, I think the words above may be a direct quote from someone on Hunter’s team. And when they use the word “forensic,” they mean it in the most technical sense. They likely made a forensic copy, then did all their testing on the copy so as to preserve the original data they initially received. Similarly, they are likely maintaining their chain of custody, much better than the FBI and others in the DOJ did.
And that, my friends, ought to scare the pants off of not just Costello, but David Weiss.
This whole thing strikes me as the defense version of a “speaking indictment.” Abbe Lowell is giving notice that they have — and are continuing to develop — a brutal takedown of how the DOJ handled purported evidence in their investigation, and how the DOJ ignored obvious problems that grew out of their mishandling.
Every time Hunter’s team uses the phrase “For example,” Weiss should get nervous. When Hunter’s team follows this up with “By way of further example . . .”, Weiss should get very nervous. There’s got to be a voice in Weiss’ head right now that sounds a lot like Harry Callahan.
I suspect that with each filing in these civil cases, the likelihood of Weiss filing criminal charges related to “the laptop” is disappearing rather quickly..
I’m not sure I’d go that far, though I’m not sure anyone has a full sense of whether the lawsuits are meant to serve tactical purpose for the criminal defense (which, temporally, is almost impossible to work out).
Lowell has the renged plea agreements.
He has the constitutional problems with the gun charge.
I don’t doubt DE USAO wants to charge taxes–they pretty much have to, to save face. But I also think the possibility of more, such as some weird FARA charge or the campaign finance charge against Hunter/Kevin Morris might be more difficult to rebut.
No one knows how it’ll come out. There **is** more evidence of selective prosecution here than in 99% of defense attorneys who try it. But that may not be what happens.
The amount of time (and money) spent by a sizable number of people to investigate how Hunter Biden’s life was hacked must be orders of magnitude more than the evil people who performed this hack.
Moreover, even after most of the information is eventually known about what truly happened becomes available, most of the media will have moved on many weeks ago.
As a consequence, the disinformation will be retained by many in society.
Obviously, these kinds of efforts are extremely cost effective for the bad actors.
I am not grouping the blind computer tech, Rudy, Garrett and Costello in this camp, they are just stupid people who decided on their own to insert their tits into the wringer.
Rudy is involved in it up tot he hilt, and it’s all political for him: he’s out to “get” Biden as revenge for 2020.
Surprised Rudy actually needs a hilt. And that he has any appetite for fantasy revenge – altho that may be what’s left of his addled pate.
The claimed business card must exist somewhere — unless it’s been conveniently lost? — and might itself reveal things.
[Welcome to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security. Because your username is far too common (there are many Patricks/Pats in this community) it will be temporarily changed to match the date/time of your first known comment until you have a new compliant username. Thanks. /~Rayne]
I think it might have been a photo of a business card.
Where in the Dimitrelos Report does it discuss that check? I looked through reports 2,3,and Final
Also, I noticed this while checking, which I hadn’t previously:
Questions
1.Why does purchasing EaseUS for a 7 day old MacBook Pro indicate 6 months later at April service the MacBook Pro has been “having issues”?
2.Why are there error files from 2016 on this 2017 model Laptop purchased in 2018? Is that normal?
Digging into the red
Could have been in a folder from a *previous* laptop that was copied onto a new one from the disk. I’ve done that with PCs. (I got this computer in 2018. I have at least once file from 2003.)
Q1: No idea.
Q2: Simple.
When you get a new Mac (as I did a couple of months back) you clone the old one using Time Machine (separate drive). Then you boot up the new one, select “migration” and point the new one at the clone. Voila. Everything on the old one is now on the new one, including very old files (I have files dating back to 2011 on the new machine).
But I’m old school (using external drives, etc.). Most folks would use an iCloud backup and clone the new one from that. Same result.
Interesting.
When you migrated to the new laptop even system log files and error files migrated over? So you have error files from your old Mac on the new Mac?
Also, would migration require physical control of the old laptop? There may be scenarios where the previous laptop may not have been available, such as the previous one may have been stolen, or if this laptop was by hackers from the beginning.
Recovery logs from a third party (?) software would be treated like any other application content and kept unless you excluded them.
I see now, about the Dimitrelos Report. There appear to be 4 sections of the report, oddly the first 1 is labeled Final (with the device numbers), and then the 2nd (with Dr Fone info) and 3rd (deleted files) ones are also available to the public through Washington Examiner articles and Scribd for free.
You have access to the 4th section, which for some reason WaEx doesn’t seem to have made public even in redacted form.
But they did produce a couple of articles during that time frame which did cover this topic. I don’t know if it’s appropriate to post links to those WaEx articles, so I won’t, but they are there for people trying to follow along.
You’re fine posting to articles that WashEx has published. The Sun also did one on the check (though ignored the Ablow angle).
Sorry. It wasn’t the Sun. It was the Daily Mail. It even has a video of the float spa.
https://www.dailymail.co.uk/news/article-10966153/Hunter-Biden-spent-30k-prostitutes-FIVE-MONTHS-documents-reveal.html
Abt Baier, Panetta should have flipped it around and interrogated Baier why he didn’t report on the laptop when he could have broke the story in Spring 2020.
According to Mac Isaac, his uncle Ron pitched the laptop to Baier, Sharyl Attkisson, the White House, and Judicial Watch by late May 2020, with plans to contact Sen Johnson next. Mac Isaac’s dad Steven also pitched to Sen Graham and Rep Jordan to no success.
It sounds like someone who knew the family set them up with that “laptop” (quotation marks because it was the contents that were the point).
Yes, it would be interesting to get them as witnesses under oath. According to Mac Isaac, the dad’s previously unknown friend from CIA Larry Johnson helped him coordinate after the story became public.
And if the “laptop” is not really Hunter’s, and it was connected with the Apple ID back in October 2018, does that mean the account was compromised all the way back then?
Again, this is extraordinary investigative reporting, complete with links to source documents – thank you so much EW! A couple legal questions/comments from a non-attorney (IANAL): First, I used to deal with state escheat laws for a large, multistate bank. These laws deal with how unclaimed property is handled. Most states require a tolling period before any unclaimed property can be appropriated, sold or otherwise disposed of. One year is common but some states have five or seven. In any case, apparently JPMI’s invoices said any property left for over 90 days was his. In most states, language on the invoice does not override state law. Biden’s attorneys, I’m sure, are aware of that. Second, doesn’t any “evidence” obtained by hacking, theft or misappropriation (i.e. stealing someone’s digital identity) get tossed in court under the “fruit of the poisonous tree” doctrine?
If you click through to the countersuit, Hunter’s lawyers argue just that. In Delaware the tolling is a year, and there are specific notice requirements. Plus they note that that same fine print guarantees that JPMI will protect the customer’s data.
RE fruit of the poisonous tree. Where it could figure here is if the REAL laptop shared with the FBI were shown to have been packaged up, and if FBI/IRS used content from the laptop–notably, the same phone they accessed via a found password, in the warrant affidavit for the iCloud backups they obtained in August, before such point as they had checked whether or not the laptop had been packaged up.
I’m not sure if it is even possible that the ‘real’ laptop exists, and FWIW it seems pretty clear from the timelines that any laptop was thoroughly ‘edited’ (ahem) before the FBI was ever notified about it.
TY
I just want to say the breakdown of the different petitions’ claims and responses are fantastic, and it has been needed, thank you.
TY. I think a lot of reporters–myself included–had just gotten to the one claim and moved on. But I agree that it was a useful exercise.
It’s a wild current I’m trying to swim upstream against, though.
The political value of the laptop story rests in how intricately the narrative conflates things known with things inferred. Right from the start the NY Post claimed the laptop had “smoking gun” evidence of something bad the Biden family was doing in business dealings.
The “secret” Burisma thank you email was hyped as proof that Joe Biden lied about never discussing Hunter’s business. It didn’t prove anything of the sort. Plus, telling a fib on the campaign trail is certainly no crime. But that was the first laptop bombshell. Next was the “big guy” comment in the email from Gilliar to Bobulinski. Again, the email proved nothing and nothing at all about it is illegal since the comp package was never formalized and Joe Biden was a private citizen even if James Gilliar thought Joe had some kind of value worth compensating.
They were two nothingburger emails that were falsely hyped by RW media as game-changers. They were mixed in with salacious Hunter Biden dik pix and naked drug pictures which made them politically embarrassing even without authentication.
The “laptop” became a catch all. It contained some clearly real stuff, some very suspect stuff, and some basically innocent stuff that was being falsely presented through Murdoch’s disinformation machinery.
We don’t know if the laptop was purchased by Hunter Biden, or dropped off by him, or what items on the devise were put there by Biden. The right has masterfully conflated the device and the cloud data obtained from it. They have conflated drug/sex stuff with many year’s worth of business and personal emails. It’s gotten to the point that all they have to say is “Hunter’s laptop” and they can sell whatever story they want to sell.
Although it is still valuable to unravel the truth behind the physical laptop, I believe it is even more important to empathize that there have been no emails establishing anything corrupt. The fact that it comes off the same source as the drug and hooker stuff that makes them appear tainted.
Misleading presentation of the emails can itself be Russian disinformation, regardless of how those emails were obtained. Because we know for certain the intended fake Ukraine/China narrative has ties to Moscow.
Please consider the advisory given Bruce earlier as to brevity of comments, especially when so much had already been covered by prior comments and/or the main post itself. – bmaz
Let me amplify that: you spent 369 words to offer your opinion. You gave this community nothing factually new.
Concision is your friend and ours. Find it or risk your overlong comments getting stuck in moderation because they are a form of DDoS-ing the site.
Thank you.
Although, by fiat of typo, you made a very important point.
It is indeed “important to empathize.” It brings out the humanity in all of us.
Thank you for that.
Marcy, this is a great presentation. As a journalist you are careful with how you warrant the evidence you present. The work you do matters a great deal, in more ways than you take credit for, I think, but with the Brett Baier’s on the TV and the tech weirdos owning social media, maybe it doesn’t matter these days as much as it should, not like the old days of Woodward and Bernstein, where Marcy Wheeler would be a household name. That’s how I feel about it anyway.
The “journalism” on this topic can be made to self-iterate, like a kind of propagandistic, neo-fascist maelstrom. In trying to understand the information environment, there is only an individual’s point of view, but I am prone to think “Hunter Biden’s laptop” is working well for them even as Hunter Biden gets his justice in civil court.
Hunter Biden’s laptop is a seedy talisman around which claims and counter-claims can be made to erode the difference between fact and opinion or between truth and fiction where opinion needs no ground except for the symbolism of his reprobate behavior. Maybe that’s how the phenomenology geniuses in the Russian intelligence services think about it. It is too rich that Hunter Biden’s laptop is not one laptop but many, it turns out. It’s like something from Joseph Campbell’s “The Power of Myth”.
So we look to judicial process, civil or criminal, or Congressional hearings to sort this all out, but I am thinking eschatologically, so I am superstitious about the outcomes, so maybe not even a trial will vindicate Hunter Biden, because the important meanings are all symbolic. Does it matter which of Bill Clinton’s scandals were real? I used to read long articles in The NewYorker about it.
As a Hitchcock fan, I consider the laptop a classic MacGuffin.
See how brief you could have been? I knew you had it in you.
With or without egg?
Thanks sooooo much for keeping this alive. AFAIC this is a really big deal: so much of what R’s & rw media have predicated to delegitimize Joe (Biden crime family etc.) is based on a lot of lies you’ve exposed. Of all the stuff you write about, this one’s disinformation effort can (and seems to have been designed for purpose) of massively affecting ’24 election. I’ve not seen much in any other media that examines this meaningfully, much less the process by which whatever was actually Hunter’s data (and what was not) came to live in the public domain.
Sure seems to me getting this out-there in detailed way (eg. the way you do things) would go a long ways towards shifting public perceptions to more closely reflect reality. Most of the bad stuff put out about Joe is built on fallacies born and repeated ad-nauseam arise from this saga. I’d really like to see it all exposed.
There’s still a lot of holes. Off the top of my head…
a) details of the car accident
b) I haven’t seen anything verifying HB’s sig on Isaac’s receipt. Sure would be iteresting if someone not HB “dropped it off” @ Isaac’s shop.
c) extent of Ablow’s involvement, wrt to several different events, and (possibly) who Ablow participated with if he indeed was involved in malfeasance. The “extra” HB laptop left in his office needs dots to connect to.
And thx for Riggleman video (I hadn’t seen it).
For a variety of reasons–not least that JPMI’s claims about what laptops Hunter dropped off are provably wrong, at least wrt the one that he shared with the FBI–I am acutely interested that JPMI did not record the S/Ns on the devices that came in.
Are you suggesting Isaac did some creative machine swapping?
Suffice it to say I find it interesting that he both routinely has gotten the model wrong (and if Thomas Fine shows up, he’ll explain that he also got the hardware wrong) AND ALSO doesn’t have a record of what he accepted.
There are other reasons I find that interesting. But we’ll start there.
Thx.
From Thomas explanation, JPMI stated it was a model w a soldered in hard drive. But the serial shows a model with a removable hard drive. Which would be repairable through swapping out the drive, not the drag and drop where he accidentally opens the files and gets curious at file names. Whole story falls apart.
If somebody soldered in a HD, it was definitely not professionally done. Especially on a MAC.
One of telltale signs it was part of disinformation campaign: a little bit of truth mixed into a smorgasbord of… something else.
I don’t follow.
JPMI claimed that because he couldn’t do solder jobs, in order to save the customer data he was forced to manually drag and drop files.
While in reality, the hard drive could have been simply removed and a backed up in normal, automated fashion. Lol I’m not a technical person, that’s what I have understood.
It’s not followable. :)
There’s very little in the entire timeline, beginning when the 1st HB laptop walked into his shop, and what followed until Rudy began distributing several versions to his various media a** hol*s.
It’s a bit like smorgasbord I mention above: +/- 97% bs, with just a little bit of truth sprinkled on top. A LOT of pure fallacy as well.
I responed to your mentioning Isaac’s saying the HD was soldered in. I commented on it only as a case in point of what I describe above. There is no evidence that I’m aware of establishing who brought that machine in his store, or if it even arrived through the front door, or who knows what.
That MacBook was quite new as I understand. There is no way a HD would be soldered into an almost new MacBook, or even an older one. Unless… it was built by amateurs planning a HB disinformation campaign.
There’s just no certainty about any of that.
Source: https://everymac.com/systems/apple/macbook_pro/macbook-pro-touch-bar-faq/how-to-upgrade-macbook-pro-touch-bar-ssd-storage.html
Touch-Bar Macbook Pros: soldered in hard drive
No Touch-Bar Macbook Pros: removable hard drive
So, someone who purchased a 2016 or 2017 MacBook Pro might assume that all Mac Book Pros have the same hardware structure, but the reality is not exactly.
FWIW, the Hunter’s confirmed owned laptop from Ablow’s had a Touch Bar and thus that one had a soldered drive.
https://www.cbsnews.com/news/hunter-biden-laptop-photo/
I spoke too quickly. Mea Culpa.
Thx.
I read it as soldered, connectorswhich it did not say.
Even if the drive was soldered in place, it would likely have been possible to swap out the connector cable to access it from another device. I’ve Frankensteined desktops this way before. Anyone with experience fixing broken hardware should be able to think of similar solutions.
Interesting.
He claimed that from water damage there was a short that affected the power to the hard drive, which forced the drag and drop scenario. And claimed the FBI agents called him back for guidance on that issue.
Yes yes, I know that Europe and the Middle East are at war, the US Congress is paralyzed, but can you please talk more about some crappy laptop (or its hard drive) that has never been established to actually be Hunter Biden’s? Because THAT is the most important thing in the world!
a) which accident?
b) there is a report funded by John Solomon, that concludes it was indeed Hunter’s signature. Long detailed report written by a retired decorated FBI investigator. But… It’s still funded by John Solomon
c) a very curious thread, with many, many layers to be worn. Coincidentally enough, he had his own laptop loss problem at the exact same time frame, trying to get it back from a plaintiff.
Lol, a “decorated FBI investigator”. Uh huh.
A report funded by John Solomon? LOL. Of more value would be which patron funded Solomon to do that.
Lol.
Who knows. Maybe Firtash via Victoria Toensing and Joe diGenova.
https://www.nbcnews.com/politics/politics-news/who-dmytro-firtash-man-linked-1-million-loan-giuliani-ally-n1121561
I didn’t read it in detail, just scrolled through. I haven’t seen anyone on either side go through it in detail.
But, I put it’s existence in my notes/timeline to get a sense of who wants what message to get out and when.
“Most of the bad stuff put out about Joe is built on fallacies born and repeated ad-nauseam”
Substitute the word Hillary for Joe in the above statement. It’s 2016 deja vu all over again, and it’s more organized, widespread, and effective.
Thank you for yet another wonderfully enlightening post. Oddly, even though what is said here, including so much from stalwarts, is factually more distressing than anything one reads elsewhere, I find it calming to come here. Simply because there is something calming, for some of us, about knowing what’s actually going on.
Am sending along another pittance, along with gratitude that there is at least one spot where the internet works the way we all knew it could work, if only it wanted to.