The Laptop Everyone Knows as Hunter Biden’s Appears to Have Been Deleted Starting February 15, 2019
I’ve been wading through Hunter Biden data all weekend. There’s some evidence that the descriptions of the “Hunter Biden” “laptop” based on the drive Rudy Giuliani has peddled do not match the description of what should be on such devices given what the FBI and IRS saw.
Before I explain that, though, I want to talk about how the life of Hunter Biden’s iCloud account differs from what is portrayed in this analysis paid for by Washington Examiner.
As that report describes, Hunter Biden activated a MacBook Pro on October 21, 2018, then set it up with Hunter’s iCloud on October 22. Hunter then used the MacBook as his primary device until March 17, 2019, a month before it waltzed into John Paul Mac Isaac’s computer repair shop to start a second act as the biggest political hit job ever.
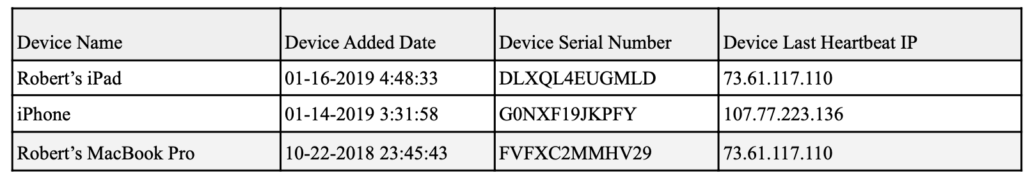
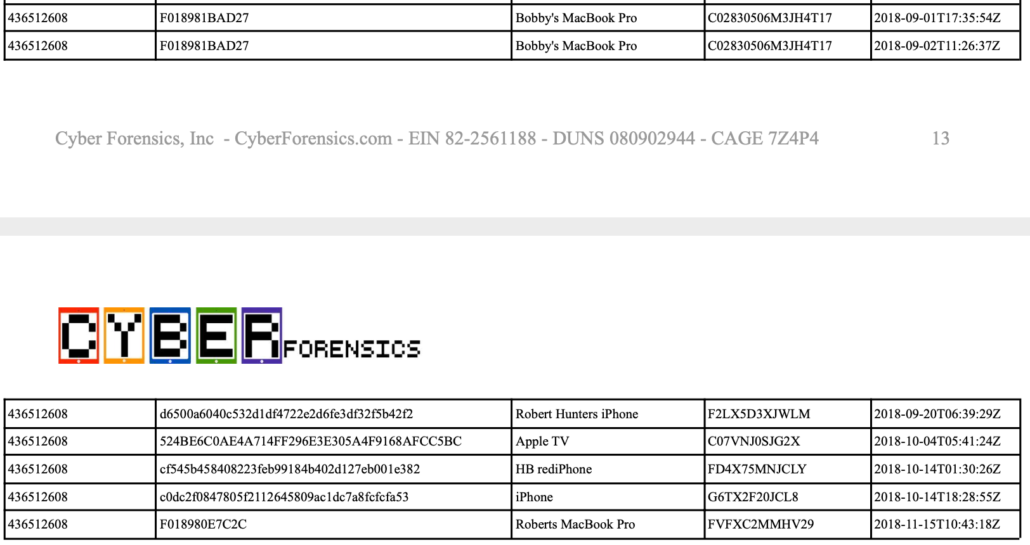
There are problems with that story. A longer table of the devices that logged into Hunter Biden’s iCloud includes devices that appear to have been accessing core Hunter Biden content.
That same table doesn’t show any access after November 15, 2018, with the last access being the device Roberts MacBook Pro that would end up in a Delaware repair shop, but showing up six days earlier than it should. There’s a phone that should but does not show up in those devices, too.
The report doesn’t discuss the import of the shifts between these emails.
RHB used several emails for business and personal use including:
○ [email protected] [sic]
○ [email protected] ([email protected])
○ [email protected]
○ [email protected]
○ [email protected]
One email missing from this list is a Gmail account under which a bunch of passwords were stored. That’ll become important later.
The most important email is the Gmail account (misspelled above), [email protected], which Hunter Biden used to contact sex workers, probably including the Russian escort service that the IRS used to predicate the IRS investigation. That email account got added to his iCloud account at the same time as his iCloud contents were requested, and then again before the MacBook stopped being used. Those changes often happened in conjunction with changes to the phone number.
For now, though, I just want to map out the major events with Hunter’s iCloud accounts from September 1, 2018 (perhaps the months before the IRS would open an investigation into him because he was frequenting a Russian escort service) until the final email as found on the laptop itself. There’s a bunch more — one after another credit card gets rejected, and he keeps moving his Wells Fargo card over to pay for his Apple account; the iCloud account shows Hunter reauthorizing use of biometrics to get into his Wells Fargo account in this period.
In January 2019, the Gmail account Hunter Biden used to contact sex workers (probably including the Russian escort service he had been using) effectively took over his iCloud account and asked for a complete copy of his iCloud account. Then, the next month, all the data on the Hunter Biden laptop was deleted.
Update: I’ve taken the reference to the HB RediPhone out altogether–it’s clear that’s a branded iPhone–and replaced it with a better explanation of the other devices.
Update: I see that he does have D[r]oidhunter88, but doesn’t discuss the import of it.
Update: I’ve added a few things that happened while Hunter’s account was pwned. Importantly, as part of this process an app called “Hunter” was given full access to his droidhunter88 gmail account. There are also a few emails that seem to be a test process.
Update: Added the missing Gmail account.
Hunter Biden’s iCloud
9/1/18: An account recovery request for your Apple ID ([email protected]) was made from the web near Los Angeles, CA on August 31, 2018 at 9:36:07 PM PDT. The contact phone number provided was [Hunter Biden’s].
9/1/18: The following changes to your Apple ID, [email protected] were made on September 1, 2018 at 10:29:36 AM PDT: Password
9/1/18: Your Apple ID ([email protected]) was used to sign in to iCloud on a MacBook Pro 13″.
Date and Time: September 1, 2018, 10:34 AM PDT
9/1/18: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser.
Date and Time: September 1, 2018, 10:42 AM PDT
9/2/18: Your Apple ID, [email protected], was just used to download Hide2Vault from the Mac App Store on a computer or device that has not previously been used.
9/2/18: Welcome to your new MacBook Pro with Touch Bar.
9/11/18: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser.
9/11/18: The password for your Apple ID ([email protected]) has been successfully reset.
9/11/18: Robert’s iPad is being erased. The erase of Robert’s iPad started at 2:56 PM PDT on August 5, 2018.
This is one of several times in several weeks that Hunter loses his iPhone, but while it’s lost, someone also pings his MacBook.
9/16/18: A sound was played on iPhone. A sound was played on iPhone at 8:25 PM PDT on September 15, 2018. (Repeats 25 times in 5 minutes)
9/16/18: A sound was played on Robert’s MacBook Pro at 8:30 PM PDT on September 15, 2018. (Repeats 2 times)
9/16/18: A sound was played on iPhone at 8:31 PM PDT on September 15, 2018. (Repeats 7 times)
9/16/18: iPhone was found near Santa Monica Mountains National Recreation Area 23287 Palm Canyon Ln Malibu, CA 90265 United States at 11:32 PM PDT.
9/16/18: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser.
9/19/18: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser.
9/20/18: Your Apple ID ([email protected]) was used to sign in to iCloud on an iPhone 8 Plus.
This is the second time he loses his phone. What follows is basically a chase of Hunter Biden’s iPhone across LA. It’s not clear it is ever recovered — but it is over two weeks before a new iPhone logs into his account.
9/27/18: Lost Mode enabled on Robert Hunter’s iPhone. This device was put into Lost Mode at 7:20 PM PDT on September 27, 2018.
9/27/18: Robert Hunter’s iPhone was found near [address redacted] Lynwood, CA 90262 United States at 7:20 PM PDT.
9/27/18: Your Apple ID ([email protected]) was used to sign in to iCloud on an iPhone 8 Plus.
9/27/18: A sound was played on Robert Hunter’s iPhone at 7:20 PM PDT on September 27, 2018.
9/27/18: A sound was played on Robert Hunter’s iPhone at 7:20 PM PDT on September 27, 2018.
9/27/18: Robert Hunter’s iPhone was found near [address redacted] Lynwood, CA 90262 United States at 7:20 PM PDT.
9/28/18: Robert Hunter’s iPhone was found near [different address redacted] Lynwood, CA 90262 United States at 4:24 PM PDT.
9/28/18: Robert Hunter’s iPhone was found near [third address redacted] Lynwood, CA 90262 United States at 5:27 PM PDT.
9/28/18: Robert Hunter’s iPhone was found near [fourth address redacted] Los Angeles, CA 90036 United States at 6:22 PM PDT.
9/28/18: Robert Hunter’s iPhone was found near [fifth address redacted] Los Angeles, CA 90069 United States at 6:38 PM PDT.
10/13/18: Bobby Hernandez to [email protected]: You left your phone. How do I get it to you?
10/14/18: The password for your Apple ID ([email protected]) has been successfully reset.
By date, this login is the HB rediPhone, but Apple recognized it as an iPhone X.
10/14/18: Your Apple ID ([email protected]) was used to sign in to iCloud on an iPhone X. Date and Time: October 14, 2018, 11:24 AM PDT
10/17/18: The password for your Apple ID ([email protected]) has been successfully reset.
10/17/18: The following information for your Apple ID (r•••••@rspdc.com) was updated on October 17, 2018. Trusted Phone Number Added – Phone number ending in 73
10/17/18: New sign-in to your linked account [email protected] Your Google Account was just signed in to from a new Apple iPhone device.
Per the Gus Dimitrelos report, the following activity reflects the creation of a new MacBook account called Robert’s MacBook Pro — the laptop that would end up in Mac Isaac’s shop. But there doesn’t appear to be an alert for a new device like there is the for the iPhone 8 Plus the following day.
10/21/18: Your Apple ID ([email protected]) was used to sign in to iCloud on a MacBook Pro 13″. Date and Time: October 21, 2018, 5:50 AM PDT
10/21/18: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: October 21, 2018, 9:06 AM PDT
10/22/18: The following changes to your Apple ID, [email protected] were made on October 22, 2018 at 7:47:30 PM EDT: Phone number(s)
10/23/18: Your Apple ID, [email protected], was just used to download Quora from the App Store on a computer or device that has not previously been used.
10/23/18: Your Apple ID ([email protected]) was used to sign in to iCloud on an iPhone 8 Plus. Date and Time: October 23, 2018, 4:10 PM PDT
10/23/18: New sign-in to your linked account [email protected] Your Google Account was just signed in to from a new Apple iPhone device.
Several spyware apps get purchased in this period.
10/29/18: Your mSpy credentials to your control panel: Username/Login: [email protected]
11/2/18: Your Apple ID ([email protected]) was used to sign in to iCloud on an iPhone XS.
11/16/18: You recently added [email protected] as a new alternate email address for your Apple ID.
11/21/18: You’ve purchased the following subscription with a 1‑month free trial: Subscription Tile Premium
11/22/18: Your Apple ID, [email protected], was just used to download KAYAK Flights, Hotels & Cars from the iTunes Store on a computer or device that has not previously been used.
12/28/18: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: December 28, 2018, 7:06 AM PST
1/3/19: Keith Ablow (then Hunter’s therapist) says Hunter’s email is screwed up
1/6/19: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: January 6, 2019, 1:51 AM PST
1/12/19: Your Recent Mac Cleanup Pro Order [ADV181229-7742-90963]
1/14/19: The following changes to your Apple ID, [email protected] were made on January 13, 2019 at 10:28:31 PM EST: Phone number(s)
1/14/19: The following changes to your Apple ID, [email protected] were made on January 13, 2019 at 10:31:15 PM EST: Password
1/14/19 The following changes to your Apple ID, [email protected] were made on January 13, 2019 at 10:52:13 PM EST: Billing and/or Shipping Information
1/14/19: The following changes to your Apple ID, [email protected] were made on January 13, 2019 at 10:53:40 PM EST: Phone number(s)
1/14/19: The following changes to your Apple ID, [email protected] were made on January 13, 2019 at 11:12:45 PM EST: Billing Information
1/16/19: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: January 16, 2019, 1:59 PM PST
While Hunter is in Ketamine treatment at Keith Ablow’s, a service called “Hunter” gets access to the droidhunter88 gmail account
1/16/19: Here’s my first tip for you!
1/16/19: Hi Robinson, Hunter now has access to your Google Account [email protected].
Hunter can:
View your email messages and settings
Manage drafts and send emails
Send email on your behalf
A bunch of things happen in this four day period: first, someone accessed droidhunter88 from a new iPhone. Someone changed the phone number for the Hunter Biden iCloud. Then, droidhunter88 was given access to the iCloud account. Then the iCloud account ordered all of Hunter’s iCloud contents. Then the password for the account was reset.
1/17/19: New device signed in to [email protected] Your Google Account was just signed in to from a new Apple iPhone device.
1/17/19: I am here to help you find the emails you need!
Giovanni here from Hunter.
I wanted to quickly check if I can help you getting started with Hunter.
There are plenty of functionalities included with your free plan that will allow you to find, verify and enrich a set of data in bulk: these are all explained in our video guides.
However, if you already have a precise task to perform, reply to this email so I can better assist you!
1/17/19: n (from [email protected])
1/18/19: Long email to tabloid journalist sent under rosemontseneca email (this is sent first to Keith Ablow and then George Mesires, the latter of whom responds); this would have shown how the email account worked
1/19/19: The following information for your Apple ID (r•••••@rspdc.com) was updated on January 19, 2019. Trusted Phone Number Removed – Phone number ending in 13
1/20/19: The following changes to your Apple ID, [email protected] were made on January 20, 2019 at 5:24:54 PM EST: Phone number(s)
1/20/19: The following changes to your Apple ID, [email protected] were made on January 20, 2019 at 5:31:21 PM EST: Apple ID
Email address(es)
1/20/19: The following changes to your Apple ID, [email protected] were made on January 20, 2019 at 5:31:21 PM EST: Apple ID Email address(es)
1/20/19: A request for a copy of the data associated with the Apple ID [email protected] was made on January 20, 2019 at 5:40:26 PM EST
1/21/19: The password for your Apple ID ([email protected]) has been successfully reset.
1/21/19: The following changes to your Apple ID, [email protected] were made on January 21, 2019 at 8:28:05 AM EST: Name — changed from Robert Hunter to Robert Biden
1/21/19: You recently added [email protected] as the notification email address for your Apple ID
1/21/19: The following changes to your Apple ID, [email protected] were made on January 21, 2019 at 8:31:02 AM EST:
Rescue email address
1/22/19: The following information for your Apple ID (r•••••@icloud.com) was updated on January 22, 2019. Trusted Phone Number Removed – Phone number ending in 96
1/22/19: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: January 22, 2019, 4:21 AM PST
1/22/19: The following changes to your Apple ID, [email protected] were made on January 22, 2019 at 10:05:20 AM EST:
Email address(es)
1/22/19: The following changes to your Apple ID, [email protected] were made on January 22, 2019 at 10:05:29 AM EST:
Email address(es)
1/22/19: The following changes to your Apple ID, [email protected] were made on January 22, 2019 at 10:05:34 AM EST:
Email address(es)
1/24/19: You recently added [email protected] as a new alternate email address for your Apple ID.
I think that after ordering all Hunter’s data, the account is reset to what it had been from the start. But Droidhunter88, not [email protected], gets the iCloud backup.
1/24/19: Your contacts have been restored successfully on January 24, 2019, 1:17 PM PST.
1/25/19: The data you requested on January 20, 2019 at 5:40:26 PM EST is ready to download. [Sent to both Droidhunter88 and [email protected]]
1/27/19: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: January 27, 2019, 7:41 AM PST
Several photo editing apps are purchased in this period (and one CAD app).
1/27/19: You’ve purchased the following subscription with a 1‑month free trial: Subscription Polarr Photo Editor Yearly
2/6/19: The following changes to your Apple ID, [email protected] were made on February 5, 2019 at 11:39:09 PM EST: Phone number(s)
2/9/19: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: February 9, 2019, 9:52 AM PST
2/9/19: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: February 9, 2019, 5:08 PM PST
Hunter connected to your Google Account
Hi Robinson,
2/9/19: Hunter now has access to your Google Account [email protected].
2/9/19: test To:[email protected]
2/9/19: jkFrom:”Robinson Hunter” [email protected]:[email protected]
2/9/19: The following information for your Apple ID (r•••••@icloud.com) was updated on February 10, 2019. Trusted Phone Number Added – Phone number ending in 96
2/9/19: You recently added [email protected] as the notification email address for your Apple ID.
2/9/19: You recently added [email protected] as the notification email address for your Apple ID
2/9/19: The following changes to your Apple ID, [email protected] were made on February 9, 2019 at 8:33:57 PM EST: Rescue email address
2/9/19: Your Apple ID ([email protected]) was used to sign in to iCloud on an iPhone 6s. Date and Time: February 9, 2019, 6:11 PM PST
2/10/19: Your Apple ID, [email protected], was just used to download Call recorder for iphone from the iTunes Store on a computer or device that has not previously been used.
2/15/19: Hi Robinson, Did you know? Hunter doesn’t have only one Chrome extension! We recently built a simple email tracker for Gmail.
This is where the data on the MacBook that would end up in Mac Isaac’s shop started getting deleted.
2/15/19: Robert’s MacBook is being erased. The erase of Robert’s MacBook started at 4:18 PM PST on February 15, 2019.
2/15/19: Robert’s MacBook Pro has been locked. This Mac was locked at 8:36 PM PST on February 15, 2019.
2/19/19: Noiseless MacPhun LLC
2/20/19: where the fuck are youi? from DroidHunter88 to dpagano:
this is hunter
i dont have your #
call me please
The droidhunter88 account bought a new iPhone — but, after telling Apple they would recycle the old one, instead kept it. That would effectively be another device associated with Hunter Biden. Given some of the other apps involved, this may have served as a way to get Hunter Biden’s calls (eg, from Mac Isaac). Unlike the new devices that show up in 2018, this one was paid for.
2/21/19: New device signed in to [email protected] Your Google Account was just signed in to from a new Apple iPhone device.
2/21/19: Hi Robinson, Welcome to Google on your new Apple iPhone (tied to droidhunter88)
2/28/19: Your items are ready for pickup.Order Number: W776795632Ordered on: February 28, 2019
2/28/19: Your trade-in has been initiated. Thanks for using Apple GiveBack.
3/1/19: Your Apple ID ([email protected]) was used to sign in to iCloud on an iPhone XR. Date and Time: March 1, 2019, 8:52 AM PST
3/5/19: Recently you reported an issue with Polarr Photo Editor, Polarr Photo Editor Yearly using iTunes Report a Problem
3/7/19: Your Apple ID, [email protected], was just used to download Lovense [sic] Remote from the App Store on a computer or device that has not previously been used.
3/9/19: New sign-in to your linked account [email protected] Your Google Account was just signed in to from a new Apple iPhone device.
3/9/19: Promise Me, Dad: A Year of Hope, Hardship, and Purpose (Unabridged)
3/13/19: Your Apple ID ([email protected]) was used to sign in to iCloud via a web browser. Date and Time: March 13, 2019, 5:43 PM PDT
3/16/19: The following changes to your Apple ID, [email protected] were made on March 16, 2019 at 11:59:16 PM EDT:Email address(es)
Droidhunter88 is added back to Hunter’s iCloud contact again.
3/17/19: You recently added [email protected] as a new alternate email address for your Apple ID.
3/17/19: The following changes to your Apple ID, [email protected] were made on March 17, 2019 at 12:02:06 AM EDT: Email address(es)
3/17/19: We haven’t received your device.



Where are the unspeakable crimes? I was told by a lawyer now about to be disbarred that there were unspeakable crimes
[Welcome back to emptywheel. Please use the same username each time you comment so that community members get to know you. You published this comment as “Mike” which is not acceptable due to its commonality and length; you have published (14) previous comments as “HCCarey,” to which I am reverting your username this one time. Please make a note of your username and use it consistently on future comments. Thanks. /~Rayne]
What are the implications of this?
Apologies for being slow on the draw. I’ll blame chemobrain.
I second that emotion.
[Welcome back to emptywheel. Please use the same username each time you comment so that community members get to know you. You changed your username to “nothin from nothin”; “nuthin from nuthin” is a new and different username which forced your comment into auto-moderation. Please use the name you chose to avoid future moderation. /~Rayne]
Most likely: Some party or parties unknown sought and gained access to Hunter’s iCloud account. After that it gets speculative, but it isn’t much of a reach to suggest involvement of a “dirty tricks” team, quite likely Russian in origin (with possible stateside political connections), perhaps linked to the Russian ‘escort’ service he patronized. Capitalizing on the prurient stuff already there & adding spurious ‘evidence’ of more serious wrongdoing.
It doesn’t have to be Russians. Any third rate hacker could have done this, all they needed was access to Hunter’s iCloud account. It didn’t help that he was likely in a drug induced fog during this time, or he would have seen the notifications that Apple sends to all devices linked to that account with things like when a new device is attempting to link.
Please note: “Quite Likely” is not isomorphic with “has to be.” Sure, could have been a US funded political operative or even some stray criminal hoping to cash in. Though the latter seems improbable, since there’s no sign of anyone getting $$ out of it.
The rediPhone probably refers to a branded device (https://www.apple.com/product-red/) from this Apple partnership. https://www.red.org/partners/apple
Oh!! That makes much more sense.
A little bit more on Red
https://en.wikipedia.org/wiki/Product_Red
I learn so much here, soaking up the information provided by Marcy Wheeler, all of the contributors, and, for lack of better words, the gallery of learned readers who have a thoughtful word or two to add.
Thank you all
(I’m going to say that “HB rediPhone” is just “[Hunter Biden] red iPhone”.)
Yup. I fixed that. I was meaning to emphasize that the report wrongly suggested that Hunter just had a simple set of phones. The reality is there were enough to get things confused.
So, is Hunter making all these changes or are you thinking it’s more nefarious and someone else is?
Hunter is not making those changes. I’m fairly certain Hunter was blinded to them by the change in phone number etc.
The thing is, it would be child’s play to get his iCloud password, especially if he was on a bender. Especially if someone absconded with his phone and fled across LA with it, as happened in September 2018. And so MOST of the web logins–the ones not associated with a “find my phone” operation–are someone else just going into his account.
Reminds me of Ashley Biden’s diary theft. I get the impression of sharks circling, looking for opportunities.
The minions would also be making things up if there was nothing to find. With this kind of chain of access custody no wonder a reasonably honest USA would be loath to bring charges, even before the repair shop fiasco.
How many of the potential charges would rely on knowingness? I’d say any defense attorney would start with the bender issue and dig into the myriad gaps.
Between Hunter and Ashley (which was an outright theft) it’s clear that a pattern of misconduct and potential conspiracy existed then and now. If it’s not punished we’ll see more of it.
Yep.
This whole thing stinks to high heaven. The kind of foul odor that is reminiscent of foreign intelligence services…
Or the GOP. But I repeat myself.
I’m pretty sure the laptop was never supposed to see a courtroom. It’s similar to the pressure campaign on the Ukrainians to announce they were opening an investigation. What Rudy expected was for there to be leaks from the FBI and/or the IRS, when nothing happened they gave it to the NYP (with even more spice added for the election). Basically it was supposed to be a replay of what they did to Hillary in 2016.
Basically it was supposed to be a replay of what they did to Hillary in 2016.
Exactly. BANNON gleefully said as much
in leaked AUDIO from 10/31/20.
I left a partial transcript of that [in moderation for now] at a comment further down the THREAD.
[Cleared auto-mod. Thanks for the heads up! /~Rayne]
Thanks Rayne! :-)
https://www.emptywheel.net/2023/07/08/the-laptop-everyone-knows-as-hunter-bidens-appears-to-have-been-deleted-starting-february-15-2019/#comment-1001545
When you’re hunky dory with seditious conspiracy, what’s a little theft or more garden variety conspiracy?
Thanks Dr. Wheeler. Again and again and again. I do not understand how the thrashings of the Biden children (and their grandchildren–thanks for nothing Maureen Dowd) proceed unabated while the sketchy actions of the former person’s children are basically ignored. Jared got 2 billion for what exactly? All of Vanks’ patents? I am grateful to you for your dogged focus in outing all the BS while keeping us informed. You are a gem.
You’re not the only ones; based on some new polling, it appears even Republican voters are getting fed up with hearing about Hunter Biden. Have a look at the linked poll here: https://www.dailykos.com/stories/2023/7/10/2180320/-House-GOP-s-sham-investigations-target-one-audience-MAGA-cultists
Bit of a bummer there, it appears that Independent’s priorities line up more closely with R’s than with D’s.
Rayne: Have been trying to change to the 8 character user name request but I seem to be always locked out when I go to the login page (and am not sure I ever created an account although I have been around since the old FireDogLake days). Feel free to reply here or to my email addy. And thanks for all you do.
I can vouch for HanTran being around forever, and is a fine voice to have here. Also, good to see you again HanTran.
It’s easier than you think. Just overtype whatever your browser cache has stored in the Name field. :-)
(this sample image shows the name “Wajim” only because he had the same problem and I snapped the image by opening Reply beneath his last comment.)
If it’s so easy for Bad People to steal HB’s Apple ID, then why is it so damn hard for me to convince Apple either to recognize mine or let me reset it?
I haven’t been able to access iCloud (from a PC now) in years. Maybe I just don’t do enough crack.
This app appears to be misspelled; 3/7/19:
“Your Apple ID, [email protected], was just used to download Lovense Remote from the App Store on a computer or device that has not previously been used.”
Should be Lovesense, it’s an app to control a remote sex toy which, I have to say, is pretty fun!
I put a “sic” in there. I copied it right from the Ziegler set of emails. It could be his error tho.
Don’t want to be be contrarian, but I believe that it really is “Lovense”; there is a website by that name, for that very product/service.
Hi. Something that’s always bothered me: the alleged drop off at JPMI is 4/12/19. The last date of data is if I understand correctly 3/18/19 or 3/17/19. Now JPMU has said that he went back & downloaded icloud data, & if that’s the case – presuming HB continued use of mac email & backups etc – that means there should be a later data point, but there isn’t.
If so this would prevent ID’ing where HB, what he was doing 4/12/19.
Also, everything in the data has HB somewhere else than Delaware – DC, L.A., maybe Ukraine, but never DE. That Jan 2019 IP is in Boston for instance.
And I’ll never understand why WashEx or other sites good bad or in between used Scribd, damned impossible to use.
I hope this is helpful, thanks for all the great work.
(fkaTex, hopefully this name works)
Frances Parkinson Keyes would approve, at least :)
https: //www. goodreads. com/en/book/show/128865
For our non-technical readers, when DinnerAtAntoine’s points out “That Jan 2019 IP is in Boston,” they mean the device contacted the network from an internet protocol address which wasn’t in Delaware but a different location. Specifically, the IP addresses point to the ISP and type of address assigned by the ISP from a particular network location:
73 61 117 110 — ISP: Comcast Cable – likely static IP — Boston MA
107 77 223 136 — ISP: AT&T Mobility LLC – likely static IP — Worcester MA
(periods removed in IP addresses above)
An IP address is comparable to a telephone number assigned to a phone; a “likely static IP” is comparable to a phone number assigned to a hardline phone which doesn’t move about like a wireless phone. These addresses could be spoofed — faked — but why would a hacker spoof Massachusetts’ static addresses on two different ISPs?
Hold that thought about the dates, DinnerAtAntoine’s. :-)
p.s. Your new username is fine, just be sure to use it and your email address consistently.
Really helpful, Rayne!
I think I am going to spend ALL DAY
just GLUED to this POST / Updates and Comment Section!
You’d better brace yourself for trollery because Marcy’s work in this post is likely to draw trolls who want to make a lot of noise to prevent the narrative going hard toward facts and away from gaslighting.
*unleashing the popcorn-o-nator*
I’m sure I have no real concept of the levels of trollery, but, you’re doing amazing moderating at the moment, as always, and I wish I could send you ALL some appropriate sustenance right now.
Typo in the blockquote at the top?
I think there is an “R” missing from that email address, making this droidhunter88 @ gmail . com.
[FYI – blank spaces added to the email address to deactivate it. /~Rayne]
Wow! Just wow.
1st timer … long timer (circa fdl).
Mac user but orig windows 1.3 trained so can follow.
The name itself “droid” doesn’t follow others.
Rayne. This is my email but I don’t bother. Hope user name works. I’ve never come out. Doing so now.
[Your username is fine as it’s unique and meets/exceeds minimum 8 letters. Thanks for the heads up and welcome to emptywheel comments. /~Rayne]
For some reason, droid made me imagine HB as a star wars nerd which didn’t quite fit. And 88 (since not his birth year) made me flash to Ziegler as the nazi adjacent online dork he is.
Droid 88 just seemed especially too cute and amused me. I look forward to reading the final report on this whole dumb invented saga.
[Moderator’s note: If you read further in this thread you’ll see I requested another commenter get back on topic rather than go off on an unsourced tangent about number=Nazi. Let’s get back on the topic. /~Rayne]
“HP iPhonered” is actually “HB iPhonered”
I suspect it’s an iPhone X (RED) belonging to Hunter Biden. An Apple device.
Oh never mind you already fixed it.
Can anyone help me out. Has anyone anywhere identified something incriminating from the notorious laptop, other than a portfolio of unflattering pictures of Hunter in his underwear?
The emails touted by the New York Post add up to nothing.
[Welcome back to emptywheel. FOURTH REQUEST: Please use the same username each time you comment so that community members get to know you. You changed your name in your last comment from “David” to “David in NYC” which complies with the site’s standard. You need to ensure you use the same name each time if you wish your comments to clear for publication. Thanks. /~Rayne]
You are spot on. There never was a real smoking gun. It has always been gaslighting that uses inuendo and guilt by association.
Here is the formula that the RW echo chamber has employed successfully: “Hunter Biden” plus “Laptop” equals “Burisma” times (“China” plus “Communist Party”) divided by “Dad”. They have repeated those combined elements so frequently that they can now just use one element to trigger the entire string with their audience.
It is time to mess them up by invalidating a key element. It’s simple, actually. The “laptop” element can be invalidated using one simple logic test: “How can a laptop that was manufactured in 2018 contain emails from 2014?” The answer is obvious, but the average Fox News consumer isn’t that well versed in cloud computing. Even if they were, “Hunter Biden’s iCloud account” doesn’t carry the same impact as “Hunter Biden’s laptop” because cloud storage is viewed as being less secure.
The media should challenge the “Hunter Biden’s laptop” narrative as being misinformation, which it clearly is. More importantly, though, is to challenge the content of what the right attempts to pass off as evidence.
You forgot to add the Eliot Spitzer factor to your equation — tracking a target by their consumption of sex worker product, and then using that to smear the target(s) when the set-up was in place and timing was right.
Feels like the opposite of a catch-and-kill, more like catch-and-spill.
“How can a laptop that was manufactured in 2018 contain emails from 2014?”
As desirable as a simple logic test might be: This isn’t it. I used to transfer my old emails to new computers and notebooks for many years so that I had old correspondences ready. The result was that I had access to emails even from 1998 on a notebook manufactured in 2014. (Now that I’m retired, I started anew and have old emails and documents only on an external harddrive, just in case.)
The point is that you had to add your old emails onto the newer laptop. That means Hunter Biden’s older emails had to be added to the infamous “Hunter Biden’s Laptop”. Which opens up the possibility that someone, other than Hunter Biden, did the adding.
It is no longer just the laptop. It’s about the iCloud data. Anyone who says that the laptop contained evidence of Burisma corruption is engaging in misinformation. The right knows that, which is why they refused to document when the laptop was purchased.
Near certainty the old emails were added from iCloud when Hunter’s Mac first connected to iCloud. That’s just how it works. I don’t think anything sinister in that.
What it looks to me like Marcy has pointed out: someone sinister got access to iCloud in L.A. through one of Hunter’s (stolen ???) iPhones. This is when shenanigans changing notification email account/iPhone happened, so Hunter would not be notified until they changed email notifications back to Hunter.
It was during this time sinister hacker downloaded from iCloud and made some changes. From what I’ve read last couple days, not enough data/investigation to know exactly what was done, other then addition of 4 email folders. I haven’t seen anything yet (could have missed it) that explains those 4 new folders.
Then the Macbook hd was wiped clean. Seems likely this is when the doctored iCloud download was installed on the Macbook. This explains somewhat how a lot of the email file meta data was bulloxed: whoever edited that iCloud data appears to have not been really good at it. Left clues.
Not misinformation. Disinformation.
And somebody had to be following Hunter Biden, knowing when to take advantage of him to do very specific damage.
And so now we’re on to the meta scandal, the truncated investigation, brought to us by the “whistleblowers.” It will never end.
The way I heard it from Hal Sparks (I don’t know his sources offhand but he sounds pretty confident) was that the KGB/GRU in Ukraine hacked Hunter’s ICloud and downloaded all the contents.
Then they mixed in loads of fake dirt with the real ICloud data, made a new laptop hard-drive image of the combined fake and real data, and then sold the (fake) laptop hard-drive to Guiliani for $3 million.
“[Someone] says” is not evidence, it’s speculation. Sparks’ theory may satisfy the itch for an answer but more is needed to make a case which proceeds to court.
Please do better than promote a celebrity pundit here, even if they’re left of center.
Who may I ask, is Hal Sparks??
Wow! This is amazing forensic work – thank you! It hadn’t occurred to me that the original laptop(s) that were dropped off at Mr. Magoo’s repair shop could be “tracked” in a meta sense by their connection to iCloud. Brilliant. I will be very interested in what conclusions can be drawn from this data and how it refutes the false right-wing narratives around Hunter and Joe Biden.
Yes! I am just in total AWE of Marcy!
Excellent sleuthing.
On 10/31/20, BANNON cackles about what he’s been up to, using the same play book as 2016:
Source:
Here’s the Whole Transcript of That Leaked Steve Bannon Tape, Annotated Disclosing Trump’s plans to falsely claim victory was just the start. [10/31/20] https://www.motherjones.com/politics/2022/08/full-transcript-of-leaked-steve-bannon-tape-donald-trump-2020-election/ [] DAN FRIEDMAN AND ABIGAIL WEINBERG AUGUST 17, 2022 []
I feel a need to look back at the above transcript and related articles, and this:
Trump Had One Last Story to Sell. The Wall Street Journal Wouldn’t Buy It. Inside the White House’s secret, last-ditch effort to change the narrative, and the election — and the return of the media gatekeepers. // Ben Smith 10/25/20
Web Archive link: https://web.archive.org/web/20230206184409/https://www.nytimes.com/2020/10/25/business/media/hunter-biden-wall-street-journal-trump.html
added: Here’s another:
How a fake persona laid the groundwork for a Hunter Biden conspiracy deluge
A 64-page document that was later disseminated by close associates of President Donald Trump appears to be the work of a fake “intelligence firm.” https://www.nbcnews.com/tech/security/how-fake-persona-laid-groundwork-hunter-biden-conspiracy-deluge-n1245387
Ben Collins and Brandy Zadrozny Oct. 29, 2020 Updated Oct. 30, 2020
“ Eric HERSCHMAN [friend of > KUSHNER]”
Ah Kushner and Herschmann.
I’m still baffles by why Lowell is representing both HB and Kushner.
It perplexes me that a trump world figure has competent representation. Who is also representing a Biden.
I understand plenty of lawyers can be equal opportunity and represent seemingly vastly different people. But I’m still weary.
We’re all weary, and most of us are wary.
Lol. I’ve been so tired of this since 2015, my mind blanked out on spelling.
Thanks for the reminder.
Now I’ll always associthe correct version with “ Knowatall”!
Thanks for putting this together, really amazing.
Would it be a good idea to add 1 more month of data to this analysis? Hunter is in Vegas from 8/2 to 8/20. He tells a prostitute in January that in August he almost drowned in a pool on top of a hotel while using drugs, then as he was waking up, a Russian drug dealer stole his laptop. There might be interest activity during this time related to his account activity.
[Welcome back to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security. Thanks. /~Rayne]
Do you have a link to a reported article which supports this?
The video here seems to be the source of the claim: https://web.archive.org/web/20210811185118/https://www.dailymail.co.uk/news/article-9881213/Unearthed-video-shows-naked-Hunter-Biden-claiming-Russian-drug-dealers-stole-laptop.html
Thank you — but let’s encourage other community members, especially new ones like the username “z-score,” to provide supporting documentation when they comment.
This exchange could have been reduced to one comment if a supporting link had been provided in z-score’s comment.
And it’s from a UK tabloid, so it’s like citing NY Post.
I can’t finish my cuppa until I’ve read the Daily Mail. The most credible source of news in the UK after page three of the Sun. :-)
According to its wikipedia entry, it was banned as a source in 2017, owing to its history of unreliability, sensationalism, plagiarism, and copyright infringement.
As Rayne says, citing sources allows readers here to gauge the credibility of the evidence for a comment. This source isn’t credible at all.
The general unreliability of the Daily Mail strikes me as irrelevant in this case. Either the video is real, or it isn’t. If you have evidence that it was faked, it would be helpful for you to present it.
In this case, citing the DailyMail should include a caveat that DM has been unreliable and the content needs second or third source of corroboration.
It’s not that DM is always bad, but DM has been inconsistently reliable in the past. It should not be a regular sole source.
p.s. My bad for not pointing this out when you offered the archived link.
Apologies, my intent was to be helpful. From now on, I’ll refrain from looking up and posting such an article when you ask someone else for one. I also have little experience with the Daily Mail, so didn’t think to include a caveat, but can certainly include one when I don’t know if a source is reliable.
I’d simply tried to identify the original source of the claim, and that turned out to be a DM article that includes a video, purportedly of HB telling a sex worker in January of 2019 that Russian drug dealers had stolen one of his laptops the year before. Either the video is real or it isn’t. That the DM was the first to report on it strikes me as irrelevant, unless there’s a history of the DM either faking videos itself or sharing videos faked by others.
Given the video’s contents, my guess (which is only that) is that it’s real.
Thanks, understood.
It’s also important to keep in mind with some of the UK media outlets that they were and remain responsible for Brexit, a destabilization operation intended to undermine NATO and screw with a nuclear power. DailyMail was one of those outlets. While its editorial leadership has changed since then, it dug a very deep hole for itself from which it has struggled to climb out. It doesn’t help that it continues to rely on tabloid-type reporting.
Actually, the burden of proof about reliability is on the other foot. A more credible source would help that.
I’m not criticizing you for finding a probable source for someone’s else’s comment. I’m criticizing the DM. It’s general unreliability is relevant when assessing any material it publishes.
According to the Mail that was August 2018, presumably why he activated a new laptop in October. However Hunter doesn’t blame Russians in the Mail’s transcript, nor does the quoted text in the title ‘The Russians have videos of me doing crazy f***ing sex!’ appear, so where that came from is a mystery.
The transcript is more complete than the video though there are gaps in both transcript and subtitles because the audio is unclear (eg. at 1:55). I tried shouting “enhance” at my phone but nothing happened.
Still, the dealer and his two guys from whatever motives, took Hunter to Vegas, showed him a not very good time at his own expense, roofied him and stole his laptop.
“I think he’s the one that stole my computer. I think the three of them, the three guys that were like a little group. The dealer and his two guys, I took them everywhere.”
“My computer, I had taken tons of like, just left like that cam on. And he would always put in a passcode and all that, you know what I mean? It was f***ing crazy sh**. And somebody stole it during that period of time. He did all this kind of like pretend search and sh**.”
I don’t understand why “he” should put a passcode on my computer. Aren’t passcodes for phones?
[Forgive me for not following etiquette. Is there a community guidelines I should read? I attempted to make a login, but I somehow messed up]
That DM article looks like it has the same information, yes. My notes cite 8/2 to 8/20 in Vegas from “Laptop from Hell”. And the claim of the Hunter’s laptop being stolen from the Marco Polo Report p 309-310. It transcribes his own words that he spoke to a prostitute on 1/6/19 in a video recorded on one of his devices.
I don’t plan on viewing any of the videos, lol, so trust that they accurately quote Hunter’s own words. Is there reason to believe they did not transcribe quotes accurately?
As far as the reliability of these sources, is there a reason to believe the videos were faked? I view these sources with huge skepticism in how they analyze and what they choose to put in vs leave out, but am willing to use them to establish a timeline of events. .. and a laptop stolen in August 2018 I think is relevant to the type of analysis in this article from emptywheel about acount and device activity. Is it not?
[Thanks for updating your username to meet the 8 letter minimum. /~Rayne]
Thirdhand: anecdata.
~golf clap~
What do you mean by that?
[Moderator’s note: She meant it’s anecdotal data unless there’s supporting documentation. Let’s not chase this further and focus on the topic of the post. ADDER: Comment Policy link is in footer – disregard the information referring to registration as you need only enter Name/Email/URL-where-applicable in fields indicated before posting. For other comment guidelines see this link. /~Rayne]
Thanks
Is my comment relevant to the article? There was a laptop left by Hunter at Ablow’s office sometime in Feb 2019 (reported by NBC News on 10/30/20), and discussed in Lucifer’s Banker Uncensored published 9/30/20. NBC reported that Hunter’s laptop was picked up by DEA when they raided Ablow, which was 2/13/20. NY Mag reported on 9/12/22 that the DEA returned it to Ablow’s lawyers who contacted Hunter’s lawyers.
Hunter’s team led by Kevin Morris have floated the idea that this laptop was somehow given to Mac Isaac or that Mac Isaac was used as cover for real story.
I have been trying to narrow down exactly when Hunter was w Ablow in MA, and exactly what date Hunter would have left behind his laptop (and allegedly also a diary and notes). And when he received the Ablow laptop back. I also noticed the “last heartbeat” IP addresses connecting to somewhere in MA that you mentioned somewhere in these comments.
In Beautiful Things, Hunter writes he was w Ablow for abt 6 weeks for ketamine infusions , then returned to Maryland, then back to Ablow for abt 2 weeks.
I found this Hunter account analysis by emptywheel extremely relevant and useful.
Don’t be afraid to cut and paste links to articles which support your comment. The links may cause your comment may go into moderation but it will eventually publish provided the links are to well-known and reputable news media outlets.
For those who are interested in the Hunter laptop chain of custody and the 2nd laptop at Keith Ablow’s office
Ablow’s office in Newburyport, MA raided 2/13/20 by DEA
https://www.nbcboston.com/news/local/feds-raid-office-of-former-celebrity-psychiatrist-keith-ablow/2076481/
NBC reports on 10/30/20
Hunter’s laptop picked up in DEA raid in Feb 2020
https://www.nbcnews.com/politics/2020-election/here-s-what-happened-when-nbc-news-tried-report-alleged-n1245533
NY Mag reports 9/12/22
the Ablow laptop was returned by DEA to Ablow’s lawyers who then contacted Hunter’s lawyers, discusses Hunter’s research team [doesn’t mention Kevin Morris by name, but he is likely the leader. We also now know Denver Riggleman joined Hunter’s team sometime last year. Not clear when, if Denver was involved at the time of this article]
https://nymag.com/intelligencer/article/hunter-biden-laptop-investigation.html
Miranda Devine reports at NY Post 5/29/22
Hunter left laptop w Ablow Feb 1, 2019. Miranda cites Hunter’s friend/research team lead Kevin Morris for the Feb 1 date. Has Kevin’s hand drawn mind-map/timeline which does not have verified accuracy
[Miranda should know the exact date or have a better estimate by way of her research, and interesting she doesn’t correct or offer a better date, making it seem as if 2/1/19 is the official date Hunter left the device w Ablow. Miranda also claims in this the Mac Isaac chain of custody “well established”. And notable that in her book she claimed she was involved with the original 10/14/20 reporting, but the reader is left to wonder why her name was not in that byline]
https://nypost.com/2022/05/29/new-bid-to-spin-hunters-laptop/
Lucifer’s Banker Uncensored Author book event 10/22/20
Reported by Daily Beast on 10/25/20. Says Ablow told him in Oct 2019 about the laptop, notes & journal left behind by Hunter. He then told Sen Grassley on 2/11/20. Says Hunter stayed w Ablow 3 months in Summer 2018. Notable as this is false date for when Hunter would have been w Ablow. Who is lying? Ablow or the author Brad Birkenfeld? Also in article, Giuliani associate claims Giuliani drove down to DE to get 3 devices from Mac Isaac, we know that is false but interesting a Giuliani associate either believes that or put it out there
https://www.thedailybeast.com/rudy-giulianis-crew-of-misfits-and-hucksters-storms-into-the-hunter-biden-wars
Lucifer’s Banker Uncensored published 9/30/20
Author makes similar claim as at the book event 3 weeks later (previous paragraph). Notable that this is before the NY Post publishes the Mac Isaac story on 10/14/20.
Thanks. That’s really helpful.
The February 2019 date is really important as that was just after tons of changes on Hunter’s iCloud account and a phone.
Whether or not the laptop allegations are objectively true is irrelevant, the purpose is not to establish fact but to enrage the foot soldiers. UraniumOne, Obama’s birth certificate, Vince Foster, Seth Rich, stolen election, swift boat, vaccines cause autism, Covid-19 death overcount, 6000 year old Earth, climate change denial, Pizzagate, chemtrails, etc. The process repeats itself because it has shown itself to be successful in gather votes and contributions.
…Clinton, White Water, Vince Foster yadayadayadayada …
It’s the SAME drivers, beginning with RATFUCKER Stone, and his mentor Cohn.
Laptop, Bengazi, Kabul. server, and now woke, doesn’t matter which words lead or follow, these words alone are enough to send a fair % of US adults into a Two Minutes Hate frenzy, just sub in Biden, Clinton or Obama for Goldstein.
We didn’t start the fire…
https://youtu.be/eFTLKWw542g
Don’t forget Rev Jeremiah Wright, Tony Rezko, Frank Marshall Davis, and Bill Ayers.
To think how much fuss Republicans made of Obama “paling around with terrorists” compared to Trump’s embrace of the Proud Boys and the Jan 6th defendants.
Purely anecdotal evidence- but when I clean my caches on my MacBook and iPhone and sign into gmail/iCloud etc I get the message “signed in to from a new Apple. . . device”. Because I am crazy I do this multiple times per month. So to add confusion from the clarity of the post it may be that someone is merely cleaning the caches which may suggest someone trying to keep the devices free from tracking (ad tracking) .
[Moderator’s note: Please confirm you’ve changed your email. Please also refrain from adding any content to the URL field as you have not previously entered any data in that field for your previous (3) comments to date. /~Rayne]
Clever point. But your “crazy” probably doesn’t resemble that of a drug-addled man who keeps losing his devices. Sure, a stimulant abuser might be paranoid enough to empty caches regularly, but if so, would probably also be paranoid enough to get rid of compromising pictures, emails, etc., and/or use only encrypted messaging systems. Hunter doesn’t seem to have done anything like any of that. Marcy’s argument: that someone else was breaking into the account(s) and messing around – stands.
So Droidhunter88?
88 is Neo-nazi code for ” Heil Hitler”.
Yeah? There are 88 keys on a standard full-size piano keyboard – the kind his grandfather played. His dad’s first run for POTUS was in ’88. His dad almost died in ’88 of a brain aneurysm.
Don’t post shit like that without something to support it.
ADDER: You have (2) approved comments so far under username “SB317overthere.” Perhaps you’re still new to this place. We expect a better caliber of comments here. Take a seat in the back and just read if you can’t level up your game.
ADDER-2 12:38 PM ET: This ends here. You’re going into auto-moderation until you stop DDoS-ing this thread with this crap.
Attn: PJ Evans — your reply to SB317overthere has disappeared because it’s attached to a comment which has been binned. Please don’t reply to this character in this thread if another comment appears because they are DDOS-ing the thread with their evidence-free material.
Nothing. Because if there’s more than one of a name, the rest get numbers.
No problem!
Another example of Rayne keeping the site cleaned up. Thank you, Rayne; I’m sure there’s something you would rather be doing on a summer Sunday than dealing with trolls like this. Much appreciated.
Just don’t troll during my cocktail hour or I will have a nuclear meltdown and open a can of whoop-ass. LOL
Just how long is your cocktail hour these days? :-)
BTW, nice thread over at Mastodon about Threads.
By all accounts, Hunter was going on 3 day crack binges. He’d come off for a few days, a week, and start rolling again.
99.9 percent of the people in this world have no idea a what that does to your mind and your body. It’s like having a jet rocket hooked up to your system (according to a friend) and then going into 72 hours of liftoff.
Coming down is the lowest, dirtiest feeling in the world. Again, according to friends who have now cleaned up, what you do over those 3 days is completely out of your control.
Finding passwords, setting up hook ups, getting more drugs, is the struggle of a lifetime.
It’s a really bad place to be. Really bad. And from what I’ve read and heard from friends in Wilmington, he was at the top of the abuse chain. He destroyed everything along the way. Most addicts do.
I commend him for getting sober. I understand his struggle. Just hope he stays clean. Because where he came from is living hell. From instant euphoria to the gutter.
I cringe just thinking about it. The pressure and stress from the media isn’t helping him.
Thank you. That was a very thoughtful and helpful post. Not everyone here has had to deal with the problems of addiction. Most are sympathetic, though.
I appreciate the dilgence in research, reporting and managing comments.
This site is always worth a read, and a think, and a ponder.
I suspect a few proverbial nooses are tightening.
Exciting times.
May the rule of law prevail.
The app named “Hunter” appears to be this one: https://hunter.io/
If you go their website “About” page, you will find that the “Head of customer success” is named Giovanni. The company appears to be legitimate, at least at first glance. Five minutes of poking around their website leads me to believe that like a lot of legit tools, their tools might also be useful to folks with nefarious intentions.
Yep. Lots of that here.
For example, why does Hunter need two spyware tools on top of his habit of hunting for his own phone all the time, if that’s what he did?
Well, because those provide more information without notice back to the Apple site.
Marcy, from just before 10/21/18 in the above post:
Marcy, an hour ago, on Mastodon:
https://mastodon.social/@emptywheel/110686294490639396
Jul 09, 2023, 17:40 [I still don’t know what TZ this is]
Curiouser and curiouser. It’s as if the Examiner’s “forensics expert” is no expert at all. Perhaps he used to work for the Daily Mail, but couldn’t make the grade.
This is the “report” Marcy said a couple days ago was problematic. Her last couple articles here since have exposed some of why that is true.
The most important possibility for any of these reports (at least 2 more I know of: CBS and NBC) it to prove/disprove tampering. I read this one (Wa. Ex), CBS and part of NBC. They all differ in conclusions, some even self-contradictory. AFAIK right now there is no single, definitively reliable forensic study of Hunter’s Hard Drive.
Both the Examiner and CBS use the same methodology: proving that the data appears as a user would have used it. WEll, if you hijack someone’s iCloud account that’s what you’ll get.
So it seems that someone got access to Hunter’s laptop and iCloud accounts and planted information.
I’m old enough to remember emails winding up on Weiner’s laptop in late 2016.
Besides laptops and sex workers, what is the connection? Giuliani.
>2/20/19: where the fuck are youi? from DroidHunter88 to dpagano:
this is hunter
i dont have your #
call me please
Could this be real? yeah…sure…but it reads almost exactly (awkward use of #, typos, vagueness) like the increasing amount of impersonation spam that I get at work from ‘colleagues’
I can’t find the article from a few years back, because every related keyword has been co-opted by news stories on right wing propaganda operations, but I distinctly remember an article about a journalist who’s emails were hacked by Russia/a Russian cutout who remarked that most of them were real, but there were a smattering of fake ones that ran the gamut from innocuous to potentially embarrassing that had been added to the leak.
And apart from inserting fake emails, removing real emails can do as much damage, or more, by eliminating context. A totally innocent email chain can be tweaked to look nefarious by getting rid of one or more emails.
I think droidhunter was still not under his control at that time. If that’s right, this is a way to get a pimp or dealer to call him w/o him asking to.
going through the Marco Polo Report (p 307), it stood at to me that he allegedly texts a previous escort/pimp on 3/9/19 8:27am
“Hi my name is Hunter and I was hoping you were available… I am staying at ”
Which didn’t have a response but it stood out for using name Hunter as opposed to Rob, and having good grammar in a text message.
Once the hard drive was erased on the purloined laptop, and the data hacked from iCloud, you just gotta make the planted data look good to Time Machine, and voila! The MacOS is based on BSD Unix, so there are ways around “Hey, the image you are trying to restore from doesn’t checksum.”
Forgive me for being perhaps woefully uninformed about this, but I have followed the story all along and here’s something I have never been able to verify: Does Hunter Biden’s laptop actually exist? I have never seen anyone provide a shred of evidence that it does. As far as I can tell, all that has been produced is a hard drive, which passed through many hands, a number of them known liars with a history of hostility to the Bidens, and is therefore useless to prove anything. What I have always suspected is that some hackers, probably in Russia, where they are so good at this, obtained a significant amount of data from Hunter’s laptop, including some apparently genuine sexual material, placed it on a hard drive and then studded the hard drive with manufactured politically incriminating falsehoods. If there actually is no laptop to be found, why should we not believe that this is the true story?