Could Roger Stone Be Charged in a CFAA Conspiracy?
I just did an extended rant on Twitter about Jonathan Chait’s latest attempt to pretend to be covering the Russian investigation. Basically, though, I was making the same point I made in this post: Mueller is not going to charge Roger Stone just for talking to WikiLeaks — or even having advance knowledge about what WikiLeaks planned to do. So to try to understand what Mueller is after, you need more than a Chait-like titillation that Stone exchanged some DMs with Guccifer 2.0 or, much later, WikiLeaks.
In response to that, a number of people suggested that Mueller might charge Stone for conspiracy to hack (under the Computer Fraud and Abuse Act) after the fact.
You don’t charge people for entering into a conspiracy after the crimes have been committed.
In fact, in one of Roger Stone’s denials, to Chuck Todd earlier this year, he tried to make this point — that he can’t be held responsible for any hacking because the hacking happened before he started interacting with the purported hacker, Guccifer 2.0.
Todd: Why did you reach out to Guccifer? Why did you reach out to Wikileaks?
Stone: First of all, my direct messages with Guccifer 2.0, if that’s who it really is, come six weeks, almost six weeks after the DNC emails had been published by Wikileaks. So in order to collude in their hacking, which I had nothing whatsoever to do with, one would have needed a time machine.
And (at least based on what we know) I believe that’s true, with respect to the March 19, 2016 hack of John Podesta and the May 25, 2016 exfiltration of the DNC emails. Nothing we know suggests Stone was part of a conspiracy with the Russians that early (though I don’t rule it out, particularly given his recruitment of Paul Manafort around the same time as the Podesta hack). Nothing we know says Stone can be shown to have entered into a conspiracy with Russia before the hack of Podesta or the DNC.
But it is not the case that no hacking occurred after Trump and his allies are suspected of entering into a conspiracy. Mueller provided a really remarkable example in the GRU indictment, showing that after Trump asked the Russians for Hillary’s emails, they launched a new wave of attacks on targets close to Hillary.
The Conspirators spearphished individuals affiliated with the Clinton Campaign throughout the summer of 2016. For example, on or about July 27, 2016, the Conspirators attempted after hours to spearphish for the first time email accounts at a domain hosted by a third-party provider and used by Clinton’s personal office. At or around the same time, they also targeted seventy-six email addresses at the domain for the Clinton Campaign.
There’s another example in the indictment, involving Stone, which is more subtle.
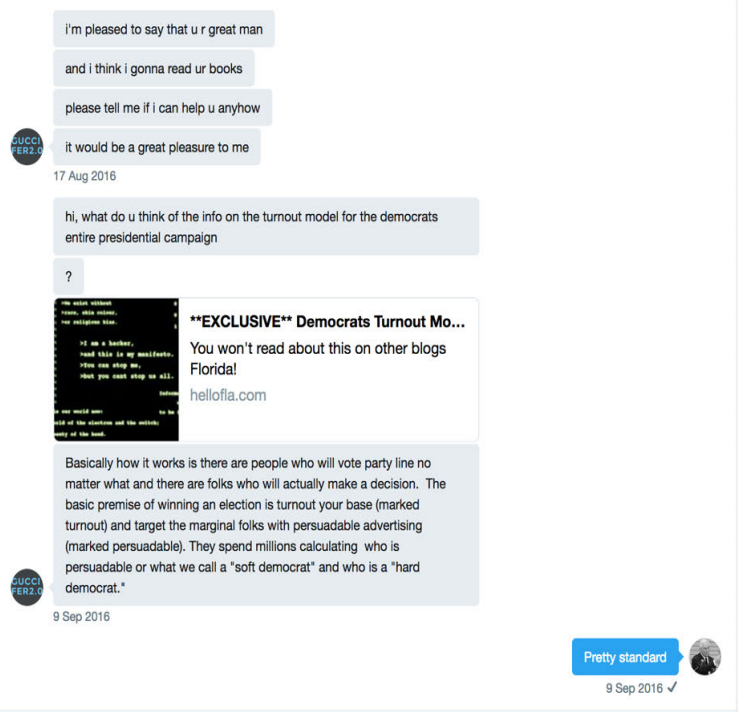
The indictment summarizes key parts of Stone’s conversation with Guccifer 2.0, describing him as someone who “was in regular contact with senior members of the presidential campaign of Donald J. Trump.” It describes how Guccifer 2.0 asked Stone if he could be of assistance, then asked him what he thought of a turnout model earlier released to and highlighted by Aaron Nevins (whom the indictment describes as a “a then-registered state lobbyist and online source of political news”). As the indictment describes, Stone said that that turnout model was “pretty standard.”
The Conspirators, posing as Guccifer 2.0, also communicated with U.S. persons about the release of stolen documents. On or about August 15, 2016, the Conspirators, posing as Guccifer 2.0, wrote to a person who was in regular contact with senior members of the presidential campaign of Donald J. Trump, “thank u for writing back . . . do u find anyt[h]ing interesting in the docs i posted?” On or about August 17, 2016, the Conspirators added, “please tell me if i can help u anyhow . . . it would be a great pleasure to me.” On or about September 9, 2016, the Conspirators, again posing as Guccifer 2.0, referred to a stolen DCCC document posted online and asked the person, “what do u think of the info on the turnout model for the democrats entire presidential campaign.” The person responded, “[p]retty standard.”
It looked like this:
Sometime in September — the indictment is coy about whether it happened before or after September 9 — Russian hackers accessed the DNC’s analytics on an AWS server and made a copy, thereby stealing it.
In or around September 2016, the Conspirators also successfully gained access to DNC computers hosted on a third-party cloud-computing service. These computers contained test applications related to the DNC’s analytics. After conducting reconnaissance, the Conspirators gathered data by creating backups, or “snapshots,” of the DNC’s cloud-based systems using the cloud provider’s own technology. The Conspirators then moved the snapshots to cloud-based accounts they had registered with the same service, thereby stealing the data from the DNC.
Accessing the Democratic analytics program updated daily — even if, as I’ve been told happened, the Democrats discovered and shut down this effort before Russians could obtain more valuable trend data — would presumably be far more valuable than leaking a targeting document dating to February 9. It would be far more damning, too, if that theft came after a close associate of the candidate (and the recently departed campaign manager) had poo-pooed the dated targeting data as standard fare, suggesting Trump’s team wanted something more valuable.
We don’t know what happened to that analytics data after Russia stole it. But the GRU indictment does show not only that Stone was interacting with Guccifer 2.0 before that theft in September, but that he may have even provided feedback about similar information before the theft of more valuable, timely turnout information.
That probably still doesn’t get you to a CFAA conspiracy by itself (which is a different matter than a ConFraudUS conspiracy based off accepting a thing of value from a foreigner, for which there’s more solid evidence). But the two events taken in tandem suggest Russian hackers may have been responding to feedback from both the candidate and his longtime political advisor Roger Stone. The question, then, is what kind of agreement that responsiveness took part in.
As I disclosed in July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.