In Discussion of Unmasking Admiral Rogers Gets Closer to Admitting Types of Section 702 Cybersecurity Use
Last Friday, Director of National Intelligence Dan Coats, Director of NSA Mike Rogers, and FBI Director Christopher Wray did an event at Heritage Foundation explaining why we need Section 702 and pretending that we need it without reasonable reforms. I attended Wray’s talk — and even got my question on cybersecurity asked, which he largely dodged (I’ll have more about two troubling things Wray said later). But I missed Rogers’ talk and am just now catching up on it.
In it, he describes a use of Section 702 that goes further than NSA usually does to describe how the authority is used in cybersecurity.
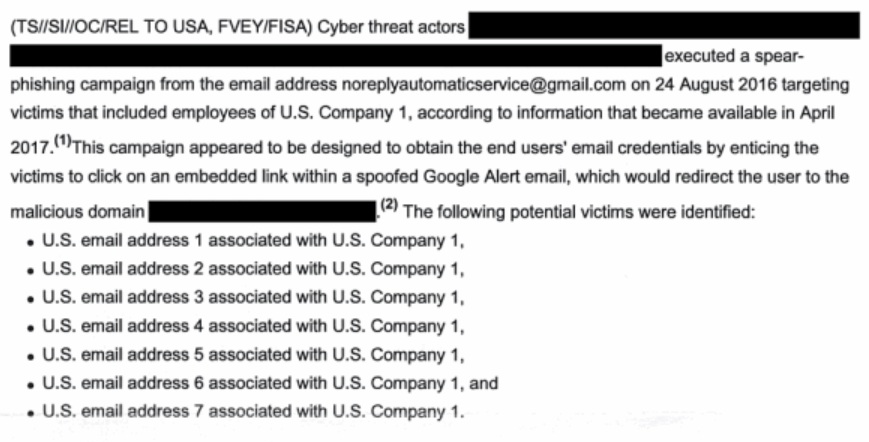
So what are some examples where we’ll unmask? Companies. Cybersecurity. So we’ll report that US company 1 was hacked by the following country, here’s how they got in, here’s where they are, here’s what they’re doing. Part of our responsibility on the US government side is the duty to warn. So how do you warn US company 1 if you don’t even know who US company 1 is? So one of the reasons we do unmasking is, so for example we can take protective to ensure this information is provided to the appropriate individuals.
What Rogers describes is an active hack, by a nation-state (which suggests that rule may not have changed since the 2015 report based off 2012 Snowden documents that said NSA could only use 702 against nation-state hackers). The description is not necessarily limited to emails, the type of data NSA likes to pretend it collects in upstream (though it could involve phishing). And the description even includes what is going on at the victim company.
Rogers explains that the NSA would unmask that information so as to be able to warn the victim — something that (via the FBI) happened with the DNC, but something which didn’t happen with a number of other election related hacks.
Of course, Reality Winner is facing prison for having made this clear. The FISA-derived report she is accused of leaking shows how the masking works in practice.
In the case of VR Systems, the targeted company described, it’s not entirely clear whether NSA (though FBI) warned them directly or simply warned the states that used it. But warnings, complete with their name, were issued. And then leaked to the press, presumably by people who aren’t facing prison time.
In any case, this is a thin description of NSA’s use of 702 on cybersecurity investigations. But more detail in unclassified public than has previously been released.




Questions:
Did they detect the alleged phishing going to the companies domain? Or did they detect via emails that went to the employees cell phones? (if, assuming phishing at all)
Put another way, did NSA correlate the employees cell phones to the company?
The data available to NSA would allow them to map the employee to company relationship.
Especially with real-time cell phone tracking.
They know the location of the company, and with real-time cell phone tracking, it would not be a lot of effort to figure out who works there.
And, in conjunction with prior leaks, and if realtime is available, bad guys can figure out where people with security clearance work.
OPM was the hack/leak/exfiltrate I was referencing.