The Shadow Brokers Vulnerability Equities Process: NSA Has Had at Least 96 Days to Warn Microsoft about These Files
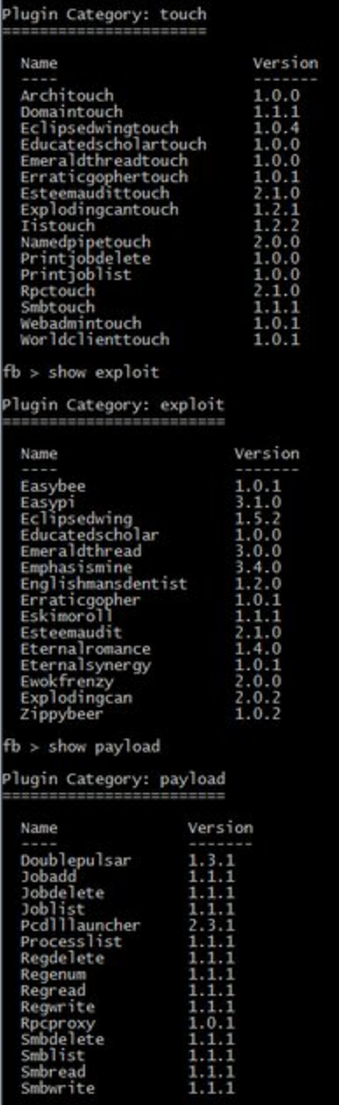
On January 8, Shadow Brokers announced an auction of Windows Warez, with lists of the exploits he/they had for sale (these two posts from Malware Jake provide analysis of them). Four days later, SB released a different set of Windows exploits, a more dated set that (SB claimed) Kaspersky Labs had had some visibility onto. The Windows files released today include the ones offered for sale back in January, down to the version numbers. Compare, in particular, the touch, exploit, and payloads with this screencap. SB announced Fuzzbunch and DanderSpritz in January, too.
That’s a critical detail for the debate going on on Twitter and in chats about how shitty it was for SB to release these files on Good Friday, just before (or for those with generous vacation schedules, at the beginning of) a holiday weekend. While those trying to defend against the files and those trying to exploit them are racing against the clock and each other, it is not the case that the folks at NSA got no warning. NSA has had, at a minimum, 96 days of warning, knowing that SB could drop the files at any time.
The big question, of course, is whether NSA told Microsoft what the files targeted. Certainly, Microsoft had not fully responded to that warning, as hackers have already gotten a number of these files to work.
With WikiLeaks’s Vault 7 files, it’s at least possible the CIA doesn’t know precisely what got leaked to WikiLeaks, even though the government immediately identified when and how the files were breached. The NSA cannot make that claim here, at least not with the Windows files. SB was kind enough to provide warning. The question is, what did NSA do with that warning.
The fact that SB provided that warning, though, should have very serious ramifications for the Vulnerabilities Equities Process, under which the NSA is supposed to consider whether it is better to alert companies to exploits or to sit on them and use them. It’s one thing to decide NSA’s spying takes precedence over the security of the customers of big American companies. It’s another thing to keep those exploits in a way that makes them vulnerable to theft, as both CIA and NSA have done.
But it should be beyond question that when an intelligence agency gets a very detailed list of a group of exploits a malicious entity plans to release, the agency should warn the American companies affected.
Update: Microsoft told Sam Biddle they haven’t heard from any “individual or organization.”
A Microsoft spokesperson told The Intercept “We are reviewing the report and will take the necessary actions to protect our customers.” We asked Microsoft if the NSA at any point offered to provide information that would help protect Windows users from these attacks, given that the leak has been threatened since August 2016, to which they replied “our focus at this time is reviewing the current report.” The company later clarified that “At this time, other than reporters, no individual or organization has contacted us in relation to the materials released by Shadow Brokers.”
I think there’s actually some wiggle room in there. We shall see how long it takes MSFT to patch this stuff.
Update: MSFT released a statement that said all but three of these had been addressed. Three of them were addressed in their March update, and another this year. Which would suggest NSA did warn them.