No More Secrets: Vault 7
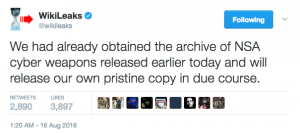
Several days after Shadow Brokers first announced an auction of a bunch of NSA tools last August, Wikileaks announced it had its own “pristine” copy of the files, which it would soon release.
Wikileaks never did release that archive.
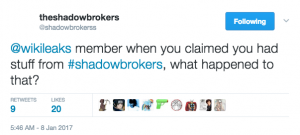
On January 7-8, Shadow Brokers got testy with Wikileaks, suggesting that Wikileaks had grown power hungry.
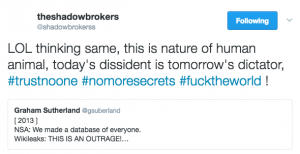
Shadow Brokers threw in several hashtags, two of which could be throw-offs or cultural references to a range of things (though as always with pop culture references, help me out if I’m missing something obvious). The third — “no more secrets” — in context invokes Sneakers, a movie full of devious US intelligence agencies, double dealing Russians, and the dilemma of what you do when you’ve got the power that comes from the ability to hack anything.
Moments later, Shadow Brokers called out Wikileaks, invoking (in the language of this season’s South Park) Wikileaks’ promise to release the file.
Of course, within a week, Shadow Brokers had reneged on a promise of sorts. Less than an hour before calling out Wikileaks for growing power hungry, Shadow Brokers suggested it would sell a range of Windows exploits. Four days later, it instead released a limited (and dated) subset of Windows files — ones curiously implicating Kaspersky Labs. All the “bullshit political talk,” SB wrote in a final message, was just marketing.
Despite theories, it always being about bitcoins for TheShadowBrokers. Free dumps and bullshit political talk was being for marketing attention.
And with that, the entity called Shadow Brokers checked out, still claiming to be in possession of a range of (dated) NSA hacking exploits.
Less than a month later (and over a month before Monday’s release), Wikileaks started the prep for the Vault 7 release of CIA’s hacking tools. (Given the month of lead hype and persistent attention throughout, I’m not sure why any claimed rapid and “overwhelming” response to the release should be attributed to Russian bots.)
Having been called out for sitting on the Shadow Brokers’ files (if, indeed, Wikileaks actually had them), Wikileaks this time gave the appearance of being forthcoming, claiming “the largest ever publication of confidential documents on the [CIA].”
Except …
While Wikileaks released a great deal of information about CIA’s hacking, it didn’t release the code itself, or the IP addresses that would reveal targets or command and control servers.
Wikileaks has carefully reviewed the “Year Zero” disclosure and published substantive CIA documentation while avoiding the distribution of ‘armed’ cyberweapons until a consensus emerges on the technical and political nature of the CIA’s program and how such ‘weapons’ should analyzed, disarmed and published.
Wikileaks has also decided to redact and anonymise some identifying information in “Year Zero” for in depth analysis. These redactions include ten of thousands of CIA targets and attack machines throughout Latin America, Europe and the United States.
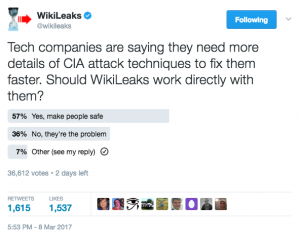
Now, perhaps Wikileaks really is doing all this out of a sense of responsibility. More likely, it is designed to create a buzz for more disclosure that WL can use to shift responsibility for further disclosure. Yesterday, Wikileaks even did a silly Twitter poll designed to get thousands to endorse further leaks.
In reality, whether for their own PR reasons or because it reflects the truth, tech companies have been issued statements reassuring users that some of the flaws identified in the Wikileaks dump have already been fixed (and in fact, for some of them, that was already reflected in the Wikileaks documents).
Thus far, however, Wikileaks is sitting on a substantial quantity of recent CIA exploits and may be sitting on a significant quantity of dated NSA exploits. Mind you, the CIA seems to know (belatedly) precisely what Wikileaks has; while NSA has a list of the exploits Shadow Brokers was purportedly trying to sell, it’s not clear whether NSA knew exactly what was in that dump. But CIA and NSA can’t exactly tell the rest of the world what might be coming at them in the form of repurposed leaked hacking tools.
There has been a lot of conversation — most lacking nuance — about what it means that CIA uses code from other hackers’ exploits (including Shamoon, the Iranian exploit that has recently been updated and deployed against European targets). There has been less discussion about what it means that Wikileaks and Shadow Brokers and whatever go-betweens were involved in those leaks might be involved have been sitting on US intelligence community exploits.
That seems like a worthwhile question.
Update: as his delayed presser on this release, Assange stated that he would work with tech companies to neutralize the exploits, then release them.





regarding the wikileaks poll re should they release the anonymised data so Tech co’s can “fix” backdoors/etc, what is your opinion? Should wiki release that info? Do you think wiki is withholding it because of how it might reflect on Nation/State actors, thus “protecting” the identities of those actors? I guess if you are going to leak such explosive revelations re IC exploits/backdoors/exploits that could be used for plausible deniable assassinations via remote vehicle control hacking it would seem appropriate to dump everything you have, so everyone can draw their own conclusions… does that seem realistic?
I’m agnostic at this point, which is why I made several suggestions above.
Security researchers are definitely already able to use what has been released, so it’s not like Assange didn’t provide tools that could be misused. But this does at least appear more responsible than past practice, so it could just be a PR blitz, an attempt to get big tech on his side. Alternately, maybe he’s holding them for his own purposes?
I truly do not know.
“(including Shamoon, the Iranian exploit that has recently been updated and deployed against European targets).”
“Kaspersky Lab noted that due to the attack’s unsophisticated design, the errors contained in it, and statements from the apparent hackers, they believe it more likely came from hacktivists rather than nation-state developers in Iran” — https://www.wired.com/2015/02/nsa-acknowledges-feared-iran-learns-us-cyberattacks/
“The researchers also noted the possibility that one or both of the embedded language sections are “false flags” intended to mislead investigators about the origins of the malware. ” — https://www.wired.com/2015/02/nsa-acknowledges-feared-iran-learns-us-cyberattacks/
Fair, thank you.
Does anyone else get the sense that the latest dump was a kind of threat — as in, “Drop the investigation or we will release your code”?
The timing of the whole thing (along with the fact that they didn’t actually release the code this time) makes me wonder.
YUP. My first impression, especially since it is all outdated stuff.
I may be missing something, but is it generally accepted the ShadowBrokers are non state actor?
Non-state actor?
Not to me. Various tells say it is really some part of the gang of seventeen.
It is all about money. Events of recent months point to a cyberwar within the GO17. Prime battlers for the money being NSA and CIA, but with others on the sides betting on the victor.
We do not want a Victor. We want Truth.
Trump’s notion of efficiency: Hire more staff for ICE. Pay for it by cutting budgets of Coast Guard, TSA and FEMA.
Robbing Peter to pay Paul doesn’t quite capture the absurdity. Assure more deaths and harm to those at sea, make smuggling easier, make airport screening harder, reduce or slow checks of baggage and freight, and make the country less able to respond to inevitable, global warming-caused increases in natural disasters.
Are these “priorities” a bright shiny object to vex critics still tied to the real world? An example of typical Trump avoidance of decision-making by making his own people fight for fewer crumbs? Is this more evidence that Mr. Trump really is hapless and destructive in equal measure? Or does Mr. Trump hope that a Republican Congress will appreciate his prudence but hire more ICE staff and maintain funding for the departments he appears to be throwing under the bus?
Ueber-capitalists like mega-developers and Goldman Sachs fellows throw around claims that they are driven by “creative destruction”. I suspect that’s just a ruse for the destruction.
So what are the tells that shadow brokers is one of the 17?
One is that there were no bidders.
Tells you most suspected a trap and/or not worth it due to being old. Later, SB confirmed some was old. How many servers still run Solaris these days? Interestingly, SB notes that it uses a self-destructing rootkit. Fine, that makes sense these days. But late Y2k?
That tells me the exploits were probably put together by some group inside NSA.
So, is NSA hacked? Was SUN paid off? Are the exploits worthless today because no one uses old enough versions of the OS anymore?
Is there a group inside NSA intentionally leaking these tools because they are basicallly worthless?
You might think that is the case until you read below.
http://www.networkworld.com/article/3137065/security/shadow-brokers-leak-list-of-nsa-targets-and-compromised-servers.html
“Most of the servers were running Solaris, although some were running FreeBSD or Linux. The compromised servers were reportedly targets of INTONATION and PITCHIMPAIR; the leak also included a list of previously undisclosed Equation Group tools: Dewdrop, Incision, Jackladder, Orangutan, Patchicillin, Reticulum, Sidetrack and Stoicsurgeon.”
And now this new news (or fake news?)
https://www.cyberscoop.com/shadow-brokers-leak-nsa-linked-microsoft-hacking-tools/
‘The mysterious group that claims to have stolen digital weapons once used by the National Security Agency published a trove of active Microsoft Windows software exploits on Thursday.
The code dump, accompanied by a farewell message written in broken English by the enigmatic group the Shadow Brokers, confirms claims implicit in an earlier post Sunday. While the prior message showed filenames, directories and screenshots — implying the existence of these capabilities — along with an associated price tag, today’s download provides functional code.”
Again, it is old stuff (for Windows in this case), but in this case, SB has dumped some code that is supposed to be from NSA, while WL has not yet released any code that is supposed to be from CIA.
[Note that the code dump will lead to signatures even if the code is old]
It is Spy vs Spy. There is a cyberwar going on,
and it looks like it is NSA vs CIA fighting to preserve their legitimacy and claim as much Black OPs money as they can.
There may be moles from each agency woriking at the other agency. They may all be double dipping. Both agencies may already be hacked because of the moles implanting backdoors.
Your tax dollars at work.
I think, and I could probably be very wrong, that there is major infighting in the Intell Agencies. Not just one or two, but all 17 that we know of. Also, if Wikileaks has this info from the CIA, they probably have all the dirt on the objects/persons of the spy ops. I say that because they say they released only around 1%. I know that many of you do not like Wikileaks, I do. I do not think such secrets should be allowed. So far, there has been nothing released that would put our country in jeopardy. The political fools in DC will say so, but just letting Americans know the CIA has targeted all of us in spying is not a threat to our country.
“The third (hashtag)— “no more secrets” — in context invokes Sneakers”
The phrase in Sneakers was “too many secrets”.
The SETEC phrase was. But no more secrets is from the movie. It comes right when they discover what the chip can do. (It actually appears at least twice.)
Like Mr. Trump, Jeff Sessions loves to double down on mistaken facts and failed policies. In setting new priorities for US Attorneys, Sessions is apparently doubling down on the failed “war on drugs”. The policy has proven as effective in fighting crime and reducing drug use as climate change denial has been in reducing the rate of global warming. It has been effective in helping militarize local and state police forces, in making them dependent on exceptionally aggressive asset forfeiture mechanisms, and in keeping alive the right’s culture war on democracy and domestic dissent. It has also been exceptionally profitable for the private prison business. Nothing racist or destructive about Mr. Sessions’s “law and order” priorities here. Nope. Nada.
It would be interesting to carry ‘1st posted’ dates next to the names of posters here. I think we’d find that there are a few whose arrival coincided with the great putinbot-splosion of 2016.
If you may be speaking of me, I assure you I’ve been around a very long time. I read here, but do not always comment. Marcy, Bmaz, and Rayne know me. I come off as crazy, but only because this shit is so fantastic you can’t believe it at times. Just the way the Politicians want it. (grins)
Yeah, I’ll vouch for you.
Times two.
MARCY,
Do you have the document from this post: https://www.emptywheel.net/2016/07/15/fbi-established-saudi-task-force-just-before-joint-inquiry-release/
I’m asking because I tried your link and the page is blank. Maybe Team Trump removed it with the many others. Anyway, I have stumbled upon something that leads me to think there are dots to follow in the footnotes of the official Congressional docs.
Thanks for your time.
A SHOUTOUT TO BEVAN: I keep looking and asking all over the internet for the proof of Russian hacking. Now that it’s out the CIA uses Russian malware and Russian “signatures” it seems to me that anyone who trusts anything out of the CIA is a fool.
And yet still no one can provide links to actual proof. Having Republicans talking to Russians is not a slam dunk. It’s an inference. I presume Exxon et al had Russian arctic drilling dangled in from of their eyes for a post-Obama world with a less warlike relationship with the US. And Trump can’t even deliver that.
So Bevan, can you give us some links? I’ve asked Emptywheel and apparently she is silenced by some agreement with intelligence insiders.
Emptwheel silenced? LOL. There has yet to be ANY hard proof. There are swarms of journalists salivating to get hold of proof. It is was there, it would be here. Emptywheel would NEVER let that pass.
OT?: Approx 100 zero-days alive and well. Average useful lifetime 6.9 years. Should be no wonder why they are hoarded and only old exploits are ‘leaked’.
[This is not to imply that the approx 100 lead to direct root. Likely in many targets multiple different zero-days have to be chained together before the attacker finally has root and can install a persistent rootkit]
https://theintercept.com/2017/03/10/government-zero-days-7-years/
The wiki TROVE is anything but …. its empty ! There is really nothing there. Did anyone not think the USCIA could penetrate various servers and devices? WTF ? Of course they can. There is really nothing new on wiki but the names of supposed projects. No code, no actual exploits…just people talking about them. WHAT HYPE!