My Boob Clinic Is Part of an International Spying Plot … but Hillary’s on It!
By now you’ve likely read or at least heard about this Slate story, which uses a bunch of innuendo arising from some metadata to suggest that Trump has a secret exclusive communication method with Russia’s biggest bank.
A number of people have debunked the technical claims in the article.
Former GCHQ employee Matt Tait did so in a series of tweets here. Consultant Naadir Jaawa laid out how it’s a marketing server here. Consultant Robert Graham not only lays out the same spam email explanation that both Spectrum Health and Mandiant describe in the story, but notes that other malware researchers question the data in the story.
Indeed, one journalist did call one of the public resolvers, and found other people queried this domain than the two listed in the Slate story — debunking it. I’ve heard from other DNS malware researchers (names remain anonymous) who confirm they’ve seen lookups for “mail1.trump-email.com” from all over the world, especially from tools like FireEye that process lots of spam email. One person claimed that lookups started failing for them back in late June — and thus the claim of successful responses until September are false.
Krypt3ia, in a post written in steps weeks ago, couldn’t get answers from the “Tea Leaves” behind the story and judged that the incriminating files — which were just text files — could be recreated.
These are the key files in the new dump but the problem I have is that they are just text files. Anyone with the know how could re-create these to look legit enough but yet still be questioned. I see no actual login to the shell and queries being run here so really coulda just done a find/replace on another query on any server you have access to.
In short, contrary to what Slate suggests, there are innocent explanations for this, and there’s good reason to distrust the provenance of the data behind it.
Update: The Intercept has now explained why they passed on the story; they include spam sent to both Alfa and Spectrum from Trump, which corroborates the theory everyone else technical is settling on.
Boob Clinics usually stay out of international spy plots
Most of these debunkings have focused on the technical aspects. I want to start with this passage from Slate.
A small portion of the logs showed communication with a server belonging to Michigan-based Spectrum Health. (The company said in a statement: “Spectrum Health does not have a relationship with Alfa Bank or any of the Trump organizations. We have concluded a rigorous investigation with both our internal IT security specialists and expert cyber security firms. Our experts have conducted a detailed analysis of the alleged internet traffic and did not find any evidence that it included any actual communications (no emails, chat, text, etc.) between Spectrum Health and Alfa Bank or any of the Trump organizations. While we did find a small number of incoming spam marketing emails, they originated from a digital marketing company, Cendyn, advertising Trump Hotels.”)
Spectrum accounted for a relatively trivial portion of the traffic. Eighty-seven percent of the DNS lookups involved the two Alfa Bank servers.
The story, remember, is that Trump has a super spooky exclusive hotline directly to a corrupt Russian bank. But most people covering this completely ignore that it’s not completely exclusive: over 10% of the traffic reported by the anonymous researchers involves Spectrum Health.
Spectrum Health is the largest employer in Grand Rapids and West Michigan generally. It includes the Helen DeVos Children’s Hospital and a Betty Ford Breast Care clinic. Spectrum Health is where I go to the doctor and Betty Ford is where I got my still cancer-free boobs squished this year. So for this story to make sense, you’ve got to explain why a children’s hospital and a boob clinic are in cahoots with Trump and a big Russian bank.
The original version of the story tried to make much of the tie to Spectrum, finding in the children’s hospital named after Richard DeVos’s wife a tie to Erik Prince (Helen’s daughter-in-law Betsy’s brother) and the DeVos family’s multinational pyramid scheme, the wealth from which has always — not just this year — been funneled into conservative causes.
The other frequent connection to Trump’s hidden server with the same distinctive human pattern is Spectrum Health, a Michigan hospital with close ties to the DeVos family (http://www.spectrumhealth.org/locations/helen-devos-childrens-hospital). The Devos family founded Amway / Alticor which operates in Russia including transactions with Alfa Bank such as buying insurance for 800 Alticor employees from Alfa Bank’s insurance subsidiary. The Devos family has given millions of dollars in the past few months to conservative super PACs (www.fec.gov). One member of the Devos family was a founder of Blackwater.
None of that makes sense, though, especially since — while some of the DeVoses do seem to be funding Trump now and Prince has bizarrely backed the Donald (though that may stem from being shut out of State business while Hillary was in charge) — the biggest commonality between the DeVoses (who are hard core Republicans) and Trump is their multinational scheming and fondness for sports teams.
They may both be awful conservatives, but they are different kinds of awful conservatives, and there’s little reason to believe they’d be in cahoots outside of belated efforts, post-dating these files, to fund Republican turnout in the state (and even there, Prince’s sister Betsy is withholding direct funding).
More importantly, the DeVoses no more run this hospital than Betty Ford does.
But without the conspiracy theories implicating the DeVoses, then innocent explanations sure look a lot more plausible.
Tellingly, however, most other treatments of this story (this is an exception) have simply ignored this detail. Because once you have to calculate how a children’s hospital and a boob clinic — even one, or perhaps especially one, named after Gerald Ford’s wife — has a tie to this international spy plot, things start falling apart.
The reason why the boob clinic part of the story is important is it’s a detail that should have led even non-technical people to at least think twice before running with the story. Slate, however, simply included Spectrum’s explanation for the files, the one that matched Mandiant’s working hypothesis, and careened ahead.
The FBI has its own doubts
After Slate published, the NYT posted a story that generally reveals the FBI hasn’t been able to substantiate any tie between Trump himself and Russia and has backed off its claims that Russia was trying to decide the election (a judgment I hope to return to).
It also reveals that the FBI largely agreed with what security experts concluded when they saw this claim.
In classified sessions in August and September, intelligence officials also briefed congressional leaders on the possibility of financial ties between Russians and people connected to Mr. Trump. They focused particular attention on what cyberexperts said appeared to be a mysterious computer back channel between the Trump Organization and the Alfa Bank, which is one of Russia’s biggest banks and whose owners have longstanding ties to Mr. Putin.
F.B.I. officials spent weeks examining computer data showing an odd stream of activity to a Trump Organization server and Alfa Bank. Computer logs obtained by The New York Times show that two servers at Alfa Bank sent more than 2,700 “look-up” messages — a first step for one system’s computers to talk to another — to a Trump-connected server beginning in the spring. But the F.B.I. ultimately concluded that there could be an innocuous explanation, like a marketing email or spam, for the computer contacts.
Note, this means that the FBI was already looking into this story when it got shopped to reporters in early October. So in addition to the four or so other entities that reviewed this story and found it wanting (including me), the FBI had already had a crack at it.
Hillary Clinton and her likely National Security Advisor jump on this story
Now, as with the Kurt Eichenwald story claiming to have found a smoking gun tying Trump to Putin, people on the left didn’t read the story very critically. Sure, this one is technically hard — up until you think about the boob clinic connection alleged in the middle of the spy plot. But for all its breathlessness, the Slate story simply insinuated. It proved nothing.
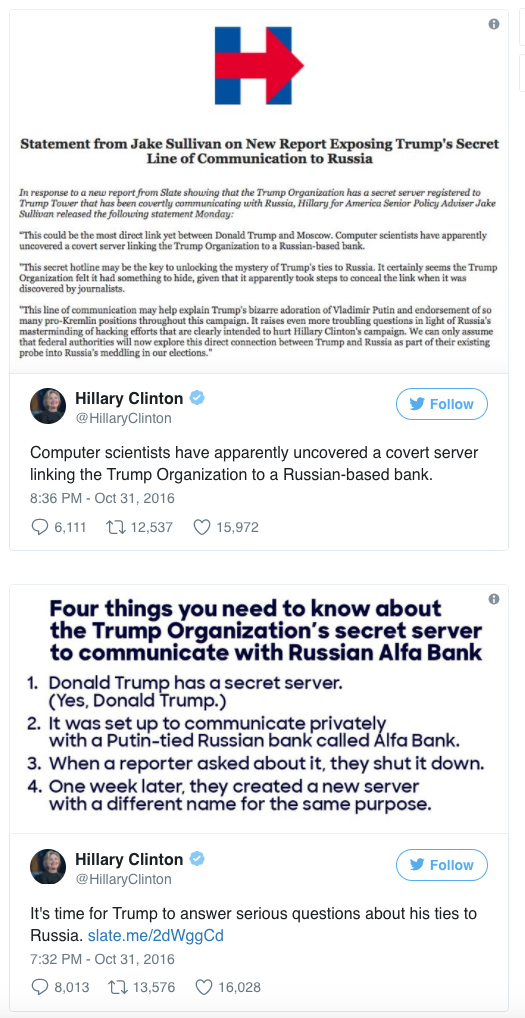
Which is why I’m so troubled that Hillary Clinton tweeted it four times in three hours, including a statement her likely National Security Advisor Jake Sullivan put together.
I mean, I get that it’s election season and all. I get that Jim Comey gave Hillary a whopping October surprise on Friday. But one of the reasons we’re supposed to elect Hillary over Trump is that she is more measured and fact-based than Donald is.
Here, she jumped on a story that at least should have given pause and created two campaign messaging pieces around it, asserting as fact that “Donald Trump has a secret server … set up to communicate privately with a Putin-tied Russian bank.”
I’ll repeat again: Jake Sullivan — the guy who wrote the longer statement on this — is widely assumed to be set to take on the job from which Condi Rice started a war by warning about fictional mushroom clouds.
Who are these secret researchers, anyway
Which leads me to a final question a few of the security folks are asking about this story.
In addition to his technical debunking, Robert Graham made an equally important point: researchers shouldn’t be accessing this data for ad-lib investigations into presidential candidates, and it’s not even clear who would have access to it all except the NSA.
The big story isn’t the conspiracy theory about Trump, but that these malware researchers exploited their privileged access for some purpose other than malware research.
[snip]
In short, of all the sources of “DNS malware information” I’ve heard about, none of it would deliver the information these researchers claim to have (well, except the NSA with their transatlantic undersea taps, of course).
And in a second post this morning, Krypt3ia started wondering who’s behind this story.
This was a non story and this was someone’s troll or an IC operation of some kind. I left it at that… That is until last night when this fallacy laden report came out of Slate.
Anonymous Security Professionals
So here is what I believe happened with Slate and Foer. Tea, not happy with my ignoring their bullshit, went on to pimp at least five venues looking for a way to get this wide and Foer was the gullible one to do so. Now, with a live one on the line Tea spun their tale and added the new twist that they are in fact a group of “security professionals” with insider knowledge and that this story is really real. Of course once again they provided no real proof of Trumps servers being configured for this purpose, no evidence of actual emails, and no real forensically sound information that proves any of what they say can be proven in a court of law. This is a key thing and Slate may not care but others do. Even in the previous dumps on the i2p site that tea set up their diagram said “this is what it would look like” would is not proof, that there is speculation and not evidence.
[snip]
Meanwhile, the story spun by Tea and now Camp et al on Slate makes me wonder just who Tea is. Obviously Camp knows Tea and the others and this is a small world so let’s work out the connections shall we?
Camp –>Vixie –> ??? let’s just assume that Camp knows these persons well and if one starts to dig you could come up with a few names of people who “would” (there’s that would again) have the kind of access to DNS data that is needed.
Just sayin.
Of course, we have since learned that before Tea Leaves started pushing this story to the press, the FBI had been investigating it for two months.
Which, to my mind, raises even more questions about the anonymous researchers’ identities, because (small world and all) the FBI likely knows them, in which case they may have known that the FBI wasn’t jumping on the story by the time they started pitching it.
Or the FBI doesn’t know them, which raises still more questions about the provenance of these files.
Ah well, if President Hillary starts a war with Russia based off Iraq-War style dodgy documents, at least I’ll have the satisfaction of knowing my boob clinic is right there on the front lines.
Update: I’ve added language to clarify that the DeVoses don’t run Spectrum.




Lol, you said “front lines” in the same sentence as “boob.”
The real story, of course, is, “I’ll repeat again: Jake Sullivan — the guy who wrote the longer statement on this — is widely assumed to be set to take on the job from which Condi Rice started a war by warning about fictional mushroom clouds,” which says an enormous amount.
You sound authoritative and convincing, rebutting all the other side’s arguments, questioning their expertise, and presenting your own conflicting facts. You must be right, then? Or perhaps a good arguer? :)
I’m not questioning anyone’s expertise.
Okay, but don’t go overboard, methinks.
“But the F.B.I. ultimately concluded that there could be an innocuous explanation, like a marketing email or spam, for the computer contacts.” First, note that that F.B.I. statement does not contradict the Slate story; you point out such vagueness in F.B.I. statements a lot, and criticize others for not seeing it. Second, why would you (of all people) believe what the F.B.I. says? Can I quote you on that in the future?
“None of that makes sense, though”. So what? I’ll bet if you go back and review all your posts for the last five years you will find plenty of stuff that you said at the time “it doesn’t make sense” because you (we) didn’t, at the time, have an explanation for it. And that’s fine—it’s your job as a journalist to bring unresolved issues to the public light. That’s possibly because there are many things in the political world that we never, ever get to know the truth behind. Same as in real life—many crimes are never solved, many facts in criminal investigations don’t add up or jibe with any suspect, people honestly have different recollections of the same event, people don’t tell the truth, etc. So, the fact that something doesn’t make sense doesn’t necessarily mean it’s wrong. Example: The Naadir Jaawa article you link to is technically beyond me, but interestingly, it notes that in one previous investigation, “We never found the root cause”. And these are experts?
Is it at all even conceivable that there is a malevolent explanation (as opposed to an innocuous one) for the existence of the Spectrum Health pings being found alongside he Trump pings? Geez, I don’t think so, there couldn’t, just couldn’t, be any crooks smart enough to do something distracting or creative like that, could there?
Just sayin’. The whole thing is way out of left field, and hard to fathom, so it sounds unbelievable, so I won’t believe it. Still, one could have said that about a large percentage of Trump stuff that popped up in the last six months and one would have been dead wrong.
I think the connection between Trump and a boob clinic is rather obvious — see the Access Hollywood tape, the multiple stories of Trump walking around backstage while beauty contestants are getting dressed, the stories told by multiple women of being groped, the serial trading-up of wives, the endless hours of tape from the Howard Stern show appearances . . .
On the children’s hospital, however, I got nothing.
No way, because you know that most of the women at the boob clinic aren’t supermodels and Trump wouldn’t be interested in grabbing them.
It really is sad that you have to spend time and energy refuting stories of this sort. It is even sadder that Clinton gets involved in nonsense which can only damage America’s relationship with other countries. This is old fashioned southern democrat campaigning, of the worst kind. Hillary is right down there in the gutter, along with her team, throwing mud and spouting poison.
And, as you suggest, it may have awful consequences. It is just another reminder of the curious character of the lady whose response to the bayonet buggery of Ghadaffi is her claim to immortality.
OK. I’m convinced. Nobody hacked Wiener.Huma/Clinton. I’m tired of whodidntdunnit. Hoodiddit?
Marcy,
Another blowing-all-over-the-map-and-all-out-of-proportion story is the latest one re: the FBI’s Hillary’s Private Server investigation, since Comey’s providing notice of its re-opening. Everyone seems to be looking at the political aspects, overlooking the core. The core is a private server used for State secret and privileged message communications.
What has come out, in recap, is that a file of Hillary’s Server emails were found on a husband of a Hillary aid’s laptop in the course of an unrelated investigation, whose warrant rights did not extend to non-subject matter. The aid, Huma Abedin, was questioned, she said she did not know how the Hillary server emails got onto her husband, Anthony Weiner’s, laptop. She was asked to cooperate (to give permission for investigation). This indicates the FBI accepted her assertion of innocence, since asking cooperation is reserved for third parties. It also indicates that the Hillary server emails are not Abedin-Weiner communications, since those would be accessible to the FBI through Weiner. The file is said to contain over 650,000 emails covering a range of years. This suggests a hack and dump copy-out.
A hack and dump copy-out to a third-party computer from Hillary’s unsecured home server, on which were kept sensitive, secret and classified communications is a security issue. It is not a political issue. It is the original issue, the security issue, the primary issue the carelessness and foolishness of the Hillary home server matter. It is, in fact, the worst-case; the prime worry, a security-breach, a hack of the insecure server. This is why Comey could not ignore the issue, or let it ride until after the election. The issue has nothing to do with the politics of the election, it has to do with sensitive State communications being let escape, potentially into the wild.
Who transferred emails from the Hillary server to the Weiner laptop, and where might the emails have been transferred from there? It is quite probable that the Hillary server hacker was Weiner, his access being via the trust relationship of matrimony. Just spying on his wife, or other motive? Did Weiner transfer on? Who might have had, or been able to, hack Weiner’s laptop? His connection to Abedin and hers to Hillary have been known, so he would have been a natural target for hackers. So the Hillary server content on his laptop was extremely insecure, even if he did not have motives, or inclinations, to espionage beyond prying into what his wife was up to.
You can see why the FBI had to re-open the Hillary server investigation, and you should be able to recognize why the new investigation is not political, is not complicated, trumps politics and could not be put off for politcal customs, traditions or usual practice. It has nothing to do with what Hillary, or her campaign, might or might not have planned or plotted, it has only to do with the security of her use of a home server. The Weiner laptop evidences that the worst that could have occurred in result of the original decision to substitute a home server, did occur: The server was hacked, the data in it was copied away, out of the system. No need for Russians, or Chinese, or technical hacking expertise. Most likely all it took to accomplish the deed was a little misplaced trust.
Just my $0.02 but:
Or it suggests that she used a shared family laptop to check her mail once or twice and, when doing so, chose to “store messages locally” which would automatically download the data to the laptop for storage. Many people have chosen that option accidentally without grasping its true meaning. Acting on Occam’s Razor I would favor the latter for three reasons: First the innocent explanation is not just the simplest but is a common action of the tech nonsavvy; Second, if this were an attempt to hack/hide the emails I find it unlikely that they would then leave the data in the open or with Anthony Sextme Weiner given the efforts that were already taken to hide the info previously (i.e. BleachBit); and Third in this context the best thing for them would be to lose the emails entirely. The Clintons and their aides have been around the block with the discovery process. The of all people should have known that not having any incriminating evidence is the best way to hide it. As such it makes little sense that they would take such care to scrub things in several places and, again, stash the stuff with a guy who likes pics of his…
As
Anon,
If the emails on the laptop are only Abedin’s I would agree a “store locally” option might have been selected, accidentally or deliberately, but the number of emails ascribed, “650,000”, suggests download of the whole server, and Abedin’s testimony is she had no idea how her email would have gotten on the Weiner laptop, which the FBI are indicating they believe (for now, as is customary for belief in investigation situations). That the emails were not at least combed, if not the whole file deleted, when all but “about 30,000” on the clintonmail server were by Clinton Foundation lawyers, also supports Abedin’s assertion, as also does the trove being on a Weiner-possessed laptop, especially after his less than secure cranial component came to light. Abedin, unlike Weiner, does not appear to be at all stupid. I am as confident as you that she would not, as you say, “take…care to scrub things in several places” and leave the Weiner computer unscrubbed, had she known of the stash, or “stash[ed] the stuff with a guy…” like Weiner.
The FBI, with the evidence in hand, will be determining the events, and sequencing.
First, where do you see her testifying that she does not know how they got there. My initial search for testimony does not bring up any public record of what she has said on that.
Second what do you mean by “as is customary forbelief in investigation situations”? For now, based upon publicly available information they are acting like they are investigating it. Whether they believe her or not is not known. Even if they did not believe her they could hardly arrest her on those grounds alone.
Third, I am not sure what you mean by the following, can you clarify?<blockquote>That the emails were not at least combed, if not the whole file deleted, when all but “about 30,000” on the clintonmail server were by Clinton Foundation lawyers, also supports Abedin’s assertion, as also does the trove being on a Weiner-possessed laptop, especially after his less than secure cranial component came to light. </blockquote>
Fourth, With respect to your final statement: “The FBI, with the evidence in hand, will be determining the events, and sequencing.” I agree, that is the premise of an ongoing investigation. The running issue here is that The FBI has repeatedly violated its own rules in this case by leaking information that the ordinary rules of investigations require to be secret. Their leaking is serving to politicize, and arguably inhibit, their own case. It is certainly casting doubt on their impartial interest in facts over press.
And finally with respect to the number it is all I suspect in how you count it. If you reply to an email or forward it, unless told otherwise, the email text will generally be copied into the body of the email. If you count all of those copies separately then the number will get high real quick. That’s not counting the fact that many of these are probably email chains which may have involved several people making several quoted replies which are then re-quoted, and so on. If they are counting it that way (and all of the reporting that I have seen only says “as many as 650,000”) then my own devices are probably that high as well.
I have to defend Evangelista here.
It was not “testimony” which, obviously, is not the only kind of evidence in any case. It was a statement by Abedin to the press and then an official statement by her attorney to both the Govt and press to that effect. Are you seriously going to stand there and say Abedin has not made a substantive claim???
Secondly, if you know squat about DOJ/FBI procedure, you know that, at best, right this second, certainly as to Clinton, and almost certainly as to Abedin, at most they have undertaken an “assessment”, maybe at most a “preliminary review”. Those are different things, with the latter a step more serious than the former. Neither are anywhere near a formal “investigation”. The “DOJ has reopened the investigation” baloney screamed by Trump and ethics challenged GOP morons in the House, is catnip for morons. Don’t bite off on that shit.
Third, there is no good data on what is what on the Weiner device, but it appears not many of the overall 650K emails, going back the better part of a decade, are really at issue as to either Abedin or Clinton.
Fourth, you again either bogusly or dogmatically insist on calling this an “investigation”. You are either rather loose with your terms or uninformed about the actual nature of FBI/DOJ investigation protocol. It is all delineated in the USAM.
Fifth: You may finally be on to something.
Very few read your rambling diatribe. Probably they would, were it more concise and relevant. But, instead, you insist on spoofing our threads with this electronic diarrhea.
You want to participate here, and have anybody but cranks interact with you? Then tighten up your prose.
Wrap it up.
Evangelista says: November 1, 2016 at 8:05 pm
All the experts have said that Clinton’s server wasn’t hacked. If you’re claiming that it was, you need to provide evidence.
P J ,
I only analyzed available evidences. The FBI re-opened the case to determine if the experts got it right, or overlooked an unlooked for spur-branch event. I imagine they, and everyone else, are hoping the evidence, in ultimate analysis, proves the experts’ conclusion not incorrect.
bmaz says:
quote”Very few read your rambling diatribe. ”
I STRENUOUSLY OBJECT YOU’RE HONOR!!! Council’s statement is speculative, and assumes facts not in evidence!!
Besides…I read it.
quote:”Probably they would, were it more concise and relevant. But, instead, you insist on spoofing our threads with this electronic diarrhea.”
On the contrary. I thought evangilista’s post was highly concise and relevant. Especially this..
quote:It has nothing to do with what Hillary, or her campaign, might or might not have planned or plotted, it has only to do with the security of her use of a home server.”unquote
http://tinyurl.com/zcuaa56
here ya go bmaz..
Weiner..meet …Assange
Now THAT oughtta make your head explode.
(-:
boobs smoobs… THIS is mind boggling…
https://www.washingtonpost.com/politics/after-release-of-documents-fbi-finds-itself-caught-in-a-partisan-fray/2016/11/01/9d466908-a068-11e6-8832-23a007c77bb4_story.html
bmaz explosion in… 5…4….3…2…
Why in the world would this, semi-dubious at best, add on make my “head explode”?
I identified immediately the problem with Comey’s actions as to Clinton back in July upon his rogue public statement, and already went full on outrage last Friday at the first instance of public knowledge of the instant situation. This FOIA add on is small potatoes, if potatoes at all.
Granted, it is a bit of a telling add on though. There IS a real problem with lack of institutional control, not only from Comey at FBI, but as to Lynch as AG too. To quote Trump, it is SAD!
Dolly Parton recently had the last word on boobs. “My comment about supporting a woman in the White House was taken out of context. I have not endorsed Hillary Clinton nor Donald Trump. I try not to get political but if I am, I might as well just run myself ’cause I’ve got the hair for it, it’s huge, and they could always use more boobs in the race.”
http://uproxx.com/news/dolly-parton-election-boobs/
Absolute statements as psyop to provoke troll feeding, lies by omission, seems like a paid for, planned for, degrading of the site by commenters. Back to wickileaks, [email protected], you have gotta be kidding me. Someone tell Assange either his leaks or his twitter feed have been hacked.
While I’m going to vote Hillary, I do wish my team would stop trying to red bait us into a second Cold War. It really is like watching the stuff I grew up with all over again, only this time it’s the Democrats using a patsy to distract from their own failures, not the Republicans. Worse, my liberal friends seem more than happy to fall for it, with much the same ugly name calling.
@bmaz, I think that you missed my point. To take your comments:
With respect to your first point I believe you missed what I was saying. I stated that I could not find the statement. Evangelista referred to it as “testimony” hence my querying on that point. I will grant that a public statement is material I never said it was not.
With respect to your second point again the term “investigation” originates from Evangelista’s comment. At different times the press reports have referred to this as being part of an investigation or as being an investigation in and of itself. You are correct in that there are formal distinctions in FBI procedure I have found little clear reporting on what the status of the specific investigation into Hillary Clinton’s emails is so I adopted the term used in Evangelista’s comment in order to reply to it. I see little reason to take such umbrage at my use of it.
With respect to your third point I have found little substantive on the content of the mails other than that they exist and the common refrain that there are “as many as 650k.” I took Evangelista’s claim to be that they were substantive and noted that the high number may result from how such things are counted. At this point I see little reason to assume that they have ruled them as being relevant or irrelevant as my understanding is that they are still sorting them out.
With respect to your fourth point, see my reply to your second point.
Fair points in response! We shall see where the bottom line ends up.
You gotta admit, it is a fascinating situation.
It is indeed. If I had thought that Comey had a sense of humour I’d almost suspect he timed the letter just so he could have the last October Surprise.