Robert Mueller’s Grand Jury and the Significance of Felix Sater
In response to Monday’s server hiccups and in anticipation that Mueller is nowhere near done, we expanded our server capacity overnight. If you think you’ll rely on emptywheel reporting on the Mueller probe, please consider a donation to support the site.
The world is abuzz with the news that Robert Mueller has impaneled a DC-based grand jury that he used to subpoena information on the June 9, 2016 meeting between Don Jr., Paul Manafort, Jared Kushner, and some Russians promising dirt on Hillary Clinton. In reality, the Special Counsel had already been using a grand jury to get information on Mike Flynn and Paul Manafort and we should always have expected a dedicated grand jury.
Nevertheless, the move has convinced the chattering classes that this investigation is for real.
This comes as a surprise to people, apparently, after reports of Mueller’s 16th hire, illegal foreign bribery expert Greg Andres. It’s almost as if people haven’t been making sense of where Mueller is going from the scope of his hires, which include:
- Mob specialists: Andrew Weissman and Lisa Page are mob prosecutors.
- Fraud specialists: Weissman and Rush Atkinson are also fraud prosecutors.
- Corporate crime specialists: Weissman also led the Enron Task force. One of Dreeben’s key SCOTUS wins pertained to corporate crime. Jeannie Rhee has also worked on white collar defense.
- Public corruption specialists: Mueller hired someone with Watergate experience, James Quarles. And Andrew Goldstein got good press in SDNY for prosecuting corrupt politicians (even if Sheldon Silver’s prosecution has since been overturned).
- International experts: Zainab Ahmad, who worked terrorism cases in EDNY, which has some of the most expansive precedents for charging foreigners flown into JFK (including Russia’s darling Viktor Bout), knows how to bring foreigners to the US and successfully prosecute them in this country. Aaron Zelinsky has also worked in international law. Elizabeth Prelogar did a Fulbright in Russia and reportedly speaks it fluently. And, as noted, Andres has worked on foreign bribery.
- Cyber and spying lawyers: Brandon Van Grack is the guy who had been leading the investigation into Mike Flynn; he’s got a range of National Security experience. Aaron Zebley, Mueller’s former chief of staff at FBI, also has that kind of NSD experience.
- Appellate specialists: With Michael Dreeben, Mueller already has someone on the team who can win any appellate challenges; Adam Jed and Elizabeth Prelogar are also appellate specialists. Mueller’s hires also include former clerks for a number of SCOTUS justices, which always helps out if things get that far.
I lay this out there to suggest that in addition to hiring a bunch of super stars, Mueller also appears to have picked people for their expertise. Those picks reflect an already well-developed theory of the case, one formed long before he impaneled his own grand jury. And many of them boast expertise fairly distant from the question of foreign adversary’s hacking a political party’s server.
And I’d suggest there’s good reason for that.
Some of Mueller’s theory of the case undoubtedly comes from whatever evidence Jim Comey’s FBI and Van Grack’s grand jury had already collected, which at least publicly pertains to Mike Flynn’s disclosure problems, his comments to the Russians, and Paul Manafort’s money laundering. Some of it comes from stuff that was being investigated in NY.
But remember: Trump’s sordid ties to Russian mobsters (see categories 1, 2, 3, and 5) go back a long way. One of the best ways to understand what and how close some of those ties are is to look at the case of Felix Sater. Josh Marshall’s description here gets at a lot of the important bits.
Sater is a Russian emigrant who was jailed for assault in the mid-90s and then pulled together a major securities fraud scheme in which investors lost some $40 million. He clearly did something for the US government which the feds found highly valuable. It seems likely, though not certain, that it involved working with the CIA on something tied to the post-Soviet criminal underworld. Now Bayrock and Trump come into the mix.
According to Sater’s Linkedin profile, Sater joined up with Bayrock in 1999 – in other words, shortly after he became involved with the FBI and CIA. (The Times article says he started up with Bayrock in 2003.) In a deposition, Trump said he first came into contact with Sater and Bayrock in the early 2000s. The Trump SoHo project was announced in 2006 and broke ground in November of that year. In other words, Sater’s involvement with Bayrock started soon after he started working with the FBI and (allegedly) the CIA. Almost the entire period of his work with Trump took place during this period when he was working for the federal government as at least an informant and had his eventual sentencing hanging over his head.
What about Salvatore Lauria, Sater’s accomplice in the securities swindle?
He went to work with Bayrock too and was also closely involved with managing and securing financing for the Trump SoHo project. The Timesarticle I mentioned in my earlier post on Trump SoHo contains this …
Mr. Lauria brokered a $50 million investment in Trump SoHo and three other Bayrock projects by an Icelandic firm preferred by wealthy Russians “in favor with” President Vladimir V. Putin, according to a lawsuit against Bayrock by one of its former executives. The Icelandic company, FL Group, was identified in a Bayrock investor presentation as a “strategic partner,” along with Alexander Mashkevich, a billionaire once charged in a corruption case involving fees paid by a Belgian company seeking business in Kazakhstan; that case was settled with no admission of guilt.
All sounds totally legit, doesn’t it?
But there’s more!, as they say.
Sater’s stint as a “Senior Advisor” to Donald Trump at the Trump Organization began in January of January 2010 and lasted roughly a year. What significance that has in all of this I’m not sure. But here’s the final morsel of information that’s worth knowing for this installment of the story.
How exactly did all of Sater’s secret work and the federal government’s efforts to keep his crimes secret come to light?
During the time Sater was working for Bayrock and Trump he organized what was supposed to be Trump Tower Ft Lauderdale. The project was announced in 2004. People paid in lots of money but the whole thing went bust and Trump finally pulled out of the deal in 2009. Lots of people who’d bought units in the building lost everything. And they sued.
In other words, an FBI (and, possibly, CIA) informant had links with two of Trump’s business with ties to the Russian mob for — effectively — the entire extended Mueller tenure at FBI.
This is a point one of the few other people with reservations about Mueller as Special Counsel made to me not long ago. The FBI — Mueller’s FBI — has known about the ties between Trump’s businesses and the Russian mob for well over a decade. The FBI — Mueller’s FBI — never referred those ties, that money laundering, for prosecution in that entire time, perhaps because of the difficulties of going after foreign corruption interlaced with US businesses.
Now, in a remarkably short timeframe, former mob prosecutor Robert Mueller has put together a dream team of prosecutors who have precisely the kind of expertise you might use to go after such ties.
Because now it matters. It matters that the President has all these obligations to the Russian mob going back over a decade, because he can’t seem to separate his own entanglements from the good of the country.
Yes, Robert Mueller convened a grand jury and he has used it to go after the records of a meeting set up by one of Trump’s key Russian allies, Aras Agalarov, and his campaign, the guy who, at the very end of Mueller’s tenure at FBI, helped Trump stage the Miss Universe pageant in Russia, an event that may have marked significant new levels of Trump exposure to Russian compromise. But Mueller was on the trail of Trump and his Russian crime ties long before that. (The person with Mueller reservations actually wondered whether Trump himself wasn’t cooperating with the FBI in this period.)
Folks have made much of this exchange in the NYT’s long interview with Trump.
SCHMIDT: Last thing, if Mueller was looking at your finances and your family finances, unrelated to Russia — is that a red line?
HABERMAN: Would that be a breach of what his actual charge is?
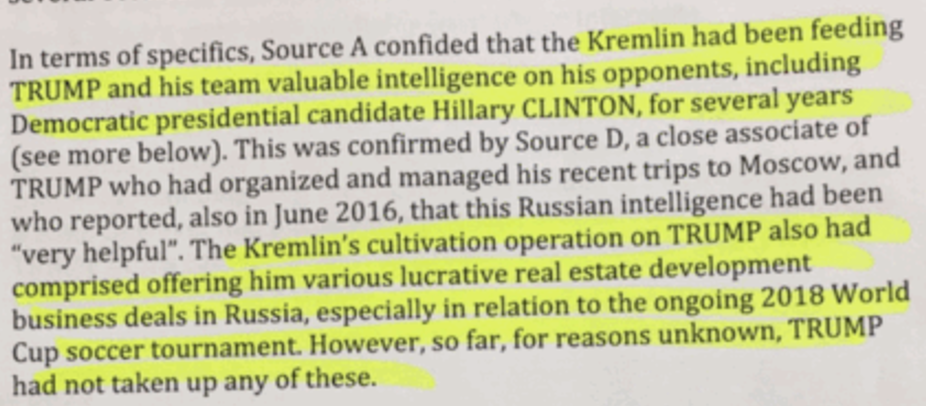
TRUMP: I would say yeah. I would say yes. By the way, I would say, I don’t — I don’t — I mean, it’s possible there’s a condo or something, so, you know, I sell a lot of condo units, and somebody from Russia buys a condo, who knows? I don’t make money from Russia. In fact, I put out a letter saying that I don’t make — from one of the most highly respected law firms, accounting firms. I don’t have buildings in Russia. They said I own buildings in Russia. I don’t. They said I made money from Russia. I don’t. It’s not my thing. I don’t, I don’t do that. Over the years, I’ve looked at maybe doing a deal in Russia, but I never did one. Other than I held the Miss Universe pageant there eight, nine years [crosstalk].
SCHMIDT: But if he was outside that lane, would that mean he’d have to go?
[crosstalk]
HABERMAN: Would you consider——
TRUMP: No, I think that’s a violation. Look, this is about Russia. So I think if he wants to go, my finances are extremely good, my company is an unbelievably successful company. And actually, when I do my filings, peoples say, “Man.” People have no idea how successful this is. It’s a great company. But I don’t even think about the company anymore. I think about this. ’Cause one thing, when you do this, companies seem very trivial. O.K.? I really mean that. They seem very trivial. But I have no income from Russia. I don’t do business with Russia. The gentleman that you mentioned, with his son, two nice people. But basically, they brought the Miss Universe pageant to Russia to open up, you know, one of their jobs. Perhaps the convention center where it was held. It was a nice evening, and I left. I left, you know, I left Moscow. It wasn’t Moscow, it was outside of Moscow.
Technically, Trump was only asked about whether he’d consider Mueller’s review of finances unrelated to Russia to be outside his lane. But Trump largely answered it about Russia, about business deals — the condos, the pageant — with Russia going back to the time Mueller’s FBI would have been working with Felix Sater to learn about the Russian mob.
Yeah. It’s no surprise Mueller has impaneled a grand jury.