How the Government Uses Location Data from Mobile Apps
 The other day I looked at an exchange between Ron Wyden and Jim Comey that took place in January 2014, as well as the response FBI gave Wyden afterwards. I want to return to the reason I was originally interested in the exchange: because it reveals that FBI, in addition to obtaining cell location data directly from a phone company or a Stingray, will sometimes get location data from a mobile app provider.
The other day I looked at an exchange between Ron Wyden and Jim Comey that took place in January 2014, as well as the response FBI gave Wyden afterwards. I want to return to the reason I was originally interested in the exchange: because it reveals that FBI, in addition to obtaining cell location data directly from a phone company or a Stingray, will sometimes get location data from a mobile app provider.
I asked Magistrate Judge Stephen Smith from Houston whether he had seen any such requests — he’s one of a group of magistrates who have pushed for more transparency on these issues. He explained he had had several hybrid pen/trap/2703(d) requests for location and other data targeting WhatsApp accounts. And he had one fugitive probation violation case where the government asked for the location data of those in contact with the fugitive’s Snapchat account, based on the logic that he might be hiding out with one of the people who had interacted with him on Snapchat. The providers would basically be asked to to turn over the cell site location information they had obtained from the users’ phone along with other metadata about those interactions. To be clear, this is not location data the app provider generates, it would be the location data the phone company generates, which the app accesses in the normal course of operation.
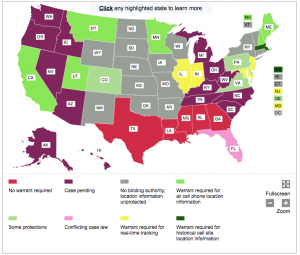
The point of getting location data like this is not to evade standards for a particular jurisdiction on CSLI. Smith explained, “The FBI apparently considers CSLI from smart phone apps the same as CSLI from the phone companies, so the same legal authorities apply to both, the only difference being that the ‘target device’ identifier is a WhatsApp/Snapchat account number instead of a phone number.” So in jurisdictions where you can get location data with an order, that’s what it takes, in jurisdictions where you need a probable cause warrant, that’s what it will take. The map above, which ACLU makes a great effort to keep up to date here, shows how jurisdictions differ on the standards for retrospective and prospective location information, which is what (as far as we know) will dictate what it would take to get, say, CSLI data tied to WhatsApp interactions.
Rather than serving as a way to get around legal standards, the reason to get CSLI from the app provider rather than the phone company that originally produces it is to get location data from both sides of a conversation, rather than just the target phone. That is, the app provides valuable context to the location data that you wouldn’t get just from the target’s cell location data.
The fact that the government is getting location data from mobile app providers — and the fact that they comply with the same standard for CSLI obtained from phones in any given jurisdiction — may help to explain a puzzle some have been pondering for the last week or so: why Facebook’s transparency report shows a big spike in wiretap warrants last year.
[T]he latest government requests report from Facebook revealed an unexpected and dramatic rise in real-time interceptions, or wiretaps. In the first six months of 2015, US law enforcement agencies sent Facebook 201 wiretap requests (referred to as “Title III” in the report) for 279 users or accounts. In all of 2014, on the other hand, Facebook only received 9 requests for 16 users or accounts.
Based on my understanding of what is required, this access of location data via WhatsApp should appear in several different categories of Facebook’s transparency report, including 2703(d), trap and trace, emergency request, and search warrant. That may include wiretap warrants, because this is, after all, prospective interception, and not just of the target, but also of the people with whom the target communicates. That may be why Facebook told Motherboard “we are not able to speculate about the types of legal process law enforcement chooses to serve,” because it really would vary from jurisdiction to jurisdiction and possibly even judge to judge.
In any case, we can be sure such requests are happening both on the criminal and the intelligence side, and perhaps most productively under PRISM (which could capture foreign to domestic communications at a much lower standard of review). Which, again, is why any legislation covering location data should cover the act of obtaining location data, whether via the phone company, a Stingray, or a mobile app provider.

what is john the butcher brennan’s ugly mug doing in public these days?
and feinstein muttering in her moustache?
and retired generals earning their keep by telling teeveeland WHY IT HAPPENED.
could this be a massive effort in misdirection, in “hey, look over there.”
the surveillers and their very expensive, very intrusive surveillance technology have failed us again !!
yes ! failed again ! and miserably.
failed for the umpteenth time.
so what has been the response of those architects and operators who built and use and ever madly applaud this never-failsafe spying machinery?
has it been to say “we really need to do better”? to acknowledge that the current approach never has worked as they promised us it would? to say, at least, “we’ve got to do better”?
why no. their approach has been as childish as a responsible adult can be:
– it’s eddie’s fault.
– it’s that cursed play station toy
– it’s what those assholes in congress took away from us in spying authority
– it’s those super-sneaky terrorist cells hiding in plain sight and communicating with each other while walking down a boulevarde holding hands.
impressive.
does this comment seem completely at odds with the subject of this column of ew’s?
well, that’s because it is.
i got tangled up with all the new columns showing up today and hit the comment key here instead of the comment key here:
https://www.emptywheel.net/2015/11/20/10-goodies-usa-freedom-act-gives-the-intelligence-community/
that’s where this comment belongs – assuming it belongs anywhere :)
“it’s somebody else’s fault; our fabulous, elephantine technology could never fail on its own.”
well, some folks are watching these slippery bastards closely:
http://america.aljazeera.com/articles/2015/11/20/post-paris-calls-for-expanded-surveillance-fall-flat.html
here is what the nytimes said:
http://www.nytimes.com/2015/11/18/opinion/mass-surveillance-isnt-the-answer-to-fighting-terrorism.html?_r=2
the times misses the key point entirely;
this is a calculated misdirection campaign by brennan and gang.
it is always a mistake when arguing with surveillance/natsec thugs like brennan and baker or rightwing operatives to begin by trying to rebut their claims.
the proper place to begin any arguement is not on their terms (did we lose capability by limiting surveillance law) but by noting that theirs is a calculated media misdirection campaign made necessary because massive surveillance manifestly failed, as it has always failed, to detect the paris attack in advance. hence, before that failure can become a topic of public discussion, these guys start a “if only you hadn’t taken our powers away backfire.
of course glenn greenwald understood what brennan and gang were up to in their rush to infect the public discourse (“eddie did it, etc), though i dont know that greenwald would term it a misdirection gambit:
https://theintercept.com/2015/11/15/exploiting-emotions-about-paris-to-blame-snowden-distract-from-actual-culprits-who-empowered-isis/
it’s the history in greenwald’s article thst is so enlightening.
based on greenwald’s history, i’d say fbi director james “big scare” comey learned his scare mongering and territory grabbing from louie freeh. who would have guessed?