FBI Caught Their ISIS Hacker by Tracking His Signed Email to His Signed Facebook and Twitter Accounts
The FBI just charged an Albanian hacker living in Malaysia, Ardit Ferizi, aka Th3Dir3ctorY, with stealing the Personally Identifiable Information of over 1,000 service members and subsequently posting that PII online to encourage people to target them (he provided the data to, among others, Junaid Hussain, who was subsequently killed in a drone strike).
Given Jim Comey’s repeated warnings of how the FBI is going dark on ISIS organizing, I thought I’d look at how FBI found this guy.
- Ardit Ferizi, the suspect’s real name, was connected to the @Th3Dir3ctorY account on Twitter. On that account Ferizi linked to an article about the Kosova Hacker’s Security group (KHS) for which he had been interviewed. He also identified himself as the owner of KHS.
- Ferizi registered the Twitter identity to a hotmail account tied to an IP address in Kosovo.
- @Th3Dir3ctorY subsequently logged into Twitter from various ISPs in Malaysia, including 210.186.111.14.
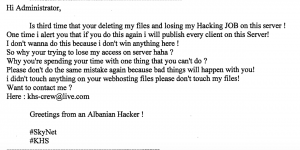
- The hacker who first broke into “Victim Company” on June 13, 2015 and ultimately stole the data of 100,000 people created an account with the identity KHS. On August 19, 2015 — after the company had removed the malware used to exfiltrate the data — someone identifying himself as “Albanian Hacker” and using the email “khs-crew@live.com” contacted the company and asked them to stop taking down their files (which the FBI interpreted to mean the malware left on the server). The IP address tied to the SQL injection used by the hacker was 210.186.111.14.
- A Facebook account tied to the name “ardit.ferizi01” also used that IP address. Ferizi sent himself a spreadsheet via that facebook account with the stolen PII.
In other words, Ferizi apparently did nothing to hide the association between his public Twitter boasting about stealing PII and association with KHS and the hack, down to his repeated email nudges to the victim company (and his attempt to get 2 Bitcoins to stop hacking them). His Twitter account, Facebook account, and email account could all be easily correlated both through IP and name, and activity on all three inculpated him in the hack.
The only mention of any security in the complaint is that Bitcoin account.
Sure, Ferizi was not playing the role of formal recruiter here, but instead agent provocateur and hacker. Still! The FBI is billing this guy as a hacker. And he did less to protect his identity then I sometimes use.
At least in this case, FBI isn’t going dark on ISIS’ attempts to incite attacks on Americans.

“The Office of the Inspector General (OIG) initiated this investigation based on a referral from the employing division of a Department of Justice (Department) attorney. According to the division, the attorney’s time and attendance at work for approximately five months were unaccounted for, both by the attorney’s assigned division and by another Department component to which the attorney had been temporarily assigned. The OIG determined that for a period of months during which the attorney was receiving full salary and benefits, the attorney was not present at work, did not complete any work-related functions, and was not on approved leave. Prosecution was declined. The Department and the attorney reached a settlement. Although the attorney did not admit liability, the attorney agreed to resign Department employment, forfeit the annual leave that had accrued during the period for which time and attendance was unaccounted, and repay a sum of money to the Department.
.
OhMyGod. Everyone’s Dream, taken down. Bastards.
The guy was asking to be busted. All of that identifying information online, and he didn’t think anyone could see it?
And the FBI thinks they did a great job of tracking him? Who did they ask for help?
He also set up an account on the retailer’s server using the username for Kosovo Hackers Security.
http://www.databreaches.net/wp-content/uploads/ferizi_complaint_final.pdf
Yup. That’s what I meant by this language: “created an account with the identity KHS.”
hacker, loz, you mean script kiddie.