Between Two Ends of the WikiLeaks Investigation: Parallel Constructing the FBI’s Secret Authorities
Two pieces of news on the government’s investigation of WikIleaks came out yesterday.
At the Intercept, Glenn Greenwald reported:
- In 2010, a “Manhunting Timeline” described efforts to get another country to prosecute what it called the “rogue” website
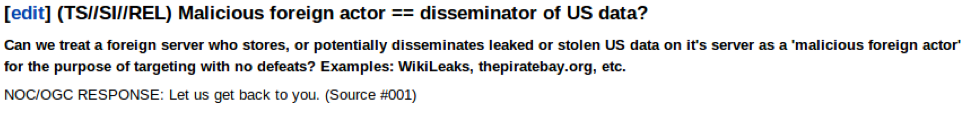
- In a targeting scenario dating to July 25, 2011, the US’ Targeting and General Counsel personnel responded to a question about targeting WikiLeaks’ or Pirate Bay’s server by saying they’d have to get back to the questioner
- In 2012, GCHQ monitored WikiLeaks — including its US readers — to demonstrate the power of its ANTICRISIS GIRL initiative
Also yesterday, Alexa O’Brien reported (and contextualized with links back to her earlier extensive reporting):
- The grand jury investigation of WikiLeaks started at least as early as September 23, 2010
- On January 4, 2011 (21 days after the December 14, 201 administrative subpoena for Twitter records on Appelbaum and others), DOJ requested Jacob Appelbaum’s Gmail records
- On April 15, 2011, DOJ requested Jacob Appelbaum’s Sonic records
Now, as O’Brien lays out in her post, at various times during the investigation of WikiLeaks, it has been called a Computer Fraud and Abuse investigation, an Espionage investigation, and a terrorism investigation.
Which raises the question why, long after DOJ had deemed the WikiLeaks case a national security case that under either the terrorism or Espionage designation would grant them authority to use tools like National Security Letters, they were still using subpoenas that were getting challenged and noticed to Appelbaum? Why, if they were conducting an investigation that afforded them all the gagged orders they might want, were they issuing subpoenas that ultimately got challenged and exposed?
Before you answer “parallel construction,” lets reconsider something I’ve been mulling since the very first Edward Snowden disclosure: the secret authority DOJ and FBI (and potentially other agencies) used to investigate not just WikiLeaks, but also WikiLeaks’ supporters.
Back in June 2011, EPIC FOIAed DOJ and FBI (but not NSA) for records relating to the government’s investigation of WikiLeaks supporters.
EPIC’s FOIA asked for information designed to expose whether innocent readers and supporters of WikiLeaks had been swept up in the investigation. It asked for:
- All records regarding any individuals targeted for surveillance for support for or interest in WikiLeaks;
- All records regarding lists of names of individuals who have demonstrated support for or interest in WikiLeaks;
- All records of any agency communications with Internet and social media companies including, but not limited to Facebook and Google, regarding lists of individuals who have demonstrated, through advocacy or other means, support for or interest in WikiLeaks; and
- All records of any agency communications with financial services companies including, but not limited to Visa, MasterCard, and PayPal, regarding lists of individuals who have demonstrated, through monetary donations or other means, support or interest in WikiLeaks. [my emphasis]
In their motion for summary judgment last February, DOJ said a lot of interesting things about the records-but-not-lists they might or might not have and generally subsumed the entire request under an ongoing investigation FOIA exemption.
Most interesting, however, is in also claiming that some statute prevented them from turning these records over to EPIC, they refused to identify the statute they might have been using to investigate WikiLeaks’ supporters.
All three units at DOJ — as reflected in declarations from FBI’s David Hardy, National Security Division’s Mark Bradley, and Criminal Division’s John Cunningham – claimed the files at issue were protected by statute.
None named the statute in question. All three included some version of this statement, explaining they could only name the statute in their classified declarations.
The FBI has determined that an Exemption 3 statute applies and protects responsive information from the pending investigative files from disclosure. However, to disclose which statute or further discuss its application publicly would undermine interests protected by Exemption 7(A), as well as by the withholding statute. I have further discussed this exemption in my in camera, ex parte declaration, which is being submitted to the Court simultaneously with this declaration
In fact, it appears the only reason that Cunningham submitted a sealed declaration was to explain his Exemption 3 invocation.
And then, as if DOJ didn’t trust the Court to keep sealed declarations secret, it added this plaintive request in the motion itself.
Defendants respectfully request that the Court not identify the Exemption 3 statute(s) at issue, or reveal any of the other information provided in Defendants’ ex parte and in camera submissions.
DOJ refuses to reveal precisely what EPIC seems to be seeking: what kind of secret laws it is using to investigate innocent supporters of WikiLeaks.
Invoking a statutory exemption but refusing to identify the statute was, as far as I’ve been able to learn, unprecedented in FOIA litigation.
The case is still languishing at the DC District.
I suggested at the time that the statute in question was likely Section 215; I suspected at the time they refused to identify Section 215 because they didn’t want to reveal what Edward Snowden revealed for them four months later: that the government uses Section 215 for bulk collection.
While they may well have used Section 215 (particularly to collect records, if they did collect them, from Visa, MasterCard, and PayPal — but note FBI, not NSA, would have wielded the Section 215 orders in that case), they couldn’t have used the NSA phone dragnet to identify supporters unless they got the FISC to approve WikiLeaks as an associate of al Qaeda (update: Or got someone at NSA’s OGC to claim there were reasons to believe WikiLeaks was associated with al Qaeda). They could, however, have used Section 215 to create their own little mini WikiLeaks dragnet.
For the same reason, they could not have used the PR/TT-authorized Internet dragnet to identify those who might have communicated with Assange or Bradley Manning Support Group members (though by this point they already had David House’s computer with a membership list of the latter on it). The domestic Internet dragnet was operational, after having been shut down already, between at least October 2010 until the end of 2011. But it, like the Section 215 dragnet, was apparently limited to terrorist identifiers.
Finally, we know under Special Procedures (SPCMA) approved in 2008 and piloted in 2009, NSA claimed the authority to track which Americans were in contact with foreign targets like Julian Assange, using communications data collected somewhere offshore. Significantly, there is no restriction to terrorism uses for SPCMA; analysts need only cite a foreign intelligence purpose. In an Espionage investigation of WikiLeaks after the adoption of SPCMA, all US person metadata collected internationally off the WikiLeaks server would have been fair game (though NSA would have to comply with dissemination limitations).
There is no authority permitting this SPCMA collection. NSA and DOD and DOJ simply claimed it under Article II. If that’s what they’re using to investigate WikiLeaks’ supporters, I can imagine why DOJ wouldn’t want to reveal that in a public filing in a FOIA case!
Particularly given the way at least two providers challenged either the gags or these criminal subpoenas themselves, there is zero reason to believe DOJ was doing anything other than providing some other claimed source for the evidence they wanted to submit to the grand jury (though there are some interesting NSLs that got challenged by various service providers in that same 2011 time frame, including the presumed Credo one).
So there are 3 details about the US investigation into WikiLeaks during 2011 of interest:
- By June 2011, they were using an authority to conduct such an investigation that they refuse to disclose
- They were, through that very same period, issuing criminal subpoenas that providers were challenging
- NSA refused to say, in writing and after that EPIC FOIA was filed, whether analysts could incidentally collect US person communications to the WikiLeaks server based on a claim it was a malicious actor
Given all that the government has declassified — including references to SPCMA — I wonder if DOJ would now be willing to tell EPIC what statute — or lack thereof — it is hiding behind.
Updated: Changed reference to O’Brien’s reporting because it said the opposite of what I intended to say.


Now wait a minute here …. If I’m following this correctly (which would be quite an achievement, I must admit), then what the hell happens to the “if you’ve got nothing to hide, you’ve got nothing to fear” justification?
with the use of nsa to support a whistleblower of great importance to the american and world’s public, there can be no doubt that governmental/prosecutorial vindictiveness and ruthless will guarantee that the electronic spying powers of the nsa will be turned on any individual or organization which reveals secrets of or even embarasses the u.s. government including american citizens.
furthermore, the use of the british electronic spying agency gchq to “supplement” u.s. government spying/investigation greatly increases the reach of the nsa to illegally investigate american citizens. citizens of other countries, e.g., julian assange, will have virtually no protection.
bottom line: seriously challenging the actvities or policies of the u.s. government will not be tolerated in today’s washington.
The time has finally arrived to strip away all the obfuscations, lies, and double-talk used by state actors at the DOJ, FBI, and NSA. Some of their lawyers write and talk as if they were tutored by Carl Schmitt while reading after-hours manuals issued by the KGB, Stasi, and Gestapo. Increasingly, I view 9/11 as a Reichstag Fire event being used by the deep state to impose a fascist web of control over the population. Under the emerging New World Order democracy will become a meaningless spectator sport (think Hunger Games).
To the litany of secret courts, secret laws and secret court orders, we now add the oddity of public laws (or, as we used to call them, laws) whose use has to be kept secret. I can’t say I’m surprised.
kinda/maybe related: when i got the notice from Kickstarter that their database had been hacked but no credit card info taken, i figured some security state actor was trolling for info on supporters of projects that had piqued their interest.
@Saul Tannenbaum: Well, if it’s SPCMA, it’s not public, or only barely right now (and not so much a law as an authority).
If it’s 215, then your point definitely holds.
This is so fascinating to me because it hinges on the premise that the government has decided what rights it wants to seize and control and then hinder anyone from finding out, let alone explaining to congress what authority it has in doing so, how it assumes and controls these rights.
I use a litmus test of these seizures based on replacing the Fourth amendment with the Second. Imagine all of the default positions the government has assumed it has authority over, in secret, and then determines application of enforcement or compliance with these rights, that they have basically seized, if they related to ammunition or hand guns. I don’t think people of the average citizenry type have a grasp of just exactly how the government is saying they should be able to control, both inherently and thru behavior that fits their law enforcement needs the rights that should be latent at best.
@emptywheel: Well, SPMCA declares that, for the purposes of metadata chaining, Americans aren’t Americans. That lives in the strange rhetorical land of data that isn’t considered “collected” until someone wants to look at it.
Historians looking back at the processes by which our government decided this was all ok will treat these distinctions the same way we treat the medieval scholars who discussed how many angels can dance on the tip of a needle.
@Saul Tannenbaum:
yes, the analogy with scholastic argumentation keeps occurring to me. in this case we’re talking about doj-sanctioned legal scholasticism – in the furtherance of those who hold the levers of u.s. power maintaining that power and doing with it what they damn well please.
In one of the best sci-fi novels ever written it describes, “The cycles of civilization, war, and collapse have apparently been repeating for hundreds of thousands of years.”
http://en.wikipedia.org/wiki/The_Mote_in_God%27s_Eye
I often wonder with humanity’s apparent capacity for stupidity whether we are doomed perpetual cycles of war.
The rise of empire, after corrupted-and-collapsed empire, always built around exceptional-ism of the few, and destined to fail for that very reason, is not a history to be proud of.
Apologies for the whimsy.
It’s this bit of the story which intrigues me the most:
An NSA file titled “Manhunting Timeline” from 2010 described the maneuvers of the US as it sought to coordinate an “international effort to focus the legal element of national power upon non-state actor Assange, and the human network that supports WikiLeaks.” In August 2010, the US government pressed 10 other countries to level criminal charges against Assange, describing him as “founder of the rogue WikiLeaks internet website and responsible for the unauthorized publication of over 70,000 classified documents covering the war in Afghanistan.”
http://www.wsws.org/en/articles/2014/02/19/wiki-f19.html
What’s the betting that one of those 10 countries was Sweden? I found this 6th August 2010 article, in which the head of the Swedish Foreign Policy Institute describes US discussions with Swedish intel agencies about shutting down the Wikileaks site, possibly with a “raid on their premises” if they were based in Sweden (a few days later Assange headed to Sweden to organise just that):
http://www.dn.se/nyheter/sverige/usa-expert-sveriges-roll-diskuteras-pa-toppniva/
(Google translate required)
@Greg Bean (@GregLBean): If I had to name a single point defect in Western modernity, it was the Treaties of Westphalia granting sovereigns a right to rule that is not subordinate in any way to their subjects.
@Jonathan: Good point, though, as indicated, limited to the West.
It seems to me that strengthening the UN Charter of Human Rights, which has existed for over 60 years, especially removing ANY exception by country, state, corporation or organization, religions included, could begin to address the primary rights of individuals.
But that would undermine the existing power structures, so it is no wonder it has been so sparsely implemented and where it has that so many exceptions have been granted.
@orionATL:
correction:
“with the use of the nsa to support u.s. government suppression of…”
in place of
“with the use of nsa to support a whistleblower of great importance…”
@Greg Bean (@GregLBean): A swastika intertwining a star of david symbolizes the cyclic nature of everything, including stupid “perpetual cycles of war”.
Our humanity is running out of time to overcome its primitive aggression towards each-other and our environment, unfortunately the industrial military complex seems intent on starting it.
The above mentioned symbol is on Elohim spacecraft and seen, in parts, all over the ancient world and here http://www.rael.org/home
A thought about that Wall Street Journal piece – NSA Weighs Retaining Data for Suits (http://online.wsj.com/news/articles/SB10001424052702303636404579393413176249186).
They report that:
“As the NSA program currently works, the database holds about five years of data, according to officials and some declassified court opinions. About twice a year, any call record more than five years old is purged from the system, officials said.”
I’m betting that this 5 year rolling purge is only occurring in the primary MAINWAY telephony metadata collection database, and that all of the telephony metadata that results from NSA’s 1-3 hop queries that winds up in the “corporate store” is never purged of any data regardless of whether it is 5 years old or older.
@Snoopdido: NSA/DOJ have never mentioned anything about the corporate store data being purged, so most of us assume it is not.
@Rosalind: that has happened a number of places over the past few years, and I agree
“There is no authority permitting this SPCMA collection. NSA and DOD and DOJ simply claimed it under Article II. If that’s what they’re using to investigate WikiLeaks’ supporters, I can imagine why DOJ wouldn’t want to reveal that in a public filing in a FOIA case!”
I’m a little confused. They did specifically say they claimed an exemption based on a statute, right? If they were using Article II, would they have a statute to cite? Sorry if this is a dumb question. Law is not my specialty.