The Schulte CIPA Transcripts: Locking up Vault 8
Perhaps the most interesting thing about the CIPA (Classified Information Procedures Act) transcripts from the Josh Schulte case that Kel McClanahan helped me liberate is that (at least in 2022, when they did a classification review) the CIA treated the moniker “Vault 8” that WikiLeaks gave to the CIA source code releases as still-classified.
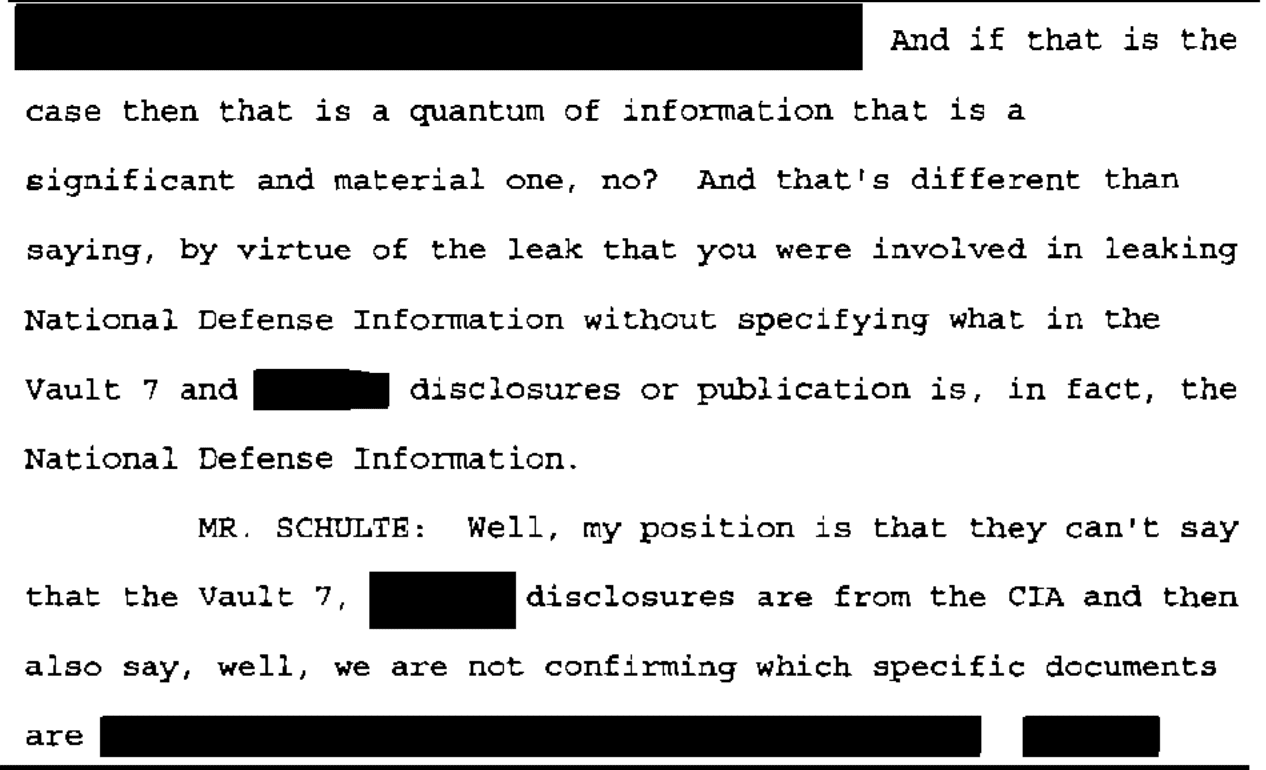
When Judge Jesse Furman restated the hypothetical he posed about whether disseminating already-released stolen classified information could itself be a crime, he described the releases to include Vault 7 and Vault 8.
I gave you two hypotheticals. I think one is where a member of the public goes on WikiLeaks today and downloads Vault 7 and Vault 8 and then provides the hard dive with the download to someone who is not authorized to receive NDI, and I posed the question of whether that person would be guilty of violating the Espionage Act and I think your answer was yes. [my emphasis]
There’s actually no unredacted reference to Vault 8 in the released transcripts.
But there are what are almost certainly redacted references to Vault 8.
Here’s how part of the discussion about hypotheticals appears in the May 2 transcript:
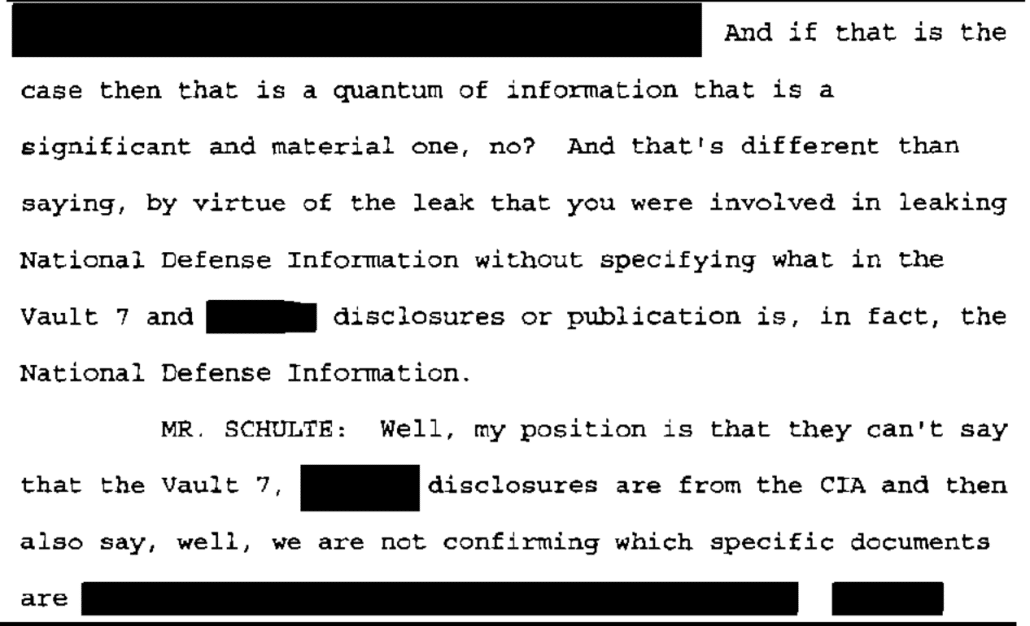
It appears likely that Josh Schulte was deliberately using both terms — he started doing so, and much later in the transcript he claimed, falsely, that there was a distinction in the charges against him between the development notes and the source code. The dual references, with repeated mention of Vault 7, followed immediately by a redaction describing the other of plural “disclosures,” appear to stop after page 31, perhaps in response to something one of the prosecutors said.
There’s undoubtedly good reason the government remains coy about the more damaging part of this release.
In a self-serving note sent after it became clear he was a suspect, Schulte himself made a clear distinction between the development notes and the source code, describing that, “These tools are MUCH more valuable [to a hostile country like Russia] undiscovered by the media or the nation that lost them [because] Now, you can secretly trace and discover every operation that nation is conducting.” The source code provided American adversaries the ability to reverse engineer US spying efforts, and in the process, identify CIA assets.
I have written about how Julian Assange seemed to threaten Don Jr by raising the separately named source code in November 2017.
Schulte’s apparent failed attempt to win the right to discuss the source code releases, in addition to the development note releases, came in the midst of his attempt to get more details from what was likely the ongoing investigation into the aftermath of his leak, including (possibly) how hackers obtained the tools he had leaked. Schulte received that discovery starting in early April, and on April 29, he asked Judge Furman to give him all the details of the ongoing investigation. Throughout his second trial, Schulte seemed focused on using his defense to communicate outward (which is one reason I found Wau Holland’s decision to pay for transcripts so notable). So in the hearing where he was attempting to include Vault 8 among the things he could discuss publicly, he was focused on the ongoing investigation into how hackers had obtained or used these tools.
I have long said that, historically, the files WikiLeaks chose not to release — and, potentially, to selectively share — were far more important than the files they released. The government’s ongoing sensitivity seems to confirm that: The US government has conceded that the development notes from CIA’s hacking tools, which constitutes the bulk of what WikiLeaks released, came from the CIA, but appears not to concede that the hacking source code itself does.





Again, thank you for your diligence.
Would the CIA’s protectiveness over Vault 8 have to do with not just with the source code of tools but because it discusses the Hive and how it operates?
Seems to me that the gov might consider the information about how the tools were remotely accessed and controlled to be even more important and destructive having that in the wild for targets to understand how those tools were manipulated.
And as Clare acknowledges, thank you for your, and Kel’s work on this.
I know this might sound self-righteous, but I decided, after Wikileaks released all those secrets, not to read any accounts of the contents of those leaks. I felt that I would be complicit in committing treason were I to do so. It sounds simplistic, but I simply felt I didn’t have the right to know certain things relating to the security of the US gov’t.
What I do have, as a US Citizen, is the right to vote for the people I trust will conduct themselves in an ethical manner as elected officials. I don’t need to know everything they do which might, on the surface, to an uninformed person, seem to be nefarious. It might be activity which borders on the immoral use of power, but I am in no position to judge; nor was Julian Assange and the news media which accepted and published that information. When countries are at war with each other, whether actively fighting or on the edge of such, anything is acceptable, unfortunately. The major crime is that human beings can do evil things, and people who do not have the intention of evil actions end up having to drop their moral underwear in order to survive.
In my ignorant (in this matter) mind, I choose to be ignorant. Julian Assange is a slimy, selfishly motivated man who pretends to be a virtuous “truth-teller.” He is, in fact, a thief who stole secrets to which he should not have been privy. He should spend the rest of his life in jail for it, as it apparently cost the lives of people doing their duty to our government.