NSA Returns to Stealing from Yahoo and Google
 The entire point of the Protect America Act and FISA Amendments Act was to provide a way for NSA to collect data from Yahoo and Google without stealing it from telecom switches, which is what they had been doing for 6 years. That was the primary goal: provide a legal means, with oversight, to collect intelligence from the multinational US-based Internet companies that dominated the free email market.
The entire point of the Protect America Act and FISA Amendments Act was to provide a way for NSA to collect data from Yahoo and Google without stealing it from telecom switches, which is what they had been doing for 6 years. That was the primary goal: provide a legal means, with oversight, to collect intelligence from the multinational US-based Internet companies that dominated the free email market.
Yet, as I’ve been predicting for weeks, that wasn’t good enough for NSA. In addition to all the intelligence they collect legally using PRISM under Section 702 authority, it turns out they’ve been busy returning to their thieving ways.
The National Security Agency has secretly broken into the main communications links that connect Yahoo and Google data centers around the world, according to documents obtained from former NSA contractor Edward Snowden and interviews with knowledgeable officials.
By tapping those links, the agency has positioned itself to collect at will from among hundreds of millions of user accounts, many of them belonging to Americans. The NSA does not keep everything it collects, but it keeps a lot.
According to a top secret accounting dated Jan. 9, 2013, NSA’s acquisitions directorate sends millions of records every day from Yahoo and Google internal networks to data warehouses at the agency’s Fort Meade headquarters. In the preceding 30 days, the report said, field collectors had processed and sent back 181,280,466 new records — ranging from “metadata,” which would indicate who sent or received e-mails and when, to content such as text, audio and video.
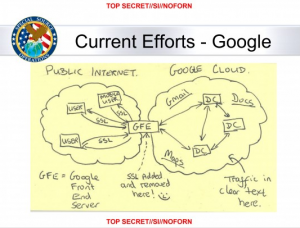
The NSA’s principal tool to exploit the data links is a project called MUSCULAR, operated jointly with the agency’s British counterpart, GCHQ. From undisclosed interception points, the NSA and GCHQ are copying entire data flows across fiber-optic cables that carry information between the data centers of the Silicon Valley giants.
Mind you, the apologists will say that breaking into Yahoo and Google’s internal clouds to steal this information isn’t stealing because it takes place overseas, and therefore doesn’t have to abide by FISA, and therefore just amounts to normal old spying.
Case in point:
Intercepting communications overseas has clear advantages for the NSA, with looser restrictions and less oversight. NSA documents about the effort refer directly to “full take,” “bulk access” and “high volume” operations on Yahoo and Google networks. Such large-scale collection of Internet content would be illegal in the United States, but the operations take place overseas, where the NSA is allowed to presume that anyone using a foreign data link is a foreigner.
Outside U.S. territory, statutory restrictions on surveillance seldom apply and the Foreign Intelligence Surveillance Court has no jurisdiction. Senate Intelligence Committee Chairwoman Dianne Feinstein has acknowledged that Congress conducts little oversight of intelligence-gathering under the presidential authority of Executive Order 12333 , which defines the basic powers and responsibilities of the intelligence agencies.
John Schindler, a former NSA chief analyst and frequent defender who teaches at the Naval War College, said it was obvious why the agency would prefer to avoid restrictions where it can.
“Look, NSA has platoons of lawyers and their entire job is figuring out how to stay within the law and maximize collection by exploiting every loophole,” he said. “It’s fair to say the rules are less restrictive under Executive Order 12333 than they are under FISA.”
But as I noted in this post, there’s at least an argument to be made that the 2011 John Bates decision ruling Section 702 upstream collection intentional and the existing FAA (that is, far more stringent than the 12333) minimization procedures insufficient under the Fourth Amendment would apply here, making the exposure of US person data under this collection a constitutional violation. And all that’s assuming there’s a purpose, like terrorism, that would warrant (heh) a special needs exception. With such bulk collection and nonexistent oversight, it’s not clear such a case could be made.
So stealing. And in the process doing enormous damage to two important American companies.
There’s one odd thing about this article though. Notice the absence of any discussion of Microsoft?