The Section 215 Dragnet Started as Abusive Exigent Letter Practice Wound Down
Julian Sanchez (who, if you’re not already following, you should, @normative) just made an important observation about the Section 215 collection that collects metadata on all phone calls every day.
Carriers keep call detail records for years. No earthly reason to demand DAILY updates just to preserve.
Thunk. The penny dropped.
In theory, no, there’s no reason to demand daily updates from the telecoms. In fact, in theory, you could always just ask the telecoms to conduct the kind of data analysis that is now being done by NSA.
But there’s a very good reason why they’re not doing it that way.
They tried. It was badly abused.
And they started moving away from that approach in March 2006, precisely when we know the Section 215 program started.
Most of what we know about the exigent letters program comes from a report DOJ’s Inspector General did in March 2007 [ed 6/16: oops–all this time I had the least damning report linked. read this one] (my posts are here, here, here, here, here, here, here). But the short version is that the NY FBI office set up an office to have representatives of the three major telecom companies come in and directly access their data with FBI Agents looking over their back. As such, it’s probably similar to what PRISM accomplishes for internet providers (except that an NSA employee rather than a telecom employee does the search), and presumably akin to whatever NSA does with the Section 215 dragnet information (which, after all, replicates the telecom databases perfectly).
The problems — that that we know about from the unclassified report (there are secret and TS/SCI versions which probably have bigger horrors) — include:
- FBI General Counsel had no apparent knowledge of 17% of the searches
- Thousands of searches never got recorded
- FBI lied to the telecoms about how urgent the information was to get the information
- FBI did an unknown number of sneak peeks into the data to see if there was something worth getting formally
Altogether, the unclassified IG Report described 26 abuses that should have been reported to then (and once again, since Chuck Hagel became Defense Secretary) inoperable Intelligence Oversight Board.
That includes the tracking of journalist call records in at least three cases (one of which I suspect is James Risen).
In short, it violated many legal principles. And that’s just the stuff that actually got recorded and showed up in an unclassified report.
The Executive spent years trying to clean up the legal mess, with four OLC opinions between November 8, 2008 and January 8, 2010 making one after another argument to justify the mess.
And just as it became clear what a godforsaken mess all this was in March 2006, they started using Section 215 to collect all call records.
The effectively created the same databases that had been abused when the FBI had telecom employees doing the work, to have NSA or FBI do the very same work as well.
In short, the reason we don’t do what Sanchez is absolutely right we should do — ask the telecoms for information as we need it — is it’s not easy enough.
What I look forward to learning, though, is how having government employees do the work that telecom employees — who at least were bound by ECPA — avoids the same kind of abusive fishing expeditions.
Update: Here’s a description I wrote to summarize this 3 years ago.
This IG Report was the third DOJ’s Inspector General, Glenn Fine, has done on the FBI’s use of National Security Letters and “exigent letters,” though this is the first to focus almost exclusively on exigent letters. In 2003, the FBI installed representatives of AT&T and (later) Verizon and MCI onsite, with computers hooked up to their respective companies’ databases. Rather than using a subpoena or a National Security Letter to get phone records from them (both of which would have required a higher level of review), the FBI basically gave them a boilerplate letters saying it was an emergency (thus the “exigent”) and could they please give the FBI the phone data; the FBI promised grand jury subpoenas to follow. Only, in many cases, these weren’t emergencies, they never sent the grand jury subpoenas, and many weren’t even associated with investigations into international terrorism. In other words, FBI massively abused this system to get phone data without necessary oversight. Fine has been pressing FBI to either establish some legal basis for getting this data or purging it from FBI databases for three years, and they have done that with some, but not all, of the data collected. But the FBI has tried about three different ways to bring this practice into conformity with legal guidelines, all unpersuasive to Fine. The OLC opinion is the most recent of these efforts.
Also, here’s a timeline.

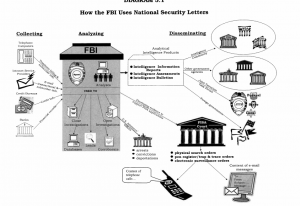
It would also be interesting to know why they’re using contractors to do the work, since it’s so important and Super-Duper Triple Top Secret.
Emptywheel wrote:
“What I look forward to learning, though, is how having government employees do the work that telecom employees — who at least were bound by ECPA — avoids the same kind of abusive fishing expeditions.”
All three branches of the US government would argue that by having government employees do the snooping, it would prevent abuse because government employees take an oath and pledge to respect the law, honor the Constitution, and never ever do bad things.
The fallacy of this naiveté, or political smoke blowing up one’s ass if you prefer, is that for all the US government’s key-logging, polygraph testing, and other Big Brother oversight processes, there is no there there. It’s like believing in Santa Claus. A fairy tale one tells children.
If the US government keeps it all in house (ignoring inconvenient facts like that private contractors form a large part of the intelligence community’s workforce), then nobody outside of the US government will ever know what they are doing. Secrecy is maintained so they would argue.
If it also just happens to allow US government employees themselves to poke around on fishing expeditions where leaving the data in the hands of private corporations would mean always having to go through cumbersome legal processes to get the corporations to do the requested fishing, that too is just fine.
The mindset is that private corporations at best are seen as reluctant allies, but you can never really trust anyone who isn’t officially on your team. See Edward Snowden.
If anyone is wondering how the US government can fob off the blame for Snowden’s leaks on the use private corporations while gladly outsourcing the US government’s work to those same private corporations, welcome to the world of government where holding multiple contradictory and opposing ideas at the very same time is a prerequisite of employment.
@P J Evans: Contractors do everything. Remember the suicide bomber who took out seven major CIA people in Afghanistan? Two were Blackwater. Read Hillhouse.
What I’ve never seen claimed is that the NSA wants to collect and cross-correlate network intrusion data from all of the companies’ public-facing Internet bandwidth. This is a very defensible need- why aren’t they talking it up?
@Morris Minor: Because they want to pretend this is only about terrorism. Once they admit (which they have, already, but still) that it’s about hackers the claims about become clearly false.
Insanity thy name is national security!
Its beginning to look as if this whole, towering national security evesdropping ediface was unnecessary.
So why build it?
well, the building of it implies that the fbi/cia/hsa were implicitly deemed incompetent to identify terrorists and stop terrorism.
Or the ediface was really built on a “terrorism” foundation but intended to be used against hackers.
But what kind of hackers?
Those that would steal money from my credit card or bank account or steal my id’s?
Or was it really pointed at hackers who could steal government secrets?
If the later, that whole, towering ediface was built for the benefit of some government agencies, officials, and politicians in office,
Not for the benefit of the nation or its citizens.
which might explain why, despite the expense and unconstitutionality and deceit required to build that ediface,
We ended up with a bombing of one of our national celebratory events, the boston marathon,
And why we are likely to experience occassional similar others in the future.
Old washington bureaucrats, university administrators, and corporate leaders have known for decades and decades that any putative threat to “national security”, can readily be turned to their organization’s or their personal advantage.
Oh, look at that timeline. It kicks of in 2003!
What happened then you may ask?
Well only the Total Information Awareness program getting defunded…